Laura Ingrahams Viral Clash With Trump Prompts Her To Tell Real Reasons China Sends Students To US – The Daily Caller
Published on: 2025-11-13
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Laura Ingrahams Viral Clash With Trump Prompts Her To Tell Real Reasons China Sends Students To US – The Daily Caller
1. BLUF (Bottom Line Up Front)
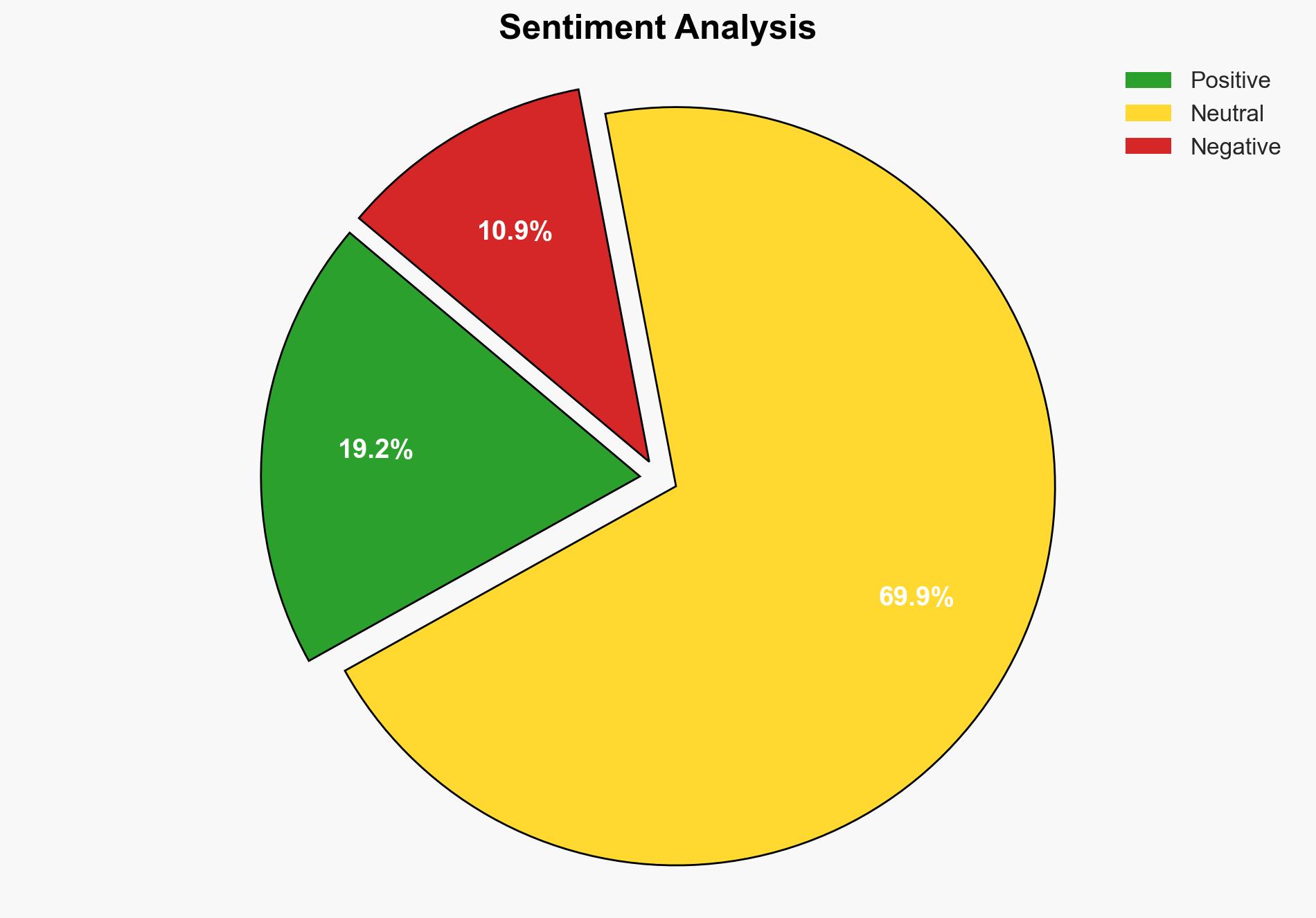
There is a strategic concern regarding the presence of Chinese students in American universities, with implications for national security. The most supported hypothesis is that China uses student placements as a means of intelligence gathering and influence. Confidence Level: Moderate. Recommended action includes enhancing vetting processes and increasing awareness of potential espionage activities.
2. Competing Hypotheses
Hypothesis 1: China sends students to the US primarily for educational purposes, with the secondary benefit of cultural exchange and soft power influence. This hypothesis suggests that the majority of students are genuine in their academic pursuits, and any intelligence activities are incidental.
Hypothesis 2: China strategically sends students to the US as part of a broader intelligence-gathering and influence operation. This hypothesis posits that the Chinese Communist Party (CCP) uses students to access sensitive information and technologies, and to influence academic and political narratives.
Hypothesis 2 is more likely given historical precedents of espionage and the CCP’s documented interest in leveraging all available resources for intelligence purposes.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that the CCP has significant control over Chinese nationals abroad and that students are susceptible to state influence. It is also assumed that US universities lack comprehensive measures to counter espionage.
Red Flags: The large number of Chinese students in sensitive fields, reports of espionage activities linked to academic institutions, and the CCP’s known use of non-traditional collectors.
Deception Indicators: Public statements by Chinese officials downplaying espionage concerns, and efforts to frame student exchanges solely as cultural and educational.
4. Implications and Strategic Risks
The presence of Chinese students in American universities poses potential risks including intellectual property theft, influence operations, and the erosion of academic integrity. Politically, this could strain US-China relations and lead to increased scrutiny of Chinese nationals. Economically, it could affect university funding models reliant on international tuition. Informationally, it risks the spread of CCP-aligned narratives within academic circles.
5. Recommendations and Outlook
- Enhance vetting processes for international students, particularly in sensitive fields.
- Increase awareness and training for university staff on identifying and reporting suspicious activities.
- Foster international collaboration on academic integrity and espionage prevention.
- Best-case scenario: Improved security measures mitigate espionage risks without harming educational exchange.
- Worst-case scenario: Escalation of tensions leads to a significant reduction in international academic collaboration.
- Most-likely scenario: Incremental policy adjustments lead to a balanced approach, addressing security concerns while maintaining educational ties.
6. Key Individuals and Entities
Laura Ingraham, President Donald Trump, Chinese Communist Party (CCP).
7. Thematic Tags
National Security Threats
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map relationships between state and non-state actors for impact estimation.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Methodology