Aggressive bots ruined my weekend – Bearblog.dev
Published on: 2025-10-29
Intelligence Report: Aggressive bots ruined my weekend – Bearblog.dev
1. BLUF (Bottom Line Up Front)
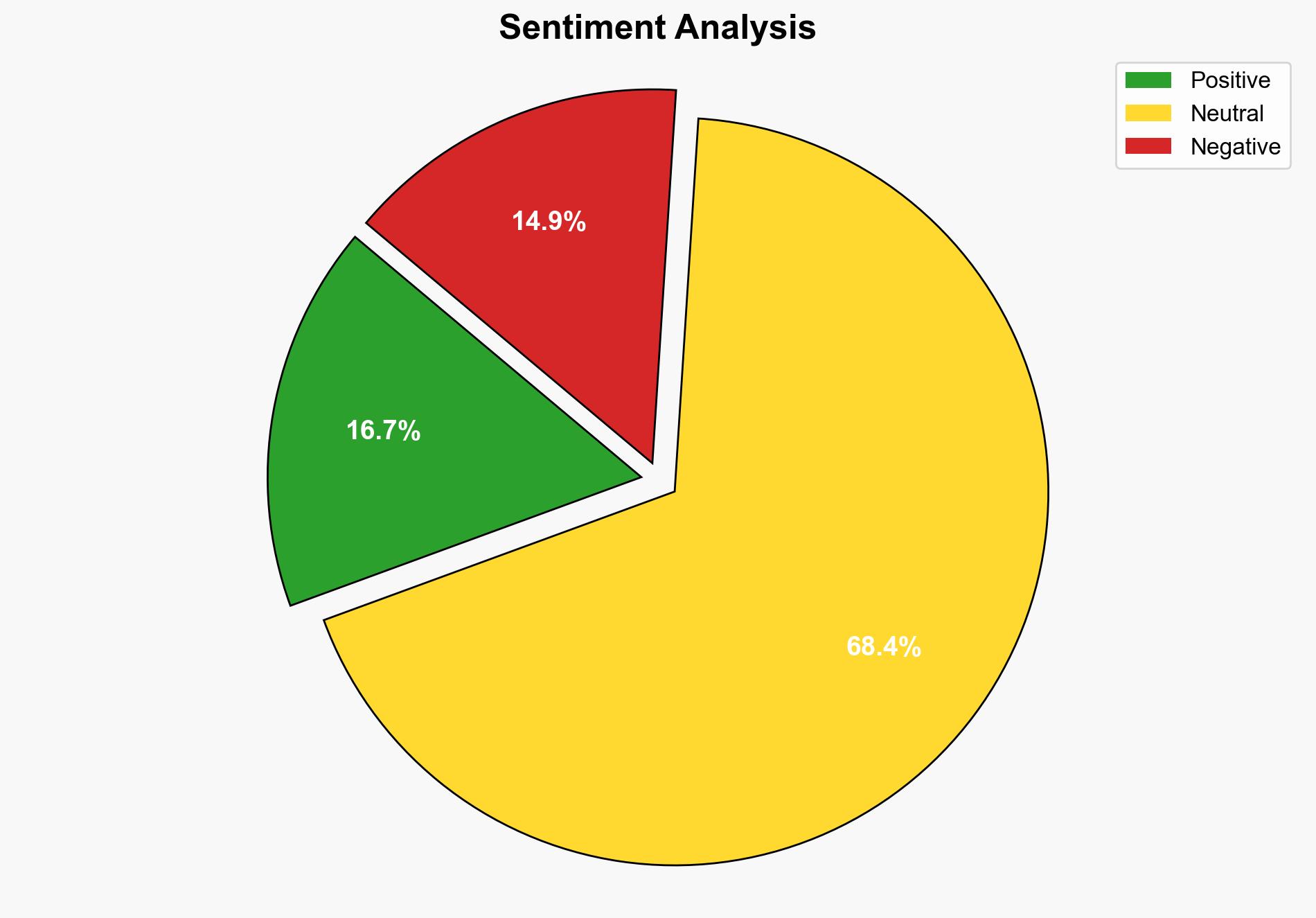
The most supported hypothesis is that the aggressive bot activity was primarily driven by malicious actors seeking to exploit vulnerabilities for data scraping and potential financial gain. Confidence level is moderate due to the lack of direct attribution evidence. Recommended actions include enhancing bot detection mechanisms and implementing more robust monitoring systems to prevent future disruptions.
2. Competing Hypotheses
1. **Hypothesis A**: The bot activity was primarily driven by malicious actors aiming to scrape data for financial or strategic gain. This includes AI training data acquisition or exploiting website vulnerabilities.
2. **Hypothesis B**: The bot activity was an unintended consequence of increased automation and the proliferation of web scraping tools, with no specific malicious intent but rather opportunistic behavior by various entities.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the systematic and aggressive nature of the bot activity, which suggests a targeted approach rather than random automation.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the bot activity was not state-sponsored and that the failure of monitoring tools was an isolated incident.
– **Red Flags**: The failure of monitoring tools to alert the administrator raises concerns about potential oversight or technical deficiencies.
– **Blind Spots**: Lack of detailed information on the origin of the bot traffic limits the ability to attribute the activity to specific actors.
4. Implications and Strategic Risks
The incident highlights the vulnerability of web services to automated bot attacks, which can have cascading effects on service availability and data integrity. Economically, such disruptions can lead to loss of revenue and reputational damage. Cybersecurity risks are elevated, with potential for data breaches if vulnerabilities are exploited. Geopolitically, if state actors are involved, this could escalate into broader cyber conflict.
5. Recommendations and Outlook
- Enhance bot detection and mitigation strategies, including advanced machine learning algorithms to identify and block malicious traffic.
- Implement redundant monitoring systems to ensure timely alerts in case of future incidents.
- Scenario Projections:
- Best Case: Successful implementation of enhanced security measures prevents future disruptions.
- Worst Case: Continued bot attacks lead to significant data breaches and financial losses.
- Most Likely: Incremental improvements in security reduce but do not eliminate bot-related disruptions.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. The entities involved include Bearblog.dev and potentially various unidentified bot operators.
7. Thematic Tags
national security threats, cybersecurity, data scraping, web security, automated attacks