An incredibly popular JavaScript library might have some worrying malware issues – TechRadar
Published on: 2025-11-11
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: An incredibly popular JavaScript library might have some worrying malware issues – TechRadar
1. BLUF (Bottom Line Up Front)
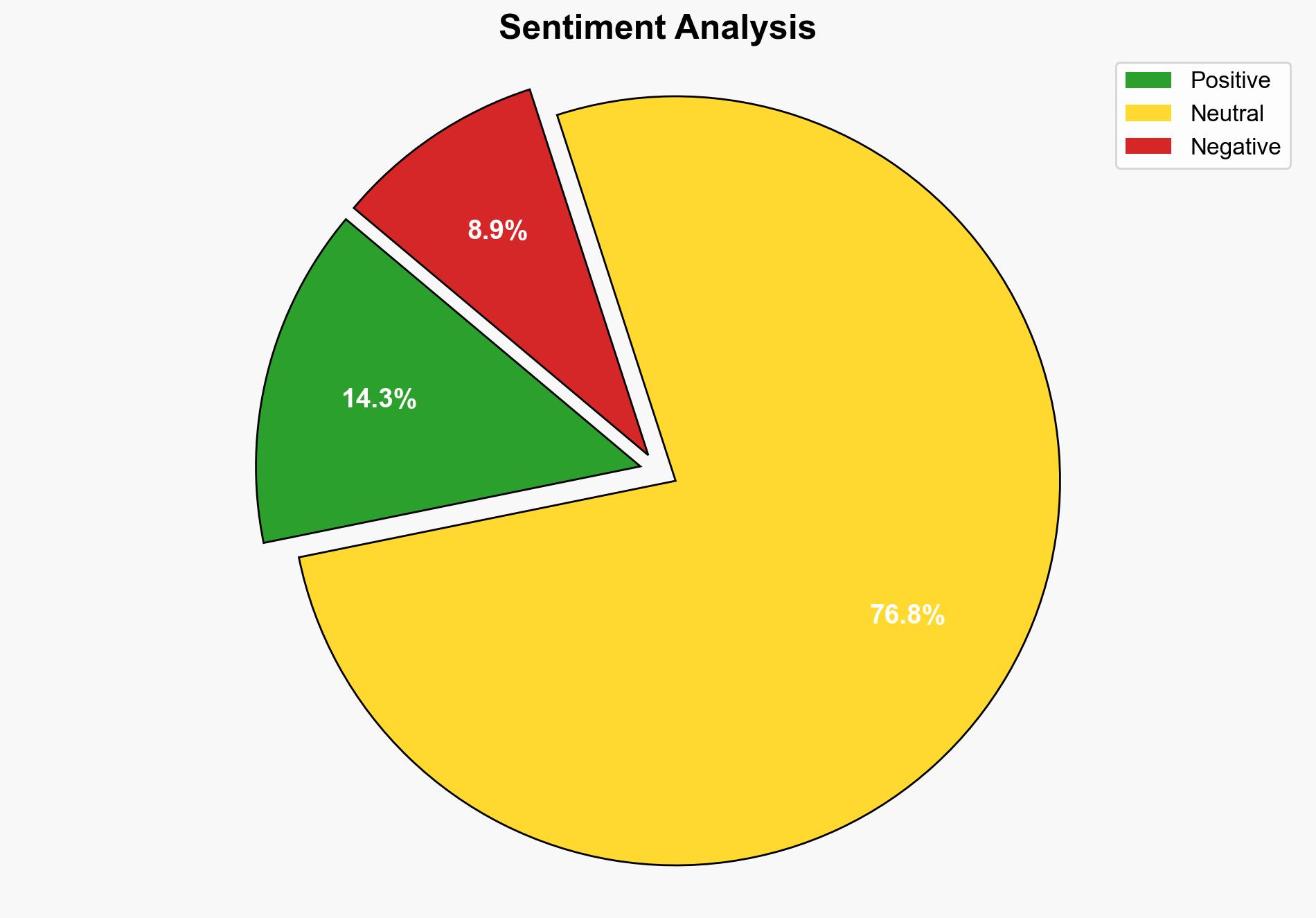
The most supported hypothesis is that the vulnerability in the JavaScript library is a result of insufficient input validation, which poses a significant cybersecurity risk due to its widespread use. The confidence level in this assessment is high based on the evidence provided by security researchers. Recommended actions include immediate patching, migrating to a secure fork, and implementing robust input sanitization practices.
2. Competing Hypotheses
Hypothesis 1: The vulnerability is due to a genuine oversight in the library’s development, specifically in input validation, which has been exploited by threat actors.
Hypothesis 2: The vulnerability was intentionally introduced by a malicious insider or external actor to exploit the library’s widespread use for cyberattacks.
Hypothesis 1 is more likely due to the common occurrence of such oversights in software development and the absence of direct evidence pointing to malicious intent in the library’s development history.
3. Key Assumptions and Red Flags
Assumptions include the reliability of the security researcher’s findings and the assumption that the vulnerability was not previously known to the library’s developers. A red flag is the potential underreporting of similar vulnerabilities in other libraries, which could indicate a broader systemic issue. Deception indicators include the possibility of misinformation regarding the severity or scope of the vulnerability.
4. Implications and Strategic Risks
The vulnerability could lead to significant cyber risks, including unauthorized access to sensitive data, disruption of services, and potential financial losses for organizations using the library. Politically, this could escalate into discussions about software supply chain security. Economically, it could affect companies relying on the library for critical applications, leading to reputational damage and loss of consumer trust.
5. Recommendations and Outlook
- Organizations should immediately apply available patches or migrate to secure forks of the library.
- Implement comprehensive input validation and sanitization practices to mitigate similar vulnerabilities.
- Best-case scenario: The vulnerability is swiftly patched with minimal exploitation incidents.
- Worst-case scenario: Widespread exploitation occurs before mitigation, leading to significant data breaches and financial losses.
- Most-likely scenario: A moderate number of exploitation incidents occur, but are contained through timely patching and mitigation efforts.
6. Key Individuals and Entities
Jangwoo Choe (Security Researcher)
7. Thematic Tags
Cybersecurity
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Methodology