Microsoft Patches Critical ASPNET Core Vulnerability with 99 Severity Score – InfoQ.com
Published on: 2025-11-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Microsoft Patches Critical ASPNET Core Vulnerability with 99 Severity Score – InfoQ.com
1. BLUF (Bottom Line Up Front)
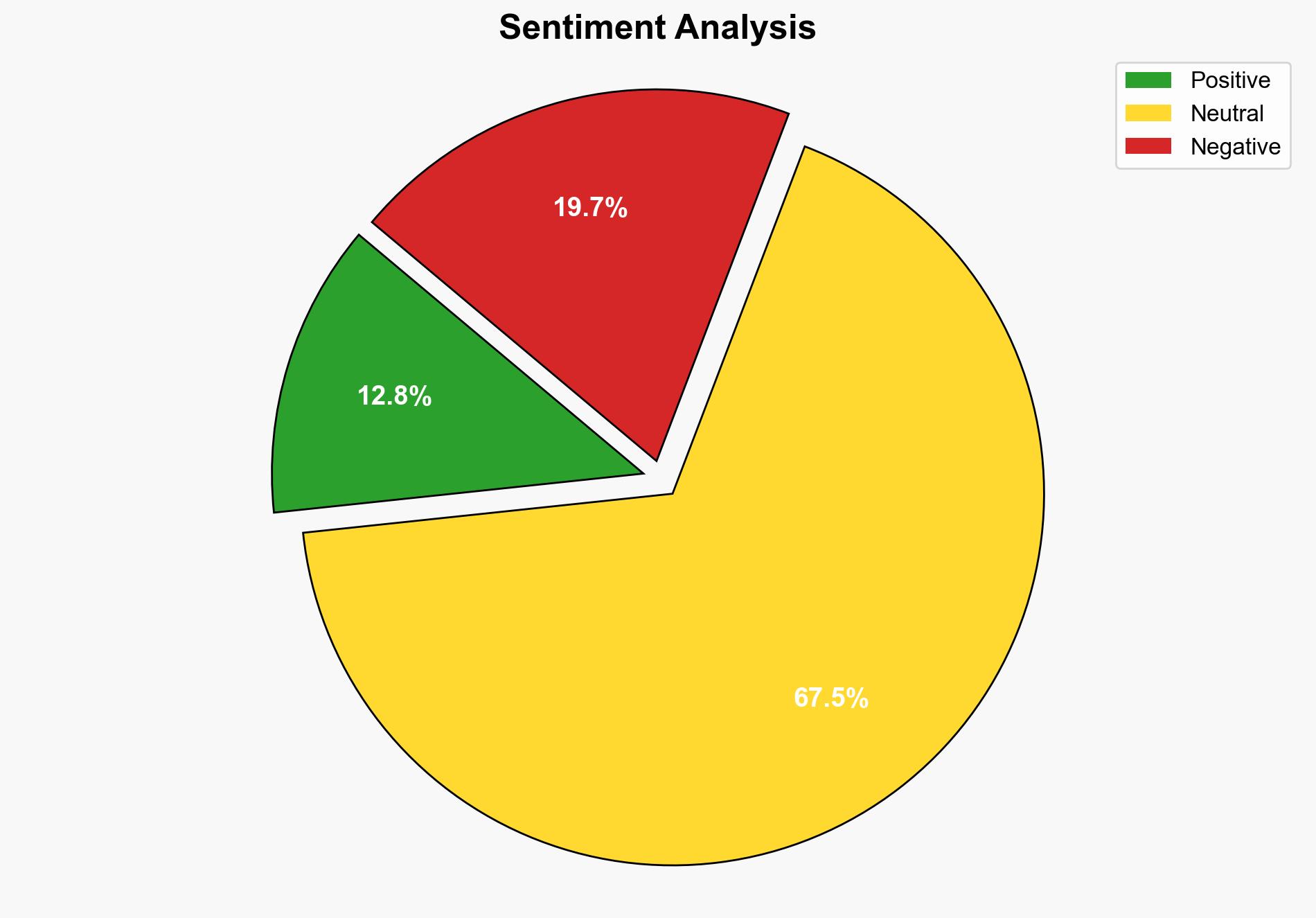
With a high confidence level, the most supported hypothesis is that the critical ASP.NET Core vulnerability represents a significant risk to applications using the Kestrel server, potentially allowing for privilege escalation and other attacks. Immediate patching is recommended to mitigate this risk.
2. Competing Hypotheses
Hypothesis 1: The vulnerability in ASP.NET Core is a severe threat that could lead to widespread exploitation if not promptly patched. This is supported by the high CVSS score and the nature of the vulnerability, which involves HTTP request smuggling.
Hypothesis 2: The vulnerability, while critical, is unlikely to be widely exploited due to mitigating factors such as specific server configurations and the need for precise conditions to be met for successful exploitation.
Hypothesis 1 is more likely due to the high severity score and the potential for privilege escalation, which could have significant impacts on affected systems.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that most organizations using ASP.NET Core are aware of the vulnerability and have the capability to apply patches promptly. It is also assumed that the vulnerability is not already being exploited at scale.
Red Flags: A potential red flag is the initial confusion among developers regarding the affected versions, which could delay patching. Additionally, the reliance on third-party proxies could introduce further complexity in mitigating the vulnerability.
4. Implications and Strategic Risks
The vulnerability could lead to cascading threats such as unauthorized access to sensitive data, system compromise, and further cyber-attacks leveraging privilege escalation. Economically, organizations could face financial losses due to data breaches and reputational damage. Politically, there could be increased scrutiny on software security practices.
5. Recommendations and Outlook
- Actionable Steps: Organizations should immediately apply the recommended patches and verify their proxy configurations to prevent HTTP request smuggling. Regular security audits and monitoring for unusual activity are advised.
- Best-case Scenario: The vulnerability is patched swiftly across all affected systems, preventing any significant exploitation.
- Worst-case Scenario: Delays in patching lead to widespread exploitation, resulting in significant data breaches and system compromises.
- Most-likely Scenario: While some systems may be exploited due to delayed patching, the majority will be secured in a timely manner, minimizing overall impact.
6. Key Individuals and Entities
Barry Dorrans, Security TPM at Microsoft; Andrew Lock, Staff Engineer at Datadog; Hayden Barne, Senior Open Source Partner Manager at Herodevs.
7. Thematic Tags
Cybersecurity
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
- Network Influence Mapping: Map influence relationships to assess actor impact.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Methodology