Cisco firewalls are facing another huge surge of attacks – here’s what we know about these latest issues – TechRadar
Published on: 2025-11-07
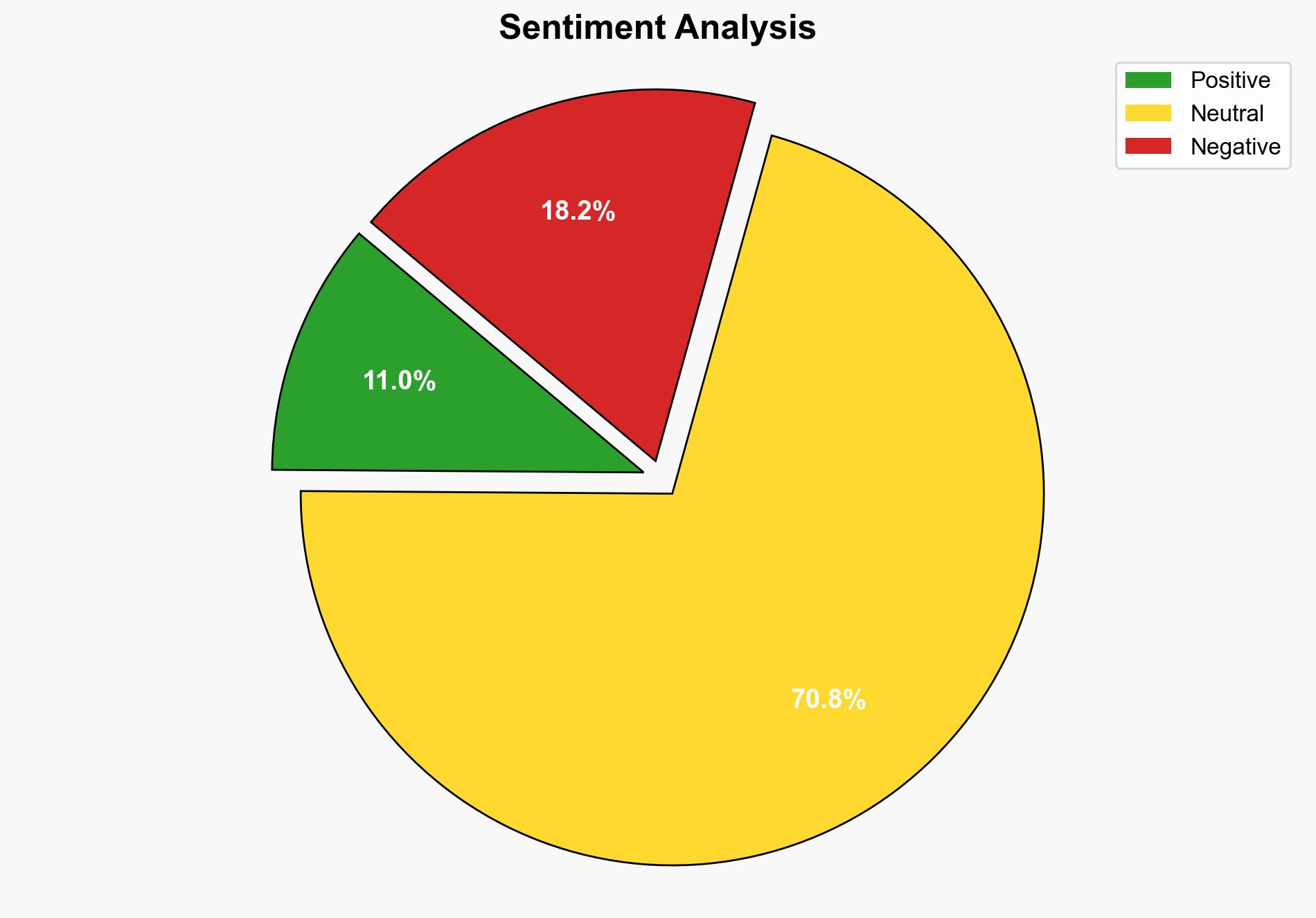
Intelligence Report: Cisco firewalls are facing another huge surge of attacks – here’s what we know about these latest issues – TechRadar
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that the surge in attacks on Cisco firewalls is part of a coordinated campaign by a sophisticated threat actor exploiting multiple zero-day vulnerabilities. This assessment is made with a high confidence level due to the advanced evasion techniques and the persistence of the attacks. It is recommended that organizations using Cisco ASA firewalls immediately upgrade to secure boot-enabled models and apply all available patches to mitigate these threats.
2. Competing Hypotheses
1. **Coordinated Campaign by a Sophisticated Threat Actor**: The attacks are part of a deliberate and organized effort by a well-resourced threat actor exploiting zero-day vulnerabilities in Cisco ASA firewalls to gain remote access and maintain persistence.
2. **Opportunistic Attacks by Multiple Actors**: The surge in attacks is due to multiple, possibly unrelated, threat actors independently discovering and exploiting the vulnerabilities in Cisco firewalls, driven by the availability of new attack techniques and tools.
3. Key Assumptions and Red Flags
– **Assumptions**:
– The vulnerabilities are not yet widely known or patched.
– The threat actor(s) possess advanced technical capabilities.
– **Red Flags**:
– Lack of detailed attribution to specific threat actors.
– Potential underestimation of the number of affected devices.
– **Blind Spots**:
– Insufficient information on the origin and intent of the threat actors.
– Limited visibility into the full scope of the attack campaign.
4. Implications and Strategic Risks
The ongoing attacks pose significant risks to organizations using Cisco ASA firewalls, potentially leading to unauthorized access, data breaches, and operational disruptions. If not mitigated, these vulnerabilities could be exploited for broader cyber-espionage or sabotage activities. The economic impact could be substantial, affecting not only the targeted organizations but also their partners and clients. Geopolitically, these attacks could escalate tensions if linked to state-sponsored actors.
5. Recommendations and Outlook
- **Immediate Actions**: Upgrade to secure boot-enabled models and apply all available patches. Disable vulnerable services and reset compromised devices to factory settings.
- **Long-term Strategy**: Implement continuous monitoring and threat intelligence sharing to detect and respond to emerging threats promptly.
- **Scenario Projections**:
– **Best Case**: Rapid patch deployment and security enhancements prevent further exploitation.
– **Worst Case**: Continued exploitation leads to widespread breaches and operational disruptions.
– **Most Likely**: Partial mitigation with ongoing attempts by threat actors to exploit remaining vulnerabilities.
6. Key Individuals and Entities
– Cisco Systems
– Threat actors exploiting vulnerabilities
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus