SAP Pushes Emergency Patch for 99 Rated CVE-2025-42887 After Full Takeover Risk – HackRead
Published on: 2025-11-13
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: SAP Pushes Emergency Patch for 99 Rated CVE-2025-42887 After Full Takeover Risk – HackRead
1. BLUF (Bottom Line Up Front)
The discovery of the CVE-2025-42887 vulnerability in SAP systems poses a critical risk of full system takeover by cyber attackers. The most supported hypothesis is that the vulnerability was a result of oversight in SAP’s security protocols, rather than a deliberate act of sabotage. Organizations using SAP systems must urgently apply the emergency patch to mitigate the risk. Confidence Level: High.
2. Competing Hypotheses
Hypothesis 1: The vulnerability in SAP systems was due to an oversight in security protocols during software development and updates.
Hypothesis 2: The vulnerability was introduced intentionally by an insider or external actor with the aim of exploiting SAP systems for malicious purposes.
Hypothesis 1 is more likely given the complexity of SAP systems and the common occurrence of such vulnerabilities in large software platforms. There is no direct evidence suggesting insider sabotage or external tampering at this time.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that SAP’s security protocols were followed during the development of the affected component. It is also assumed that the vulnerability was not exploited before the patch release.
Red Flags: The high severity rating of the vulnerability and the potential for complete system takeover are significant red flags. The rapid release of a patch indicates the urgency and seriousness of the threat.
Deception Indicators: There are no clear indicators of deception at this stage, but the possibility of insider involvement cannot be entirely ruled out without further investigation.
4. Implications and Strategic Risks
The vulnerability presents several strategic risks, including potential data breaches, financial loss, and operational disruptions for businesses relying on SAP systems. If exploited, it could lead to cascading effects such as loss of customer trust, regulatory penalties, and increased cybersecurity insurance costs. Politically, it could strain relations between affected companies and their stakeholders.
5. Recommendations and Outlook
- Organizations using SAP systems should immediately apply the emergency patch to mitigate the risk of exploitation.
- Conduct a thorough security audit of SAP systems to identify any other potential vulnerabilities.
- Enhance monitoring and incident response capabilities to detect and respond to any exploitation attempts swiftly.
- Best-case scenario: The patch is applied universally, preventing any exploitation of the vulnerability.
- Worst-case scenario: The vulnerability is exploited before patches are applied, leading to significant data breaches and operational disruptions.
- Most-likely scenario: Most organizations apply the patch in a timely manner, minimizing the impact of the vulnerability.
6. Key Individuals and Entities
Joris van de Vis, Director of Security Research at SecurityBridge.
7. Thematic Tags
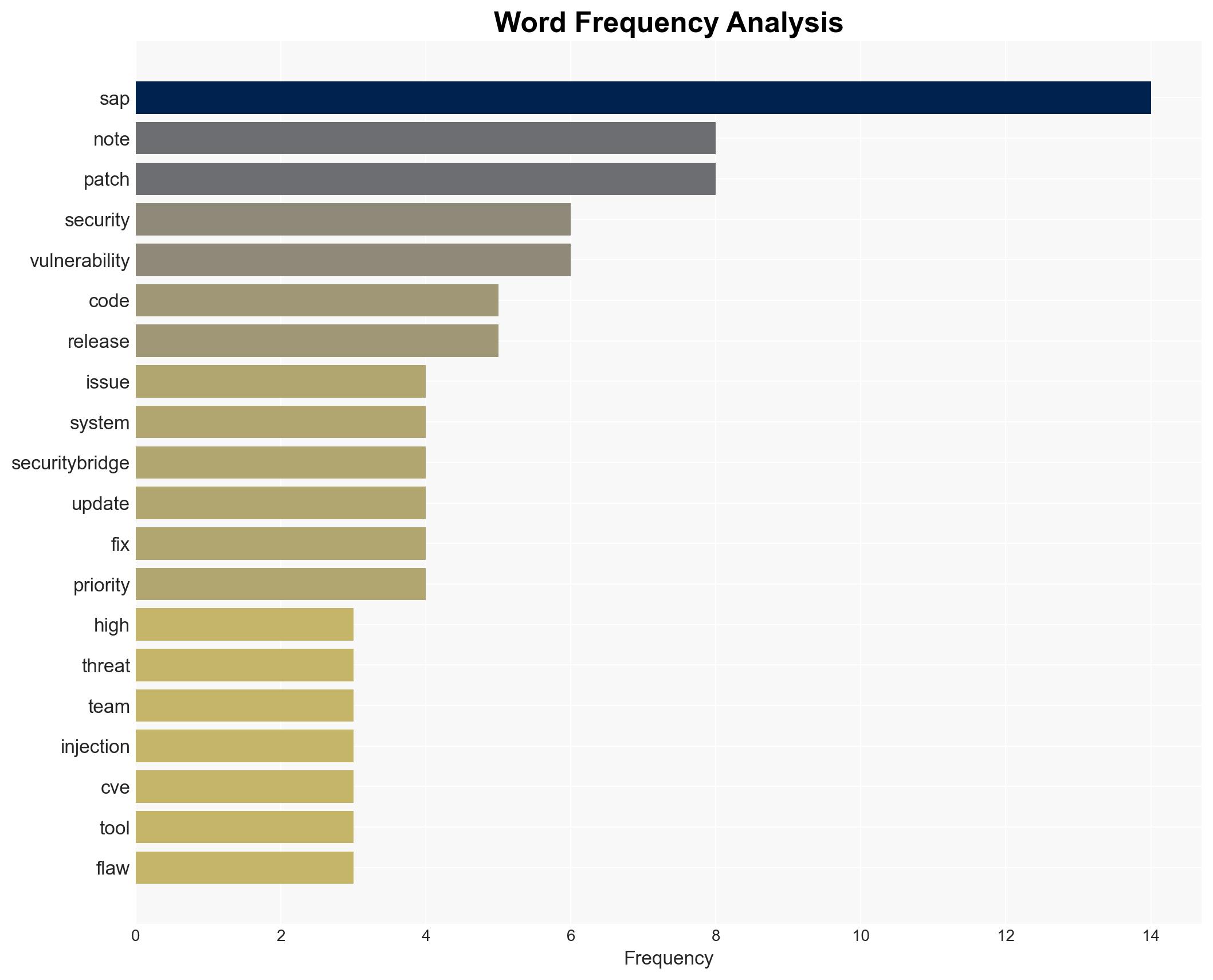
Cybersecurity
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Methodology