India Mandates Pre-Installation of Government Cybersecurity App on Mobile Devices to Combat Telecom Fraud
Published on: 2025-12-01
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: India Orders Phone Makers to Pre-Install Government App to Tackle Telecom Fraud
1. BLUF (Bottom Line Up Front)
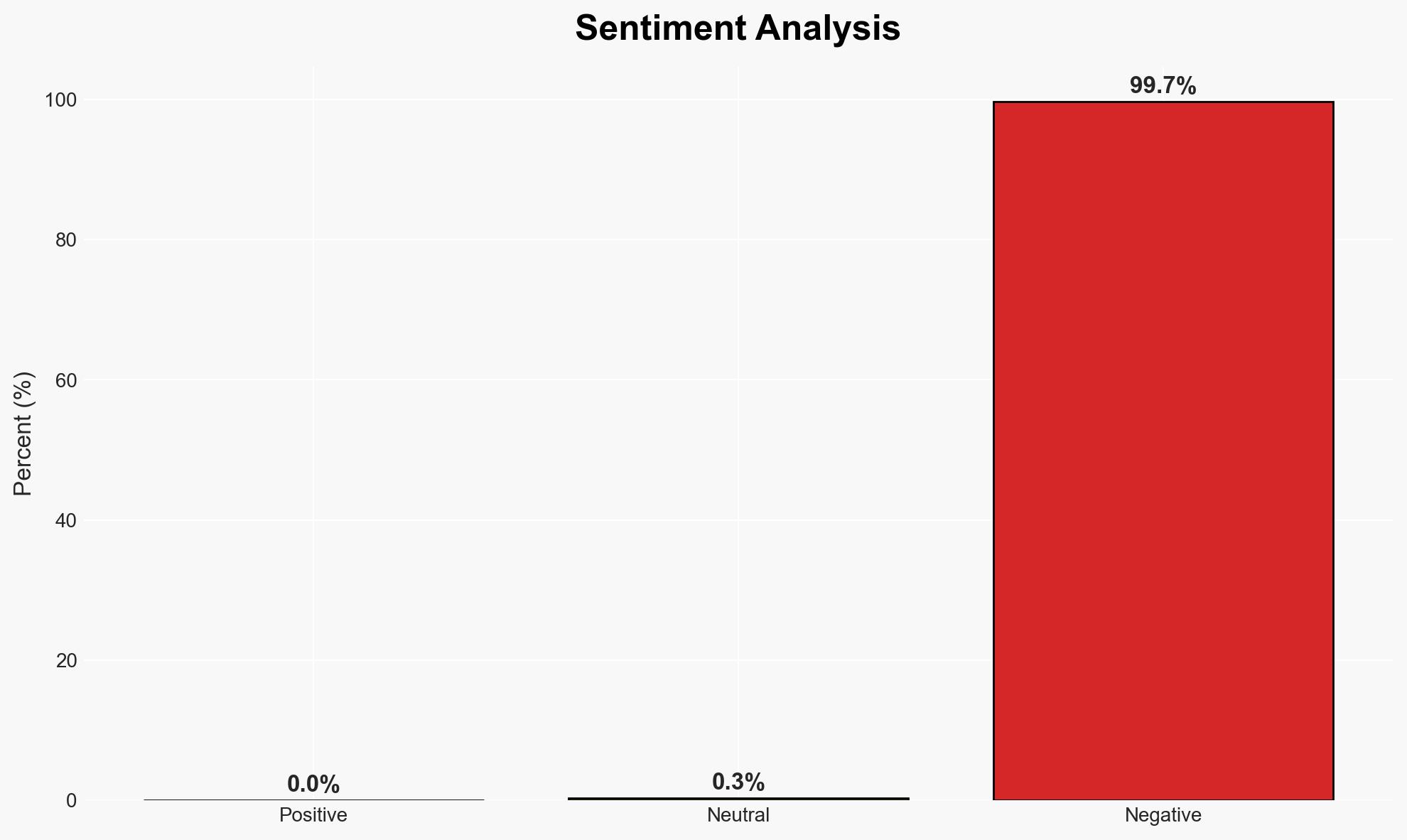
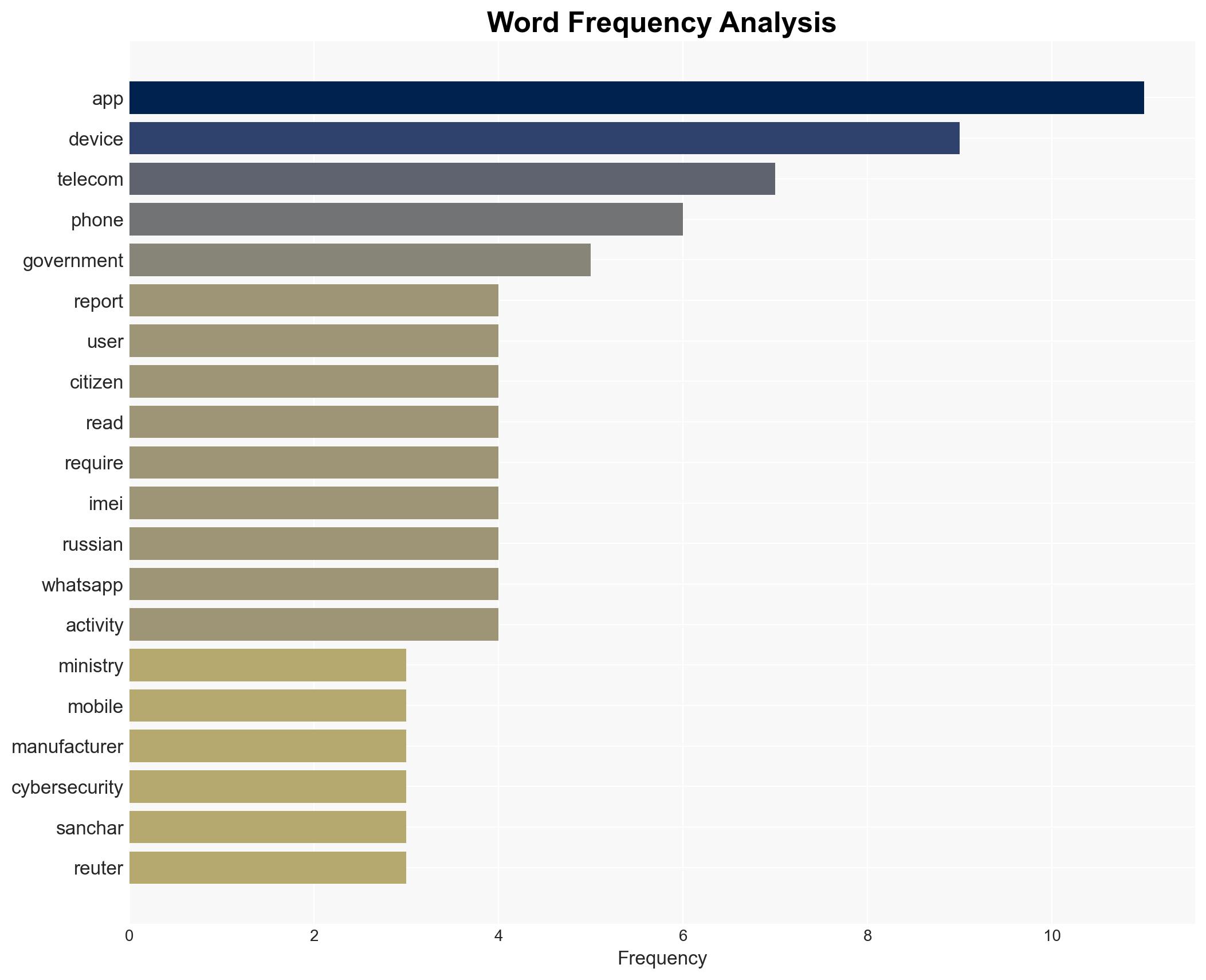
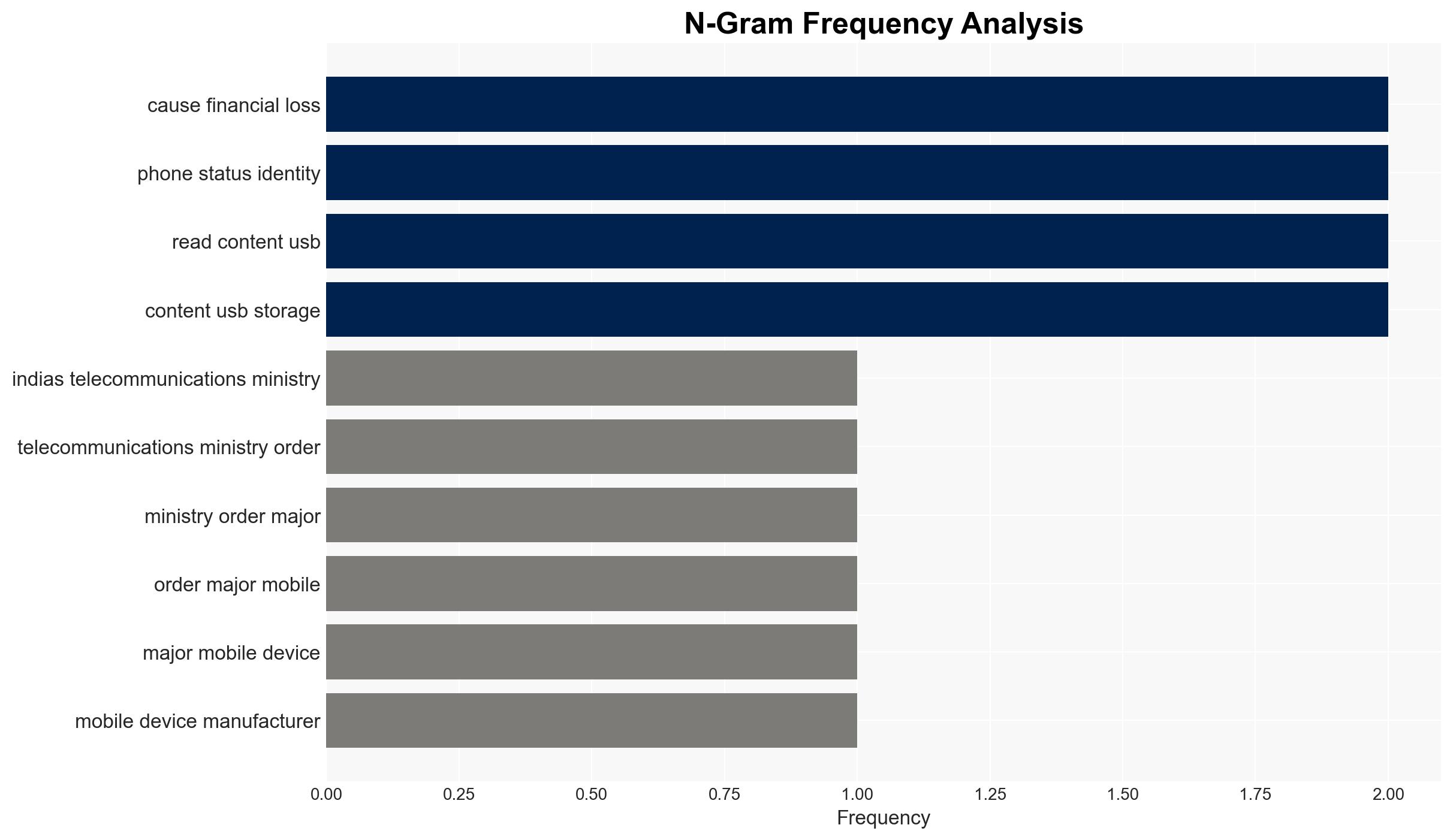
India’s directive for mobile manufacturers to pre-install the Sanchar Saathi app aims to combat telecom fraud and enhance cybersecurity. The initiative is likely to affect mobile users, manufacturers, and the telecom industry. The most supported hypothesis is that this move primarily targets fraud prevention, with moderate confidence in this assessment given the available data.
2. Competing Hypotheses
- Hypothesis A: The primary goal of the pre-installation directive is to prevent telecom fraud and protect national security. Supporting evidence includes the app’s features to report fraudulent calls and trace lost devices. However, uncertainties remain about the app’s effectiveness and user acceptance.
- Hypothesis B: The directive may serve as a tool for increased government surveillance and control over telecommunications. This is supported by parallels to Russia’s similar mandates and concerns over privacy. Contradicting evidence includes the app’s stated focus on fraud prevention.
- Assessment: Hypothesis A is currently better supported due to the app’s specific functionalities aimed at fraud detection and prevention. Indicators that could shift this judgment include evidence of misuse for surveillance or significant public backlash.
3. Key Assumptions and Red Flags
- Assumptions: The app will effectively reduce telecom fraud; users will adopt the app without significant resistance; the government will not misuse the app for surveillance.
- Information Gaps: Detailed data on the app’s operational effectiveness and user adoption rates; clarity on data privacy measures implemented within the app.
- Bias & Deception Risks: Potential government bias in reporting app success; risk of underreporting privacy concerns; possible manipulation of app functionalities for surveillance.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of government interventions in the tech sector and affect India’s international relations concerning digital privacy standards.
- Political / Geopolitical: Potential strain on India’s relations with countries advocating for digital privacy; domestic political debates on privacy rights.
- Security / Counter-Terrorism: Enhanced ability to detect and prevent telecom-based fraud and illegal activities, potentially reducing national security threats.
- Cyber / Information Space: Increased government presence in the digital space may lead to debates on cybersecurity versus privacy; potential for cyber resistance or hacking attempts against the app.
- Economic / Social: Possible impact on the secondhand mobile market; public perception of government overreach may affect social trust in digital initiatives.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor user feedback and adoption rates; assess app’s impact on fraud reduction; engage with privacy advocates to address concerns.
- Medium-Term Posture (1–12 months): Develop partnerships with tech companies to enhance app features; implement transparency measures to build public trust; prepare for potential regulatory challenges.
- Scenario Outlook:
- Best: Successful reduction in telecom fraud with high user acceptance.
- Worst: Public backlash over privacy concerns leading to policy reversals.
- Most-Likely: Gradual improvement in fraud prevention with ongoing privacy debates.
6. Key Individuals and Entities
- Jyotiraditya Scindia – India’s Telecom Minister
- Ministry of Communications, Government of India
- Major mobile device manufacturers (not specifically named)
7. Thematic Tags
Cybersecurity, telecom fraud, government surveillance, privacy concerns, mobile technology, national security, digital policy
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us