University of Pennsylvania confirms recent cyberattack led to major data theft – TechRadar
Published on: 2025-11-06
Intelligence Report: University of Pennsylvania confirms recent cyberattack led to major data theft – TechRadar
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that the cyberattack on the University of Pennsylvania was primarily facilitated by weak multi-factor authentication (MFA) protocols and social engineering tactics targeting senior staff. Confidence level is moderate due to the complexity of cyber incidents and potential for misinformation. Immediate action should focus on strengthening cybersecurity protocols and conducting a thorough investigation to identify and mitigate vulnerabilities.
2. Competing Hypotheses
1. **Hypothesis A**: The cyberattack was executed by a sophisticated group exploiting weak MFA enforcement and social engineering to gain access to sensitive data.
2. **Hypothesis B**: The attack was an opportunistic breach by less organized cybercriminals, leveraging publicly available information and exploiting basic security lapses.
Using ACH 2.0, Hypothesis A is better supported due to the detailed nature of the data stolen and the targeted approach suggested by the social engineering tactics. Hypothesis B lacks support as the attack’s complexity suggests a higher level of planning and execution.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the attackers had prior knowledge of the university’s security weaknesses. Another assumption is that the breach’s timing was opportunistic, possibly linked to recent public controversies.
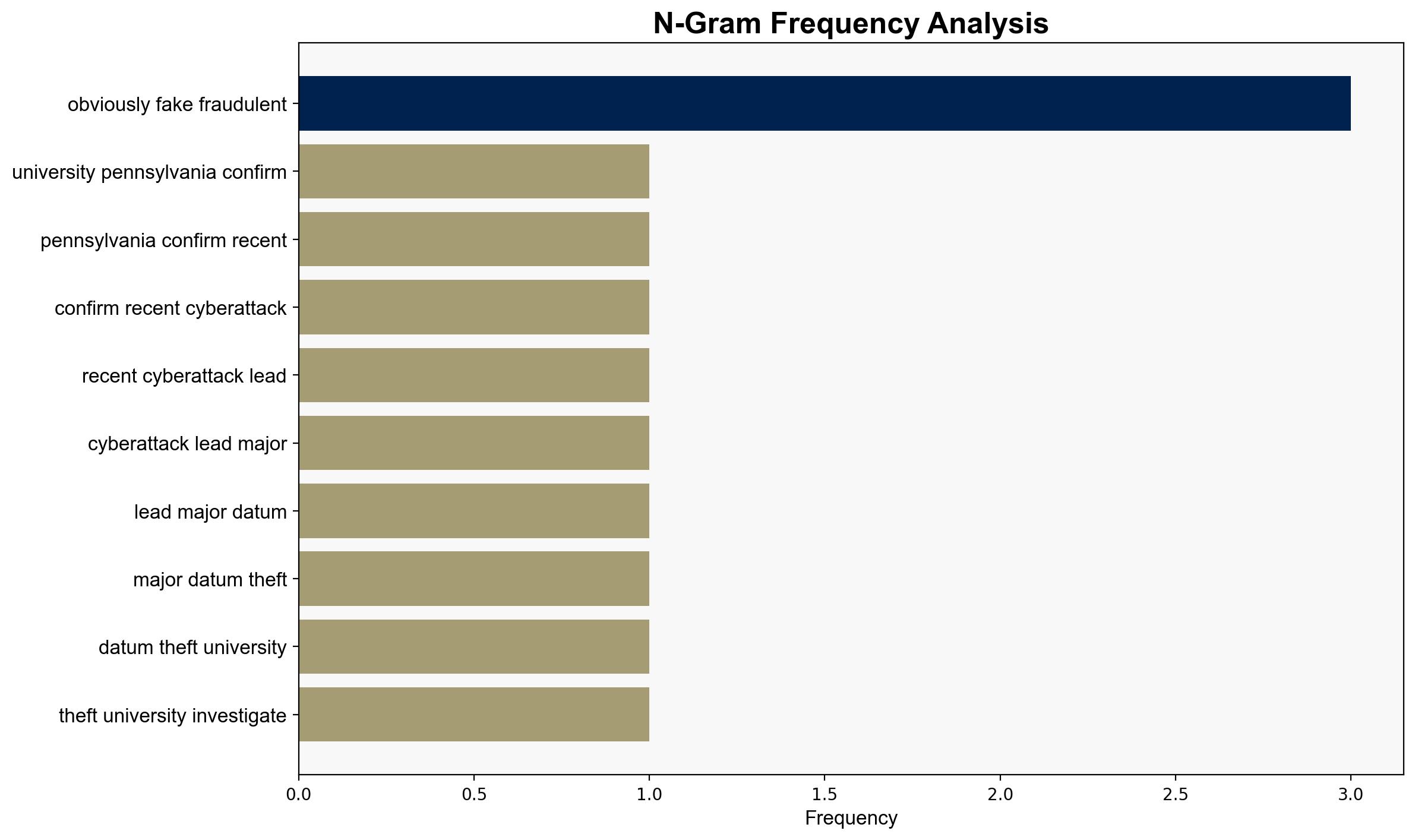
– **Red Flags**: The claim of “obviously fake fraudulent” emails could indicate an attempt to downplay the attack’s severity. The rapid lockout of systems suggests potential prior knowledge of vulnerabilities.
– **Blind Spots**: Lack of detailed information on the attackers’ identity and motivations. The potential involvement of insider threats is not addressed.
4. Implications and Strategic Risks
The breach exposes the university to significant reputational damage and potential legal liabilities, particularly concerning data privacy laws. There is a risk of further attacks if vulnerabilities are not addressed. The incident could embolden other cybercriminals, leading to a possible increase in similar attacks on educational institutions.
5. Recommendations and Outlook
- Enhance MFA protocols and conduct regular cybersecurity audits.
- Implement comprehensive training for staff on recognizing and preventing social engineering attacks.
- Scenario Projections:
- **Best Case**: Immediate mitigation measures prevent further breaches, and the university restores its reputation through transparent communication.
- **Worst Case**: Additional vulnerabilities are exploited, leading to further data breaches and significant financial and reputational damage.
- **Most Likely**: The university strengthens its cybersecurity posture, but faces ongoing challenges in fully securing its systems.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. The focus remains on the University of Pennsylvania and the unidentified cybercriminals involved.
7. Thematic Tags
national security threats, cybersecurity, data breach, educational institutions