SAP fixes serious security issues – here’s how to stay safe – TechRadar
Published on: 2025-11-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: SAP fixes serious security issues – here’s how to stay safe – TechRadar
1. BLUF (Bottom Line Up Front)
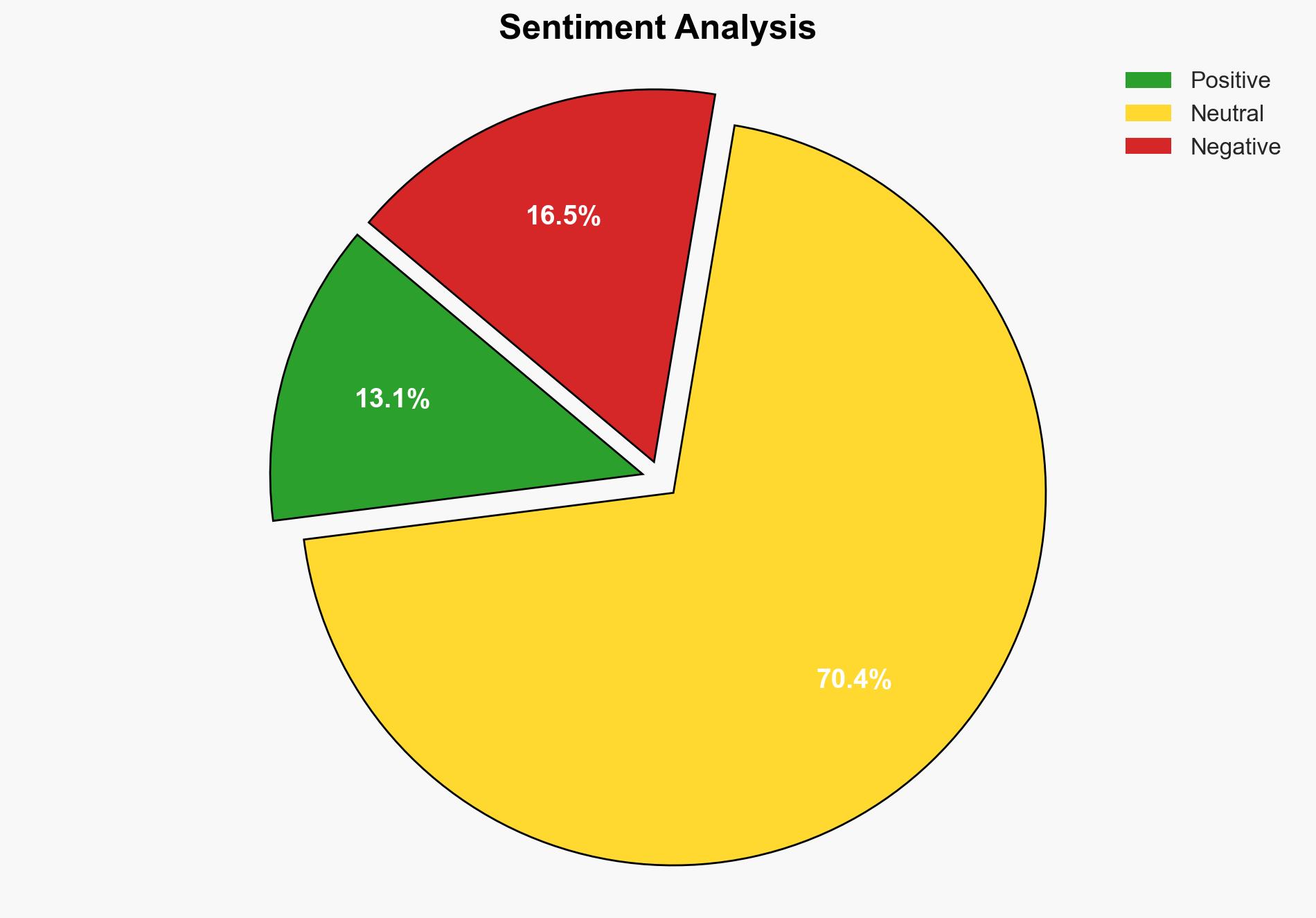
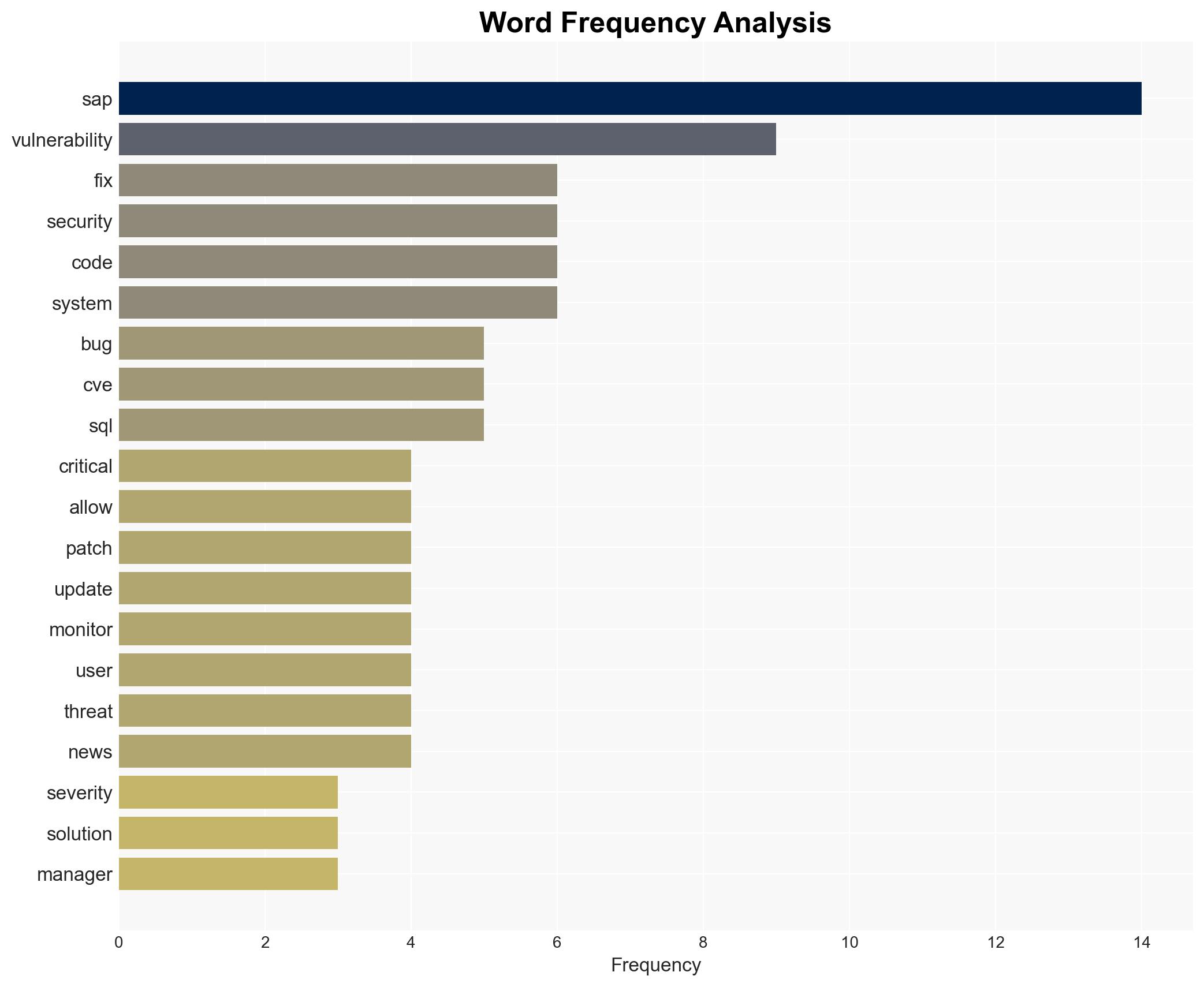
The most supported hypothesis is that SAP’s recent security patch addresses critical vulnerabilities that, if left unpatched, could lead to significant system compromises. The strategic recommendation is for organizations using SAP systems to prioritize the immediate application of these patches to mitigate potential cyber threats. Confidence Level: High.
2. Competing Hypotheses
Hypothesis 1: SAP’s security patch effectively mitigates the identified vulnerabilities, and organizations that apply the patch promptly will significantly reduce their risk of cyber attacks.
Hypothesis 2: Despite the patch, there may be residual vulnerabilities or new exploits that attackers could leverage, meaning the risk remains high even after patch application.
Hypothesis 1 is more likely due to the comprehensive nature of the patch and the urgency communicated by security experts. However, Hypothesis 2 cannot be entirely dismissed due to the potential for rapid exploit development and the complexity of SAP systems.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that the patch addresses all known vulnerabilities effectively and that organizations have the capability to implement the patch promptly.
Red Flags: The speed of reverse engineering and exploit development post-patch release is a concern. Additionally, the reliance on organizations to act swiftly may not be uniformly met, increasing risk for those who delay.
Deception Indicators: There is no direct evidence of deception, but the possibility of undisclosed vulnerabilities remains a concern.
4. Implications and Strategic Risks
The primary risk is a cyber attack leading to system compromise, data breaches, and operational disruptions. Such incidents could have cascading effects, including financial losses, reputational damage, and regulatory penalties. In a broader context, widespread exploitation of SAP vulnerabilities could impact economic stability and national security, particularly if critical infrastructure is affected.
5. Recommendations and Outlook
- Actionable Steps: Organizations should immediately apply the SAP patch, conduct a thorough security audit, and enhance monitoring for unusual activities post-patch.
- Best Scenario: The patch is applied universally and effectively, leading to a significant reduction in vulnerabilities.
- Worst Scenario: New vulnerabilities are discovered, or the patch is ineffective, leading to widespread system compromises.
- Most-likely Scenario: The patch mitigates most risks, but some organizations may still face threats due to delayed implementation or residual vulnerabilities.
6. Key Individuals and Entities
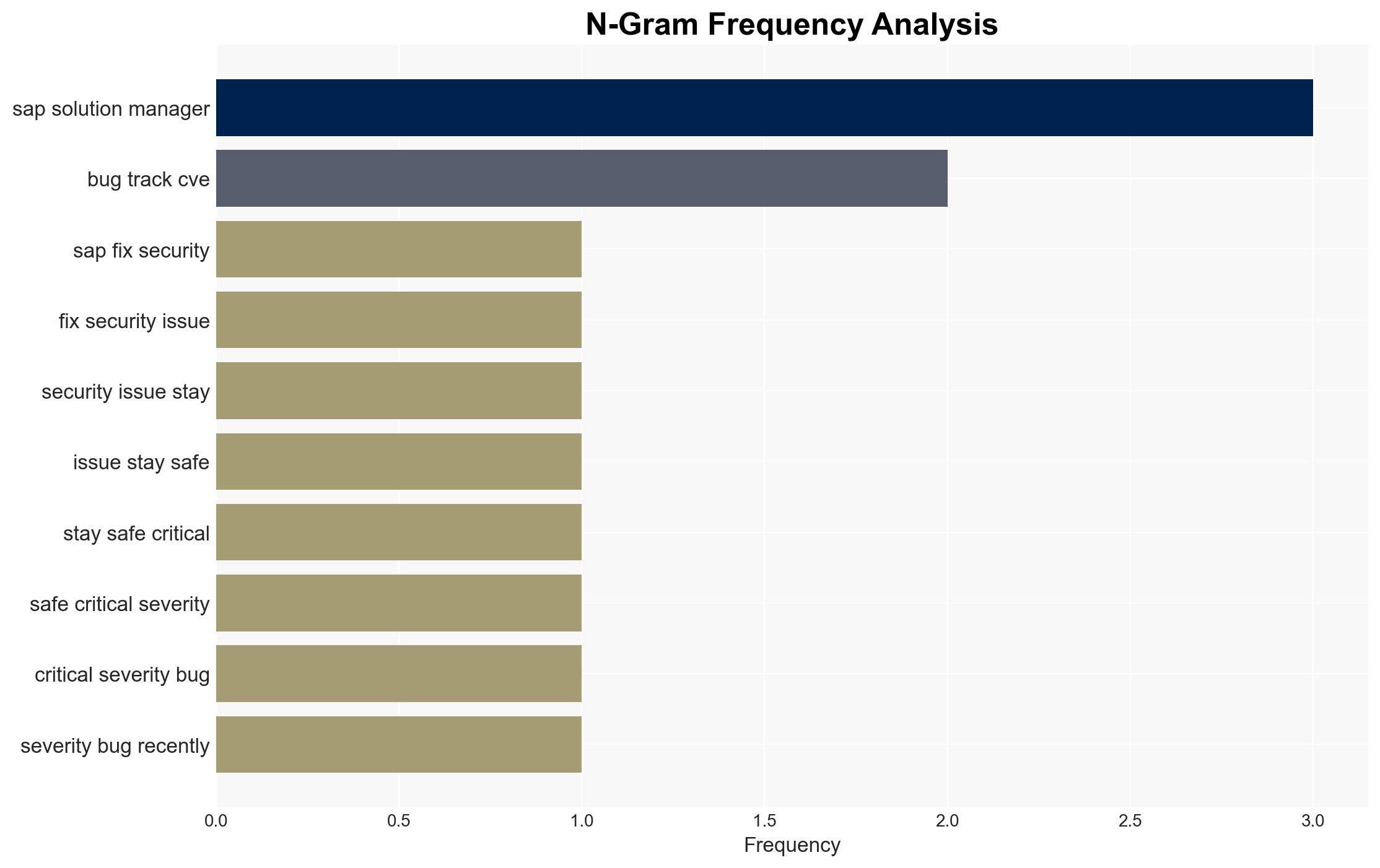
Joris van de Vis, Director of Security Research at SecurityBridge, is a key individual providing expert insights into the vulnerabilities and the importance of the patch.
7. Thematic Tags
Cybersecurity
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Methodology