Cloudflare Outage Highlights Need for Enhanced Security Measures and Application Defense Strategies
Published on: 2025-11-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: The Cloudflare Outage May Be a Security Roadmap
1. BLUF (Bottom Line Up Front)
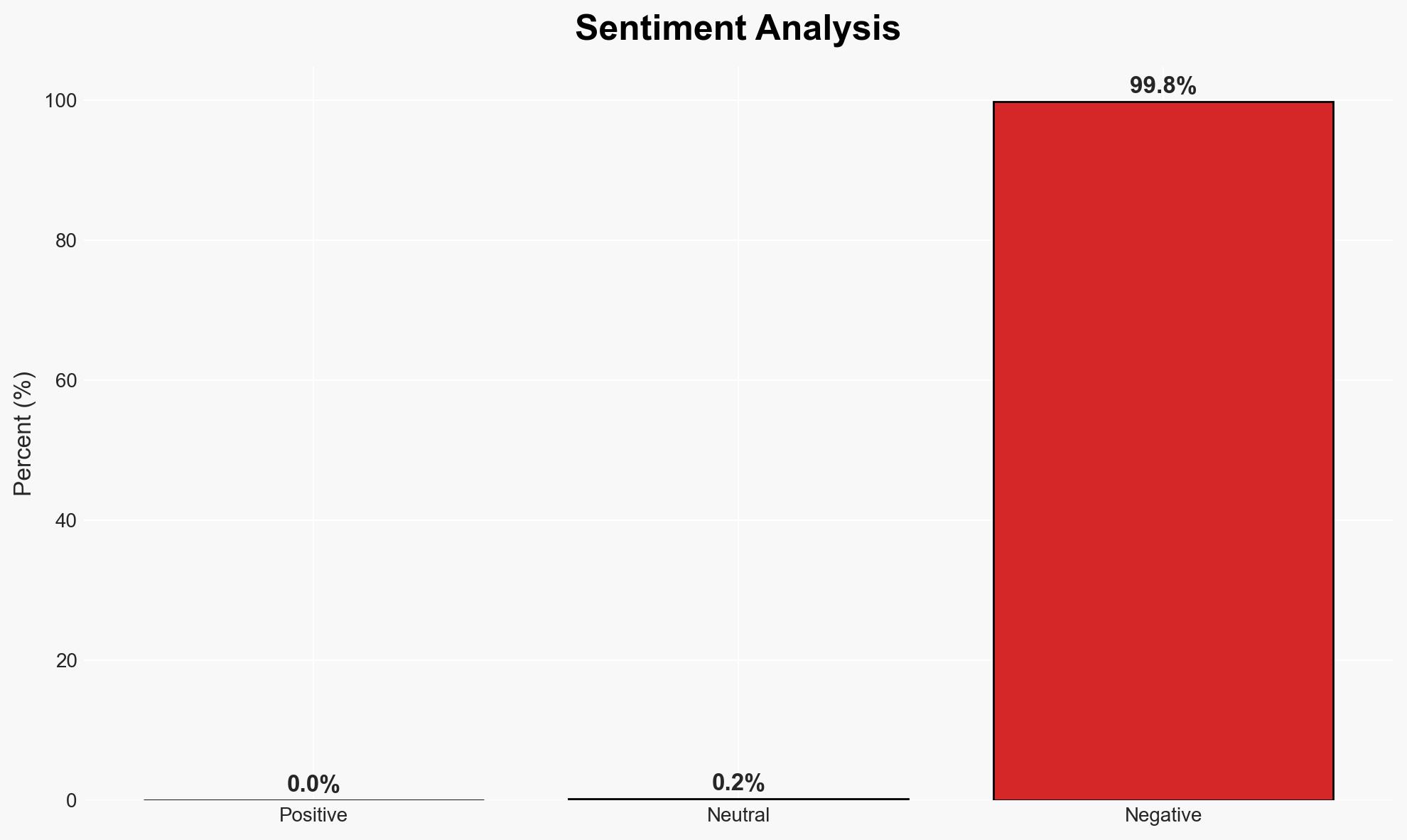
The recent Cloudflare outage exposed vulnerabilities in internet infrastructure, highlighting the reliance on a few cloud providers. The most likely hypothesis is that the outage was due to internal system errors rather than a cyberattack. This incident affects a wide range of organizations dependent on Cloudflare services. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
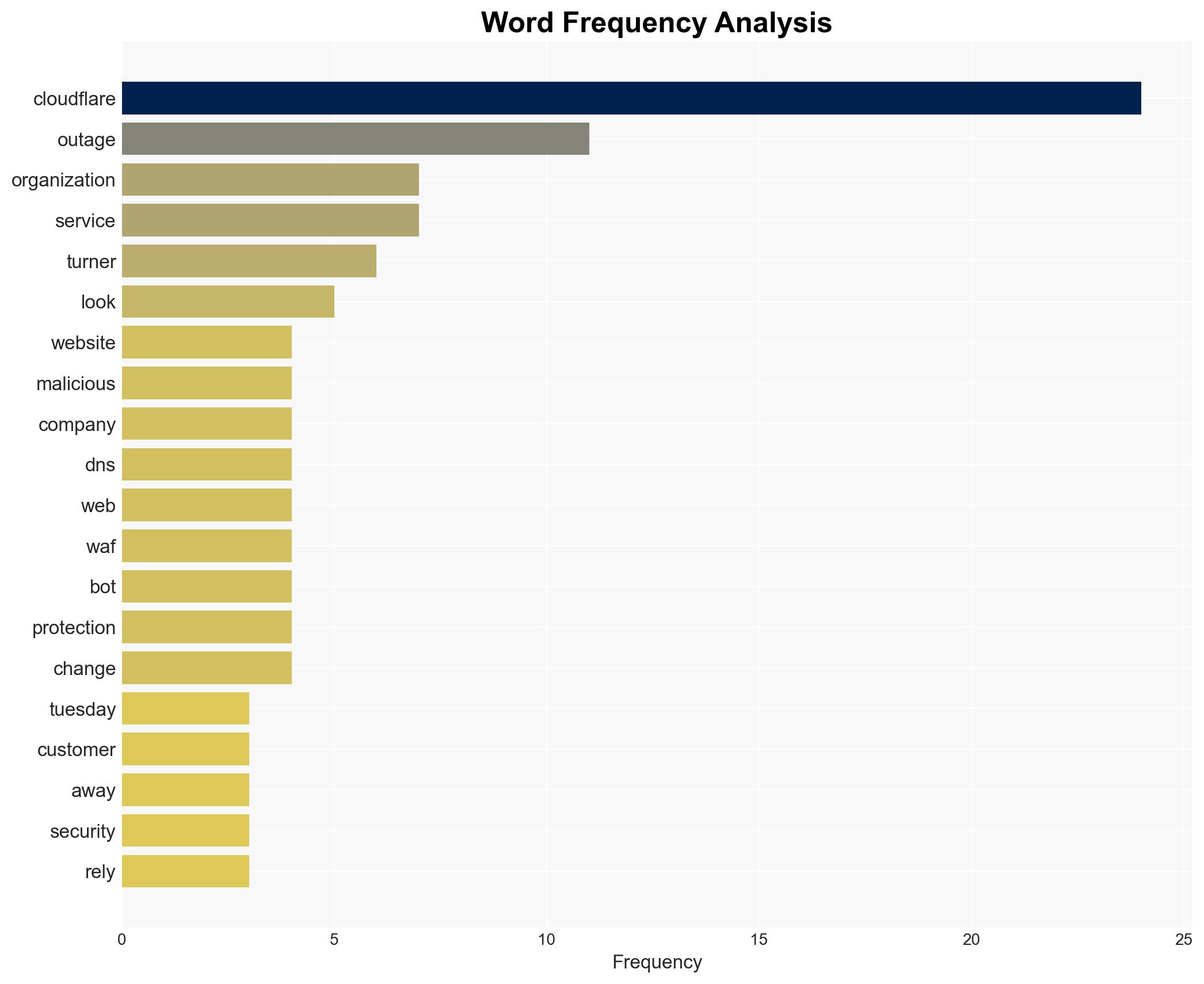
- Hypothesis A: The outage was caused by internal system errors at Cloudflare, specifically a database system permission change leading to a propagation of oversized feature files. This is supported by Cloudflare’s own postmortem analysis and the lack of evidence indicating a cyberattack.
- Hypothesis B: The outage was a result of a coordinated cyberattack exploiting Cloudflare’s infrastructure vulnerabilities. This hypothesis is contradicted by Cloudflare’s statement and the absence of typical attack indicators.
- Assessment: Hypothesis A is currently better supported due to Cloudflare’s detailed explanation and the absence of corroborating evidence for a cyberattack. Indicators such as unusual network traffic or claims of responsibility by threat actors could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Cloudflare’s postmortem analysis is accurate; no significant cyberattack indicators were missed; organizations can pivot away from Cloudflare if needed.
- Information Gaps: Detailed logs of network traffic during the outage; independent verification of Cloudflare’s internal analysis.
- Bias & Deception Risks: Potential bias in Cloudflare’s self-reporting; lack of independent analysis increases risk of deception or oversight.
4. Implications and Strategic Risks
This development underscores the fragility of internet infrastructure and the potential for cascading failures. It may prompt organizations to reassess their reliance on single providers and enhance their resilience strategies.
- Political / Geopolitical: Increased scrutiny on cloud service providers and potential regulatory responses.
- Security / Counter-Terrorism: Heightened awareness of infrastructure vulnerabilities could alter threat actor strategies.
- Cyber / Information Space: Potential for increased cyber resilience measures and diversification of service providers.
- Economic / Social: Short-term disruptions to businesses relying on Cloudflare, potential long-term shifts in cloud service market dynamics.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor for any claims of responsibility or unusual cyber activity; encourage organizations to review and test their contingency plans.
- Medium-Term Posture (1–12 months): Develop partnerships for independent verification of cloud service reliability; invest in redundant systems and multi-provider strategies.
- Scenario Outlook:
- Best: Outage leads to improved infrastructure resilience without major disruptions.
- Worst: Further outages or attacks exploit similar vulnerabilities, causing widespread disruptions.
- Most-Likely: Incremental improvements in security practices and diversification of service providers.
6. Key Individuals and Entities
- Matthew Prince, CEO of Cloudflare
- Aaron Turner, Faculty Member at IAN Research
- Nicole Scott, Senior Product Marketing Manager at Replica Cyber
- Cloudflare
7. Thematic Tags
Cybersecurity, cloud infrastructure, cyber resilience, internet security, cloud service providers, incident response, network vulnerabilities, contingency planning
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us