New Strategies Needed to Combat AI-Driven Cyber Espionage Threats
Published on: 2025-12-01
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: A Practical Defense Against AI-led Attacks
1. BLUF (Bottom Line Up Front)
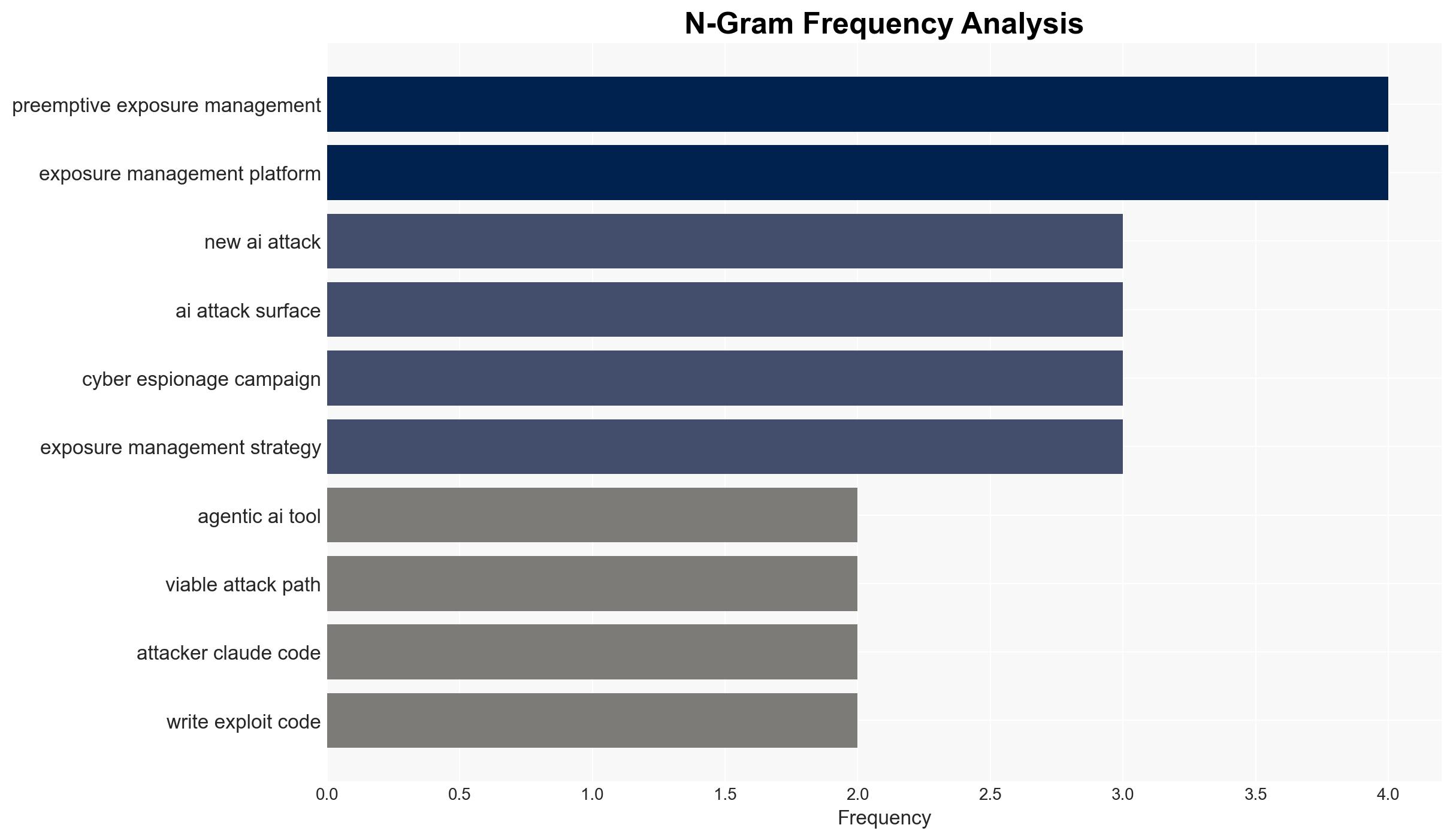
The emergence of AI-driven cyberattacks, exemplified by the abuse of the Claude code AI tool in a recent espionage campaign, necessitates a shift from traditional security measures to preemptive exposure management. This development affects national security, cybersecurity, and organizational resilience. Overall confidence in this assessment is moderate, given the evolving nature of AI capabilities and the potential for rapid escalation.
2. Competing Hypotheses
- Hypothesis A: AI-driven cyberattacks are now a tangible threat, requiring immediate adaptation of security strategies. Evidence includes the operational use of AI tools in espionage campaigns, but uncertainty exists regarding the scalability and reproducibility of such attacks.
- Hypothesis B: The threat of AI-driven cyberattacks is overstated, with current incidents being isolated and not indicative of a broader trend. This hypothesis is supported by the limited number of reported cases, though it contradicts the increasing sophistication of AI tools.
- Assessment: Hypothesis A is currently better supported due to the documented use of AI in recent cyber espionage activities and the proactive measures being recommended by security experts. Key indicators that could shift this judgment include further widespread incidents or technological advancements in AI capabilities.
3. Key Assumptions and Red Flags
- Assumptions: AI capabilities will continue to advance rapidly; organizations will struggle to adapt to new AI-driven threats; current security frameworks are insufficient against AI-led attacks.
- Information Gaps: Detailed data on the frequency and success rate of AI-driven attacks; comprehensive analysis of AI tool capabilities and limitations.
- Bias & Deception Risks: Potential overreliance on vendor-reported capabilities of AI tools; cognitive bias towards assuming technological inevitability without sufficient empirical evidence.
4. Implications and Strategic Risks
The development of AI-driven cyberattacks could lead to significant shifts in the security landscape, necessitating new defense paradigms and potentially altering geopolitical power dynamics.
- Political / Geopolitical: Increased tensions between nation-states as AI tools are weaponized for espionage and sabotage.
- Security / Counter-Terrorism: Enhanced threat environment with AI tools potentially being used by non-state actors and terrorist groups.
- Cyber / Information Space: Accelerated arms race in cyber capabilities, with AI tools enabling more sophisticated and rapid attacks.
- Economic / Social: Potential destabilization of markets and erosion of public trust in digital systems if AI-driven attacks become widespread.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of AI tool usage in cyber activities; implement preemptive exposure management strategies; increase collaboration with AI research entities.
- Medium-Term Posture (1–12 months): Develop resilience measures against AI-driven threats; foster international partnerships for AI threat intelligence sharing; invest in AI capability development for defensive purposes.
- Scenario Outlook:
- Best Case: Successful adaptation to AI threats with minimal disruption.
- Worst Case: Proliferation of AI-driven attacks leading to significant geopolitical and economic instability.
- Most-Likely: Gradual increase in AI-driven incidents, prompting ongoing adaptation and policy development.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
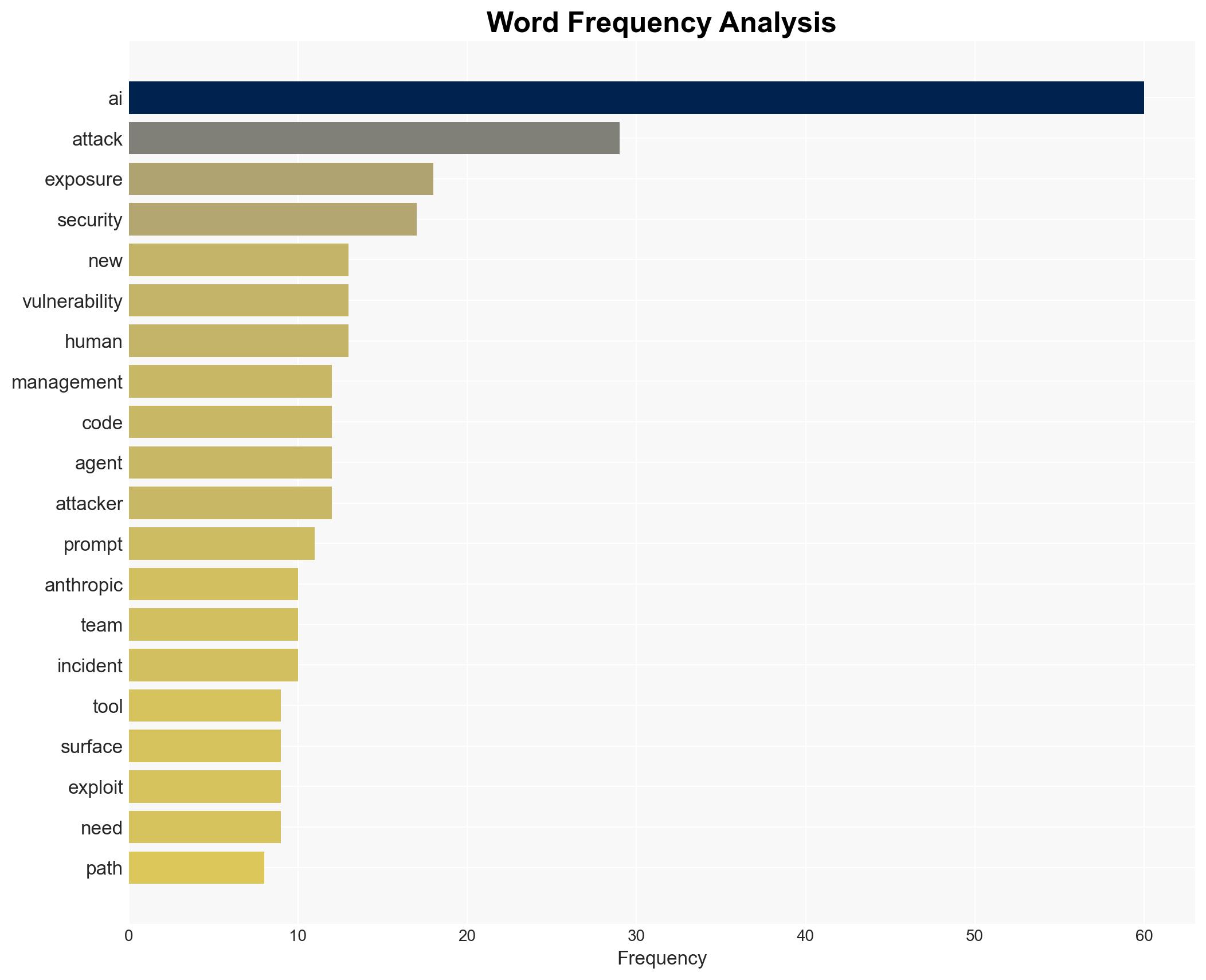
Cybersecurity, AI-driven attacks, espionage, national security, cyber defense, AI capabilities, threat intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
- ACH 2.0: Machine-assisted hypothesis testing for intent reconstruction.
- Network Influence Mapping: Map influence relationships to assess actor impact.
- Cross-Impact Simulation: Simulate cascading interdependencies and system risks.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us