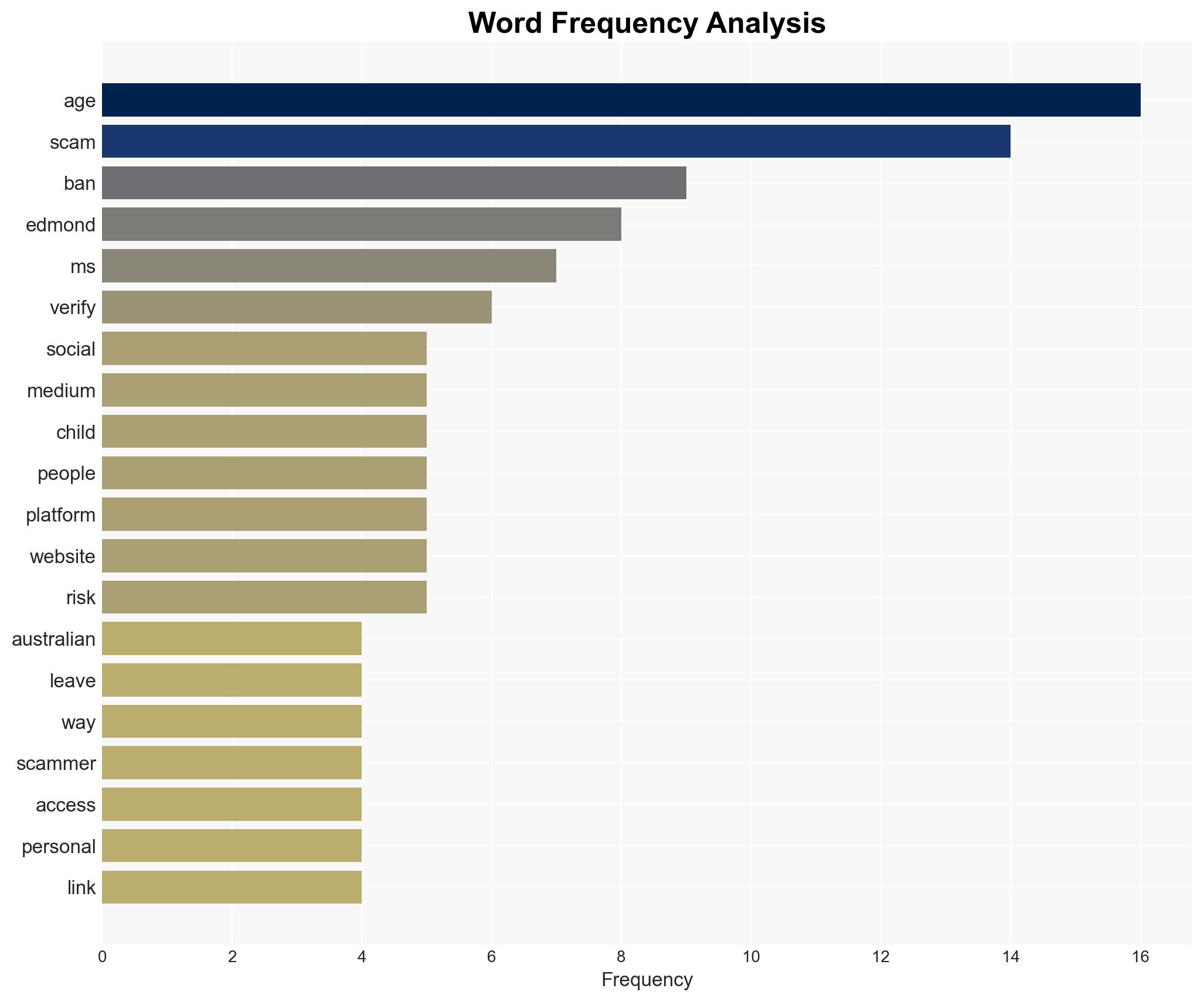
Experts warn that Australia’s social media age verification may increase children’s risk of phishing scams.
Published on: 2025-11-30
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Social media ban leaves children vulnerable to phishing scams experts say
1. BLUF (Bottom Line Up Front)
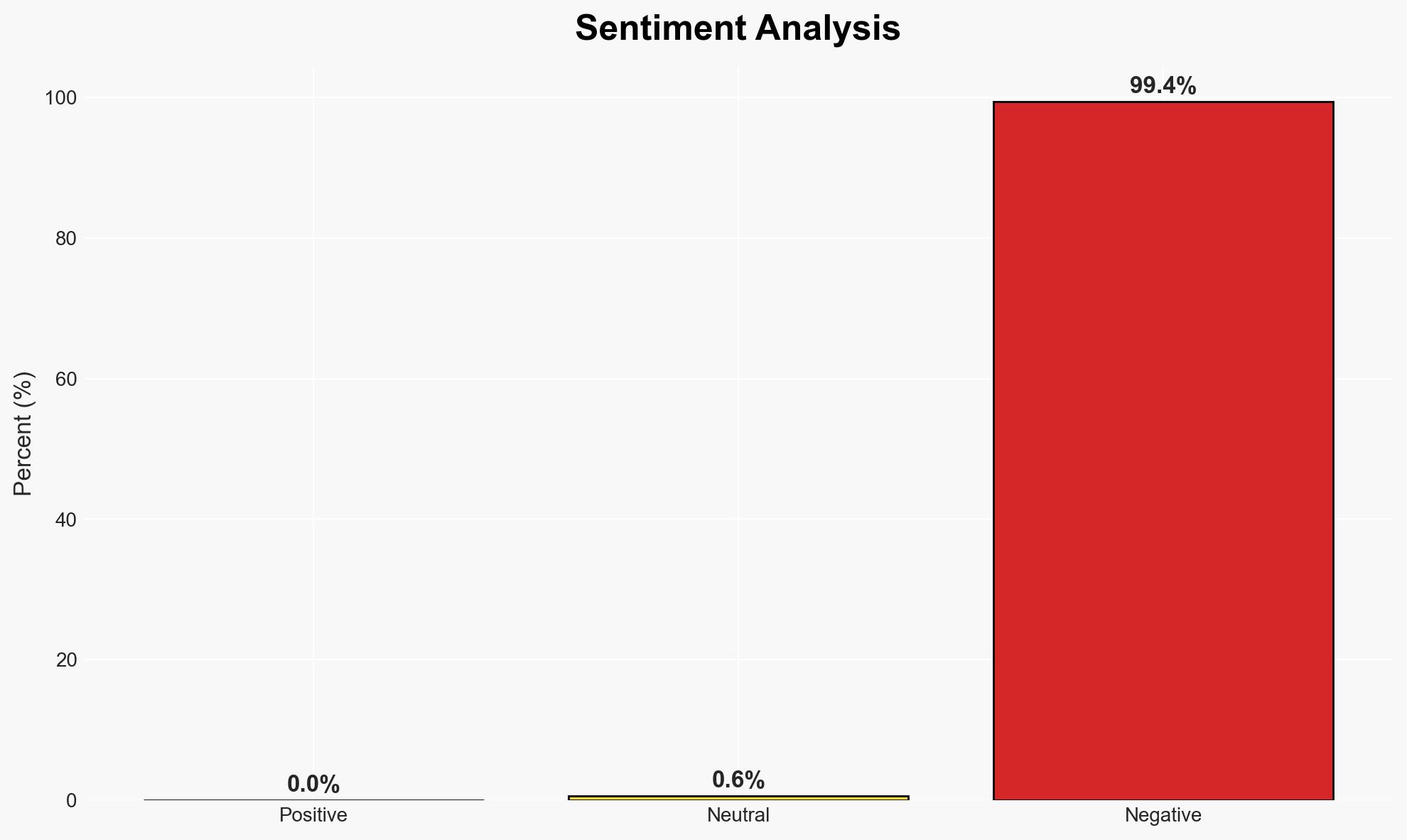
The impending Australian social media age verification ban may inadvertently increase children’s vulnerability to phishing scams. This policy change could provide scammers with new opportunities to exploit personal data under the guise of age verification. The affected parties include children, parents, and the broader Australian digital community. Overall confidence in this assessment is moderate due to potential information gaps and the evolving nature of cyber threats.
2. Competing Hypotheses
- Hypothesis A: The social media age verification ban will increase phishing risks by providing scammers with a credible cover story for data collection. Supporting evidence includes expert warnings about scammers exploiting age verification processes. Contradicting evidence is limited due to the policy’s novelty, creating uncertainty about its actual impact.
- Hypothesis B: The ban will effectively reduce underage access to social media, thereby decreasing overall exposure to online scams. This hypothesis is supported by the intended regulatory goals and similar precedents in age-restricted domains. However, evidence is weak as it relies on assumptions about effective enforcement and compliance.
- Assessment: Hypothesis A is currently better supported due to expert analysis and historical patterns of scam adaptation to new regulations. Key indicators that could shift this judgment include empirical data on scam incidents post-implementation and effectiveness of age verification technologies.
3. Key Assumptions and Red Flags
- Assumptions: The age verification process will be perceived as legitimate by users; scammers will adapt quickly to exploit new opportunities; children and parents lack sufficient awareness of phishing tactics; regulatory enforcement will be inconsistent.
- Information Gaps: Data on the effectiveness of age verification technologies; detailed scam incident reports post-ban implementation; user compliance rates with new regulations.
- Bias & Deception Risks: Potential bias from cybersecurity experts emphasizing worst-case scenarios; risk of deception by scammers using sophisticated social engineering techniques to exploit the ban.
4. Implications and Strategic Risks
This development could lead to increased cyber vulnerabilities and necessitate enhanced public awareness campaigns. Over time, it may influence regulatory approaches to digital safety and privacy.
- Political / Geopolitical: Potential for increased scrutiny on digital policy and international collaboration on cyber safety standards.
- Security / Counter-Terrorism: Heightened risk environment for digital exploitation, requiring adaptive security measures.
- Cyber / Information Space: Increased phishing activities and potential for misinformation campaigns exploiting the ban.
- Economic / Social: Possible economic impacts from increased cybersecurity costs and social implications from restricted digital access for minors.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Launch public awareness campaigns on phishing risks; enhance monitoring of scam activities related to age verification.
- Medium-Term Posture (1–12 months): Develop partnerships with tech companies for robust age verification solutions; invest in educational programs for digital literacy.
- Scenario Outlook:
- Best: Effective implementation reduces underage access and phishing incidents.
- Worst: Scammers exploit the ban extensively, increasing cybercrime rates.
- Most-Likely: Mixed outcomes with some reduction in underage access but increased phishing attempts.
6. Key Individuals and Entities
- Stacey Edmond, Cyber Safety Specialist
- Lennon Chang, Professor of Cyber Risk Policy, Deakin University
- Meta, Social Media Company
- Yoti, Third-party Age Verification Partner
- eSafety Commissioner, Australian Government
7. Thematic Tags
Cybersecurity, phishing scams, social media regulation, age verification, digital safety, online scams, policy impact
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us