Microsoft Patch Tuesday for November 2025 Snort rules and prominent vulnerabilities – Talosintelligence.com
Published on: 2025-11-11
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Microsoft Patch Tuesday for November 2025 Snort rules and prominent vulnerabilities – Talosintelligence.com
1. BLUF (Bottom Line Up Front)
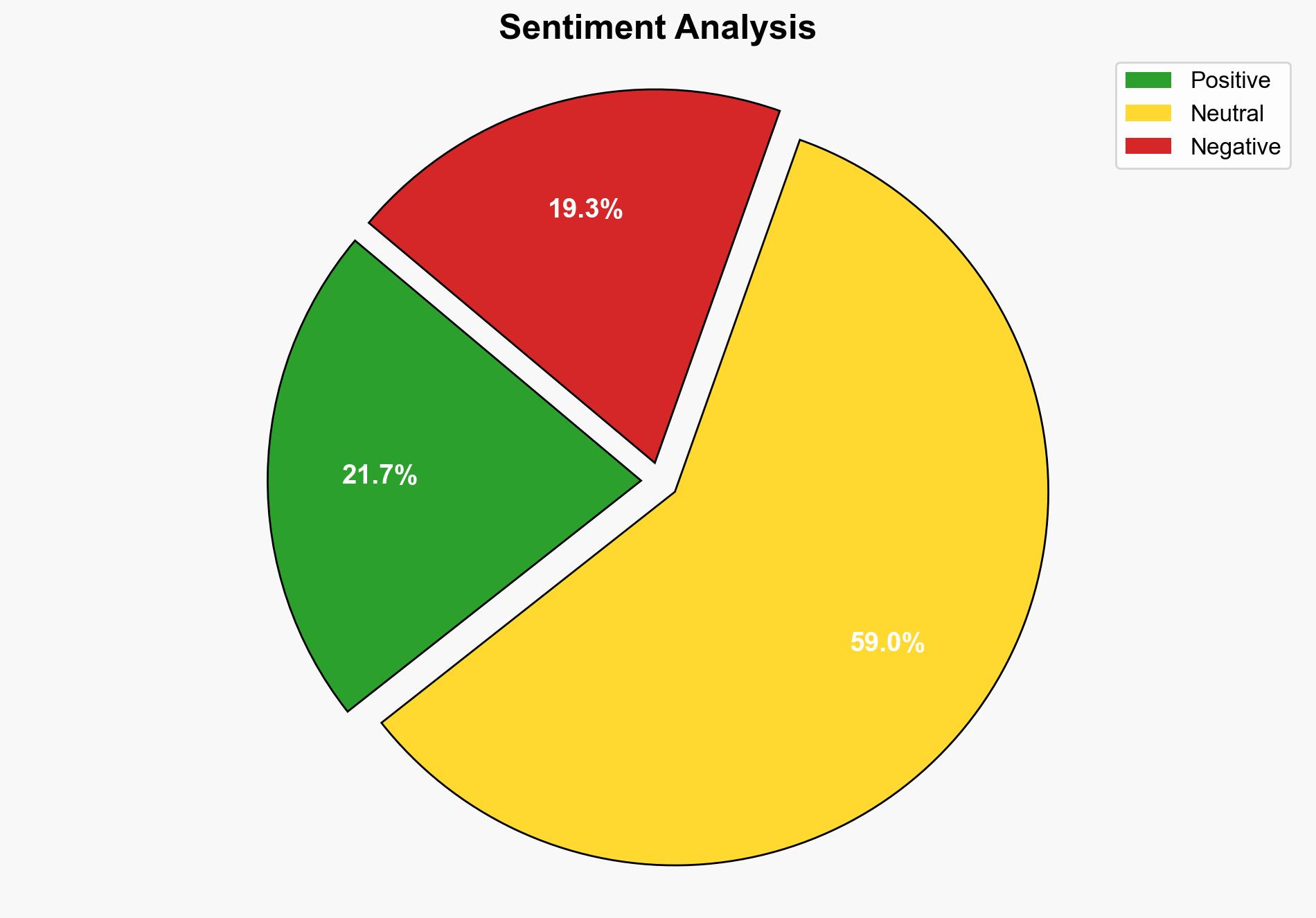
It is assessed with moderate confidence that the November 2025 Microsoft Patch Tuesday update addresses critical vulnerabilities that could be exploited by threat actors to compromise systems. The most supported hypothesis is that the vulnerabilities are being actively targeted by cybercriminals, necessitating immediate patching and enhanced monitoring. Recommended actions include prioritizing the application of patches and increasing network monitoring for signs of exploitation.
2. Competing Hypotheses
Hypothesis 1: The vulnerabilities disclosed in the November 2025 Patch Tuesday are being actively exploited by threat actors, necessitating immediate action to mitigate potential breaches.
Hypothesis 2: The vulnerabilities, while critical, are not yet being exploited in the wild, allowing organizations some time to test and deploy patches without immediate risk of exploitation.
Hypothesis 1 is more supported due to the nature of the vulnerabilities and historical patterns of rapid exploitation following Patch Tuesday disclosures. The presence of Snort rules suggests active monitoring for exploitation attempts.
3. Key Assumptions and Red Flags
Assumptions include the belief that threat actors have the capability and intent to exploit these vulnerabilities quickly. A red flag is the potential for misinformation or incomplete disclosure from Microsoft or other stakeholders. Deception indicators could involve threat actors using obfuscation techniques to mask exploitation activities.
4. Implications and Strategic Risks
The primary implication is the increased risk of cyberattacks targeting unpatched systems, which could lead to data breaches, financial loss, and reputational damage. Strategic risks include potential escalation in cyber conflict if state-sponsored actors exploit these vulnerabilities. Economic impacts could arise from disruptions in business operations.
5. Recommendations and Outlook
- Immediately apply the November 2025 patches to all vulnerable systems.
- Enhance network monitoring to detect signs of exploitation, using updated Snort rules.
- Conduct a risk assessment to prioritize patching efforts based on asset criticality.
- Best-case scenario: Patches are applied swiftly, and no significant exploitation occurs.
- Worst-case scenario: Widespread exploitation leads to major data breaches and operational disruptions.
- Most-likely scenario: Some exploitation occurs, but timely patching mitigates widespread impact.
6. Key Individuals and Entities
Microsoft (patch issuer), Talos Intelligence (vulnerability analysis), Cloudflare (security service provider).
7. Thematic Tags
Cybersecurity
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Methodology