JetBrains TeamCity 2023114 Vulnerability Allows Authentication Bypass Exploitation
Published on: 2025-08-11
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: webapps JetBrains TeamCity 2023114 – Authentication Bypass
1. BLUF (Bottom Line Up Front)
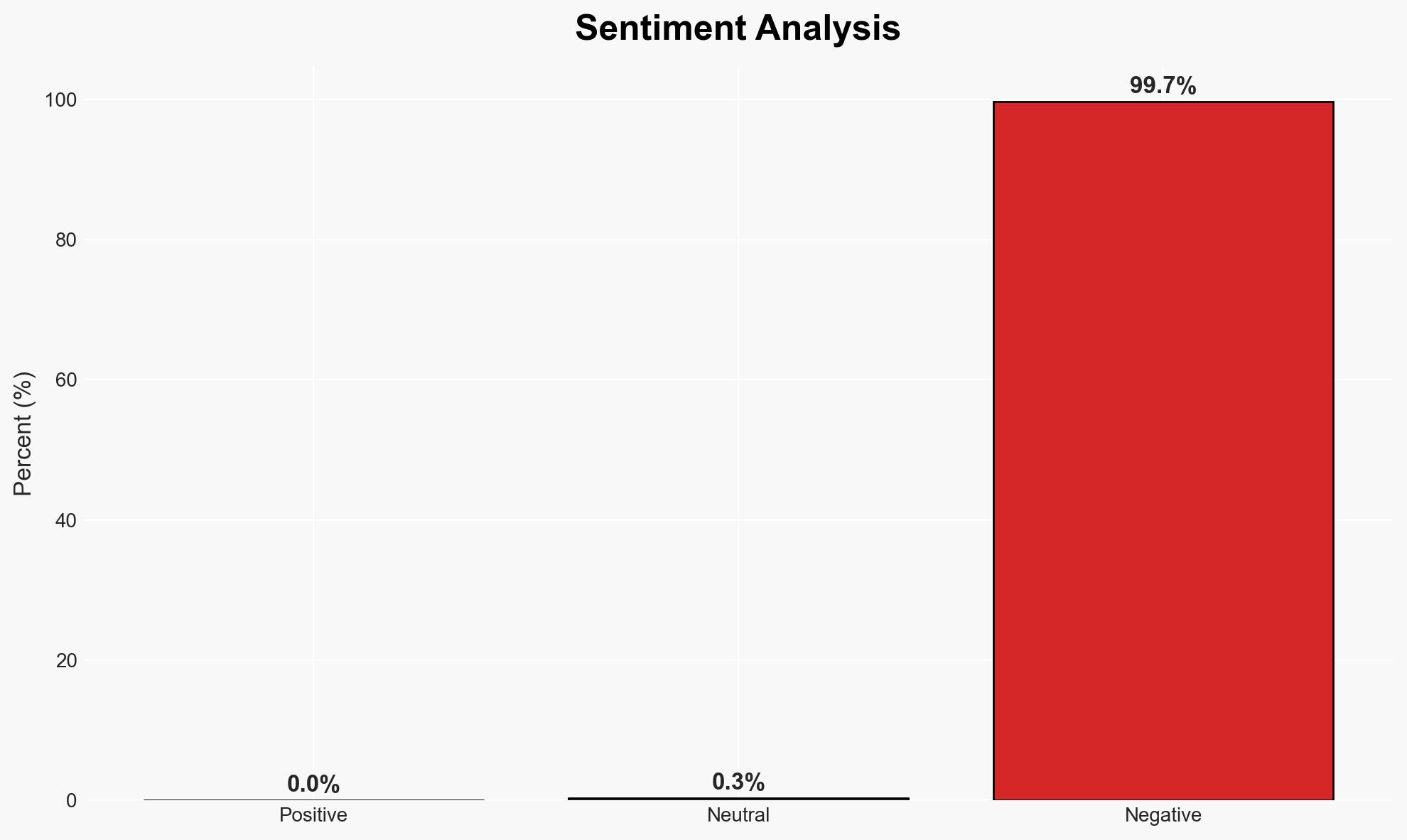
The JetBrains TeamCity 2023114 vulnerability allows for an authentication bypass, potentially enabling unauthorized access to administrative functions. This exploit could impact organizations using this software, posing significant security risks. The most likely hypothesis is that this vulnerability is being actively exploited by cyber actors. Overall confidence in this assessment is moderate due to limited information on the exploit’s prevalence and impact.
2. Competing Hypotheses
- Hypothesis A: The vulnerability is being actively exploited by malicious actors to gain unauthorized access to systems. This is supported by the existence of a detailed exploit script and the potential for significant security breaches. However, there is uncertainty regarding the scale and scope of exploitation.
- Hypothesis B: The vulnerability is not yet widely exploited, and the release of the exploit script is primarily a proof of concept. This hypothesis is contradicted by the detailed nature of the exploit, suggesting readiness for operational use.
- Assessment: Hypothesis A is currently better supported due to the detailed exploit script and the high value of administrative access in cyber operations. Key indicators that could shift this judgment include reports of active exploitation or patch releases by JetBrains.
3. Key Assumptions and Red Flags
- Assumptions: The exploit script is functional and can bypass authentication as described. Organizations using TeamCity have not yet widely patched this vulnerability. Cyber actors are motivated to exploit this vulnerability for unauthorized access.
- Information Gaps: The extent of exploitation across different sectors and the timeline for patch deployment by affected organizations.
- Bias & Deception Risks: Potential bias in assuming all instances of TeamCity are vulnerable. The possibility of the exploit author exaggerating the impact for notoriety.
4. Implications and Strategic Risks
This vulnerability could lead to significant security breaches if exploited, affecting organizational integrity and data confidentiality. Over time, this could erode trust in JetBrains products and increase demand for alternative solutions.
- Political / Geopolitical: Potential for state-sponsored actors to exploit the vulnerability for espionage or sabotage.
- Security / Counter-Terrorism: Increased risk of cyber-attacks targeting critical infrastructure and sensitive data repositories.
- Cyber / Information Space: Potential for widespread information theft and disruption of services, impacting operational continuity.
- Economic / Social: Possible financial losses and reputational damage to affected organizations, leading to broader economic impacts.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Organizations should urgently assess their exposure to this vulnerability and apply available patches. Increased monitoring for signs of exploitation is recommended.
- Medium-Term Posture (1–12 months): Develop resilience measures, including regular security audits and incident response planning. Engage with JetBrains for updates and support.
- Scenario Outlook:
- Best: Rapid patching mitigates risk with minimal exploitation.
- Worst: Widespread exploitation leads to significant breaches and operational disruptions.
- Most-Likely: Moderate exploitation with gradual patch adoption and increased security awareness.
6. Key Individuals and Entities
- JetBrains (Software Vendor)
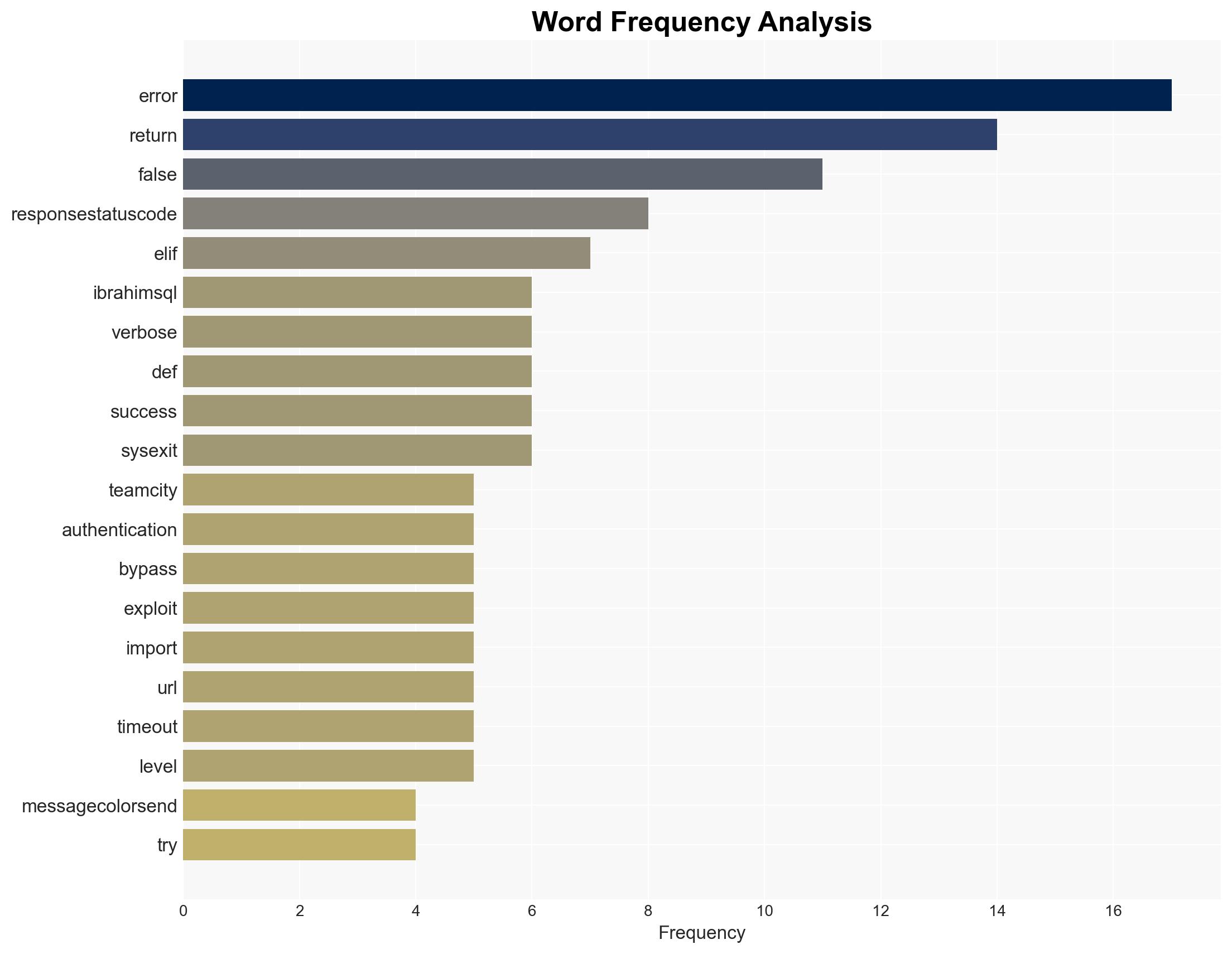
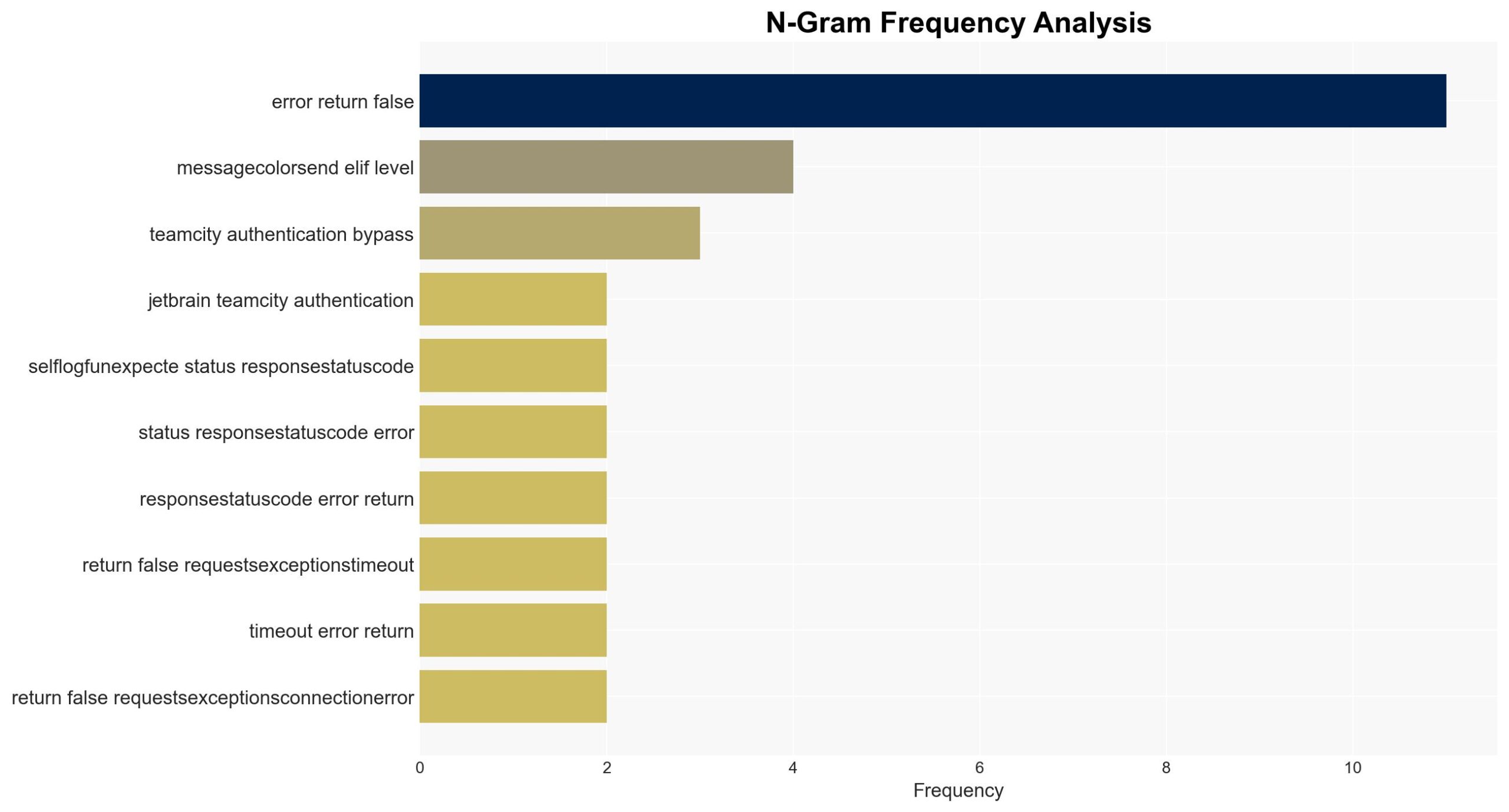
- IbrahimSQL (Exploit Author)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Cybersecurity, vulnerability management, software security, authentication bypass, cyber-espionage, threat mitigation, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us