Houthis claim to have dismantled a spy network linked to Saudi, American, and Israeli intelligence operations
Published on: 2025-11-10
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Houthis arrest alleged members of Saudi-American-Israeli spy ring
1. BLUF (Bottom Line Up Front)
The Houthi Ministry of Interior has announced the arrest of an alleged spy network linked to Saudi, American, and Israeli intelligence services. This development could exacerbate regional tensions and impact Yemen’s internal stability. The most likely hypothesis is that the arrests are part of a broader Houthi strategy to consolidate power and counter perceived foreign influence. Overall confidence in this assessment is moderate due to limited independent verification.
2. Competing Hypotheses
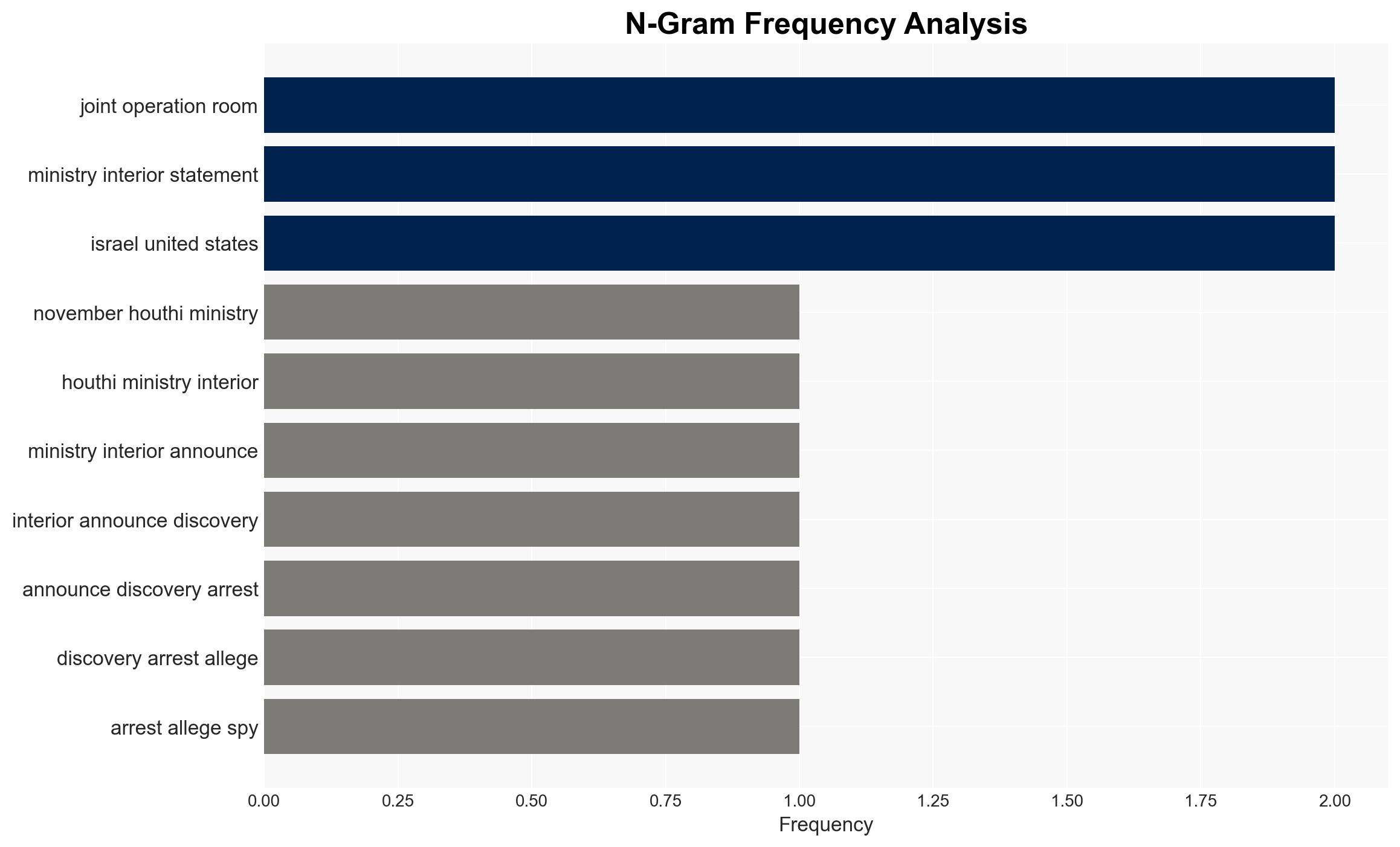
- Hypothesis A: The arrests reflect a genuine counterintelligence success by the Houthis against a real espionage network. Supporting evidence includes the detailed claims of a joint operation room and sophisticated espionage equipment. However, the lack of independent verification and potential coercion of confessions are key uncertainties.
- Hypothesis B: The arrests are a strategic move by the Houthis to justify increased repression and consolidate control by framing external powers as threats. This is supported by the timing of the arrests following a ceasefire and the historical pattern of similar claims. Contradicting evidence includes the detailed nature of the espionage claims.
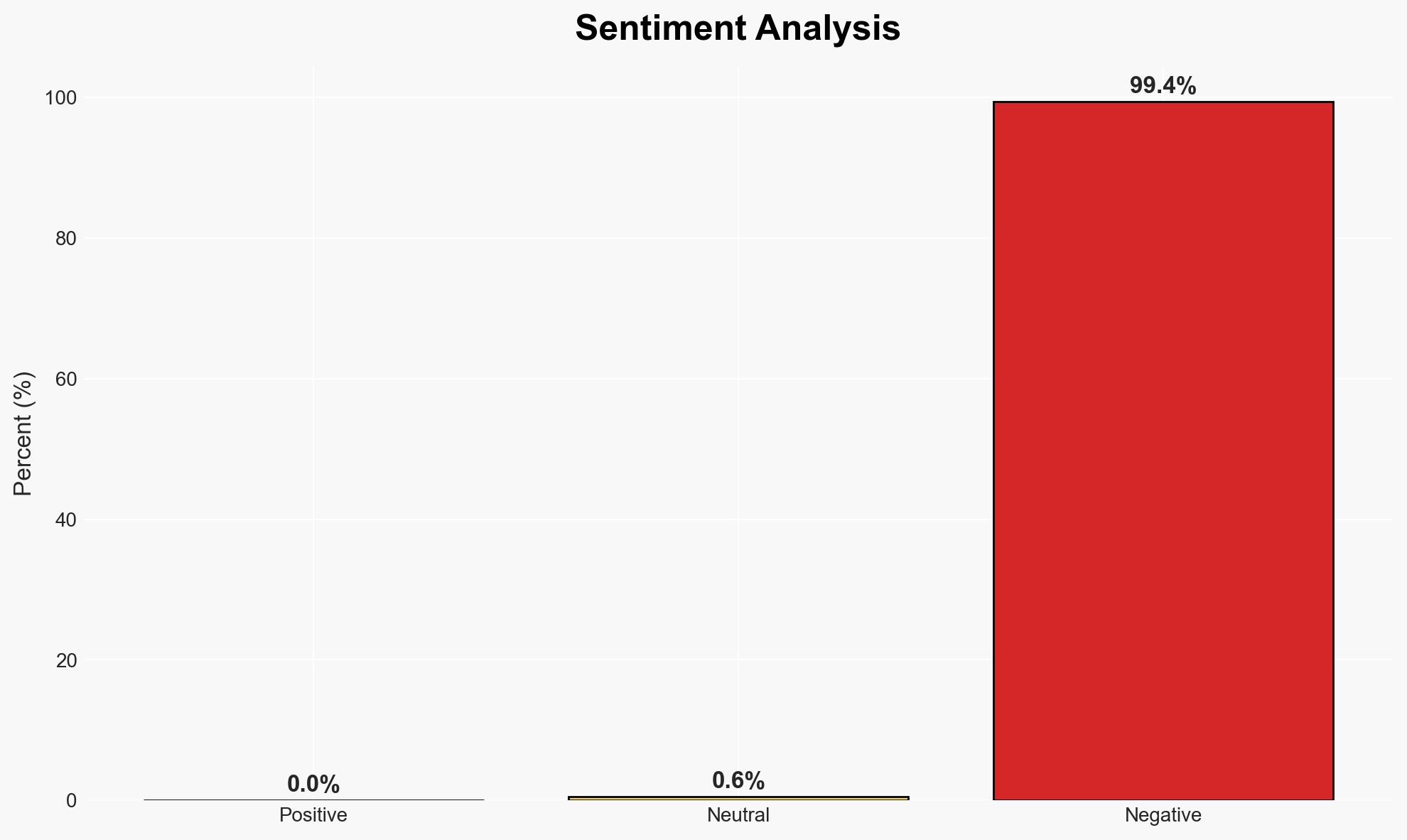
- Assessment: Hypothesis B is currently better supported due to the pattern of similar past actions by the Houthis and the lack of independent verification of the espionage claims. Key indicators that could shift this judgment include credible third-party verification of the espionage network’s existence.
3. Key Assumptions and Red Flags
- Assumptions: The Houthis have a strategic interest in portraying external threats; the confessions were obtained without coercion; the timing of the announcement is politically motivated.
- Information Gaps: Independent verification of the espionage network’s existence and activities; details on the alleged operatives’ backgrounds and affiliations.
- Bias & Deception Risks: Potential Houthi bias in framing external powers as threats; risk of coerced confessions; manipulation of public perception to justify internal crackdowns.
4. Implications and Strategic Risks
This development could lead to increased regional tensions and impact Yemen’s internal stability. The Houthis may use this narrative to justify further crackdowns on dissent and external organizations.
- Political / Geopolitical: Potential escalation of tensions between the Houthis and Saudi-led coalition; increased strain on Yemen’s relations with Western countries.
- Security / Counter-Terrorism: Heightened security measures by the Houthis; potential retaliatory actions by alleged involved states.
- Cyber / Information Space: Increased propaganda and information operations by the Houthis to bolster internal support and discredit external actors.
- Economic / Social: Potential negative impact on humanitarian operations and economic conditions due to increased internal repression.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor Houthi communications for further developments; engage with regional partners to assess the validity of the claims; prepare for potential humanitarian impact.
- Medium-Term Posture (1–12 months): Strengthen intelligence-sharing with regional allies; enhance diplomatic efforts to de-escalate tensions; support resilience measures for affected civilian populations.
- Scenario Outlook: Best: De-escalation through diplomatic engagement. Worst: Escalation of conflict and increased repression. Most-Likely: Continued Houthi narrative of external threats to justify internal actions, with moderate regional tensions.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
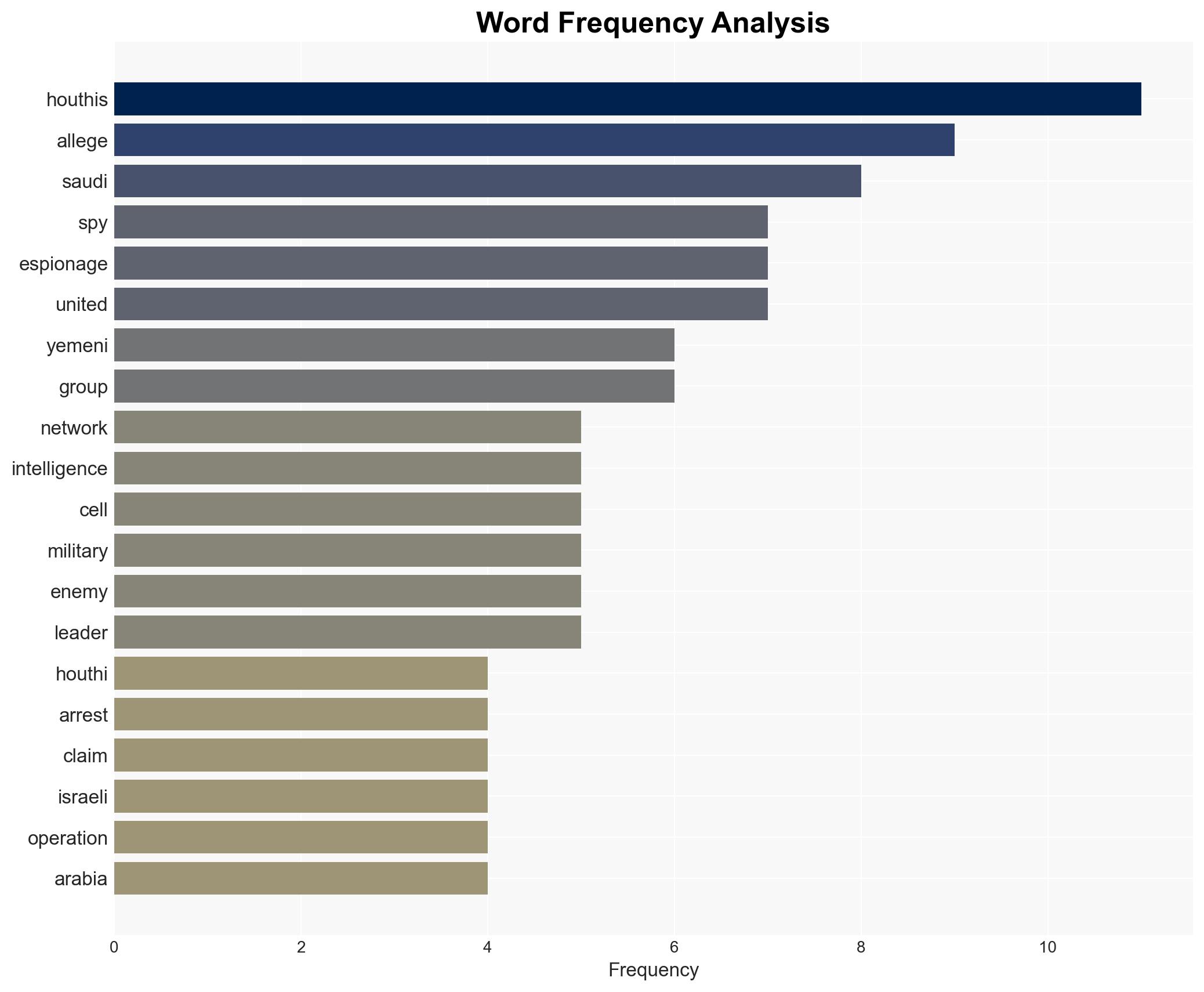
Counter-Terrorism, counter-intelligence, regional tensions, Houthi strategy, espionage claims, internal repression, geopolitical dynamics, information operations
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us