16 Billion Exposed The Terrifying Data Breach and What You Can Do – Nextpit.com
Published on: 2025-06-20
Intelligence Report: 16 Billion Exposed – The Terrifying Data Breach and What You Can Do
1. BLUF (Bottom Line Up Front)
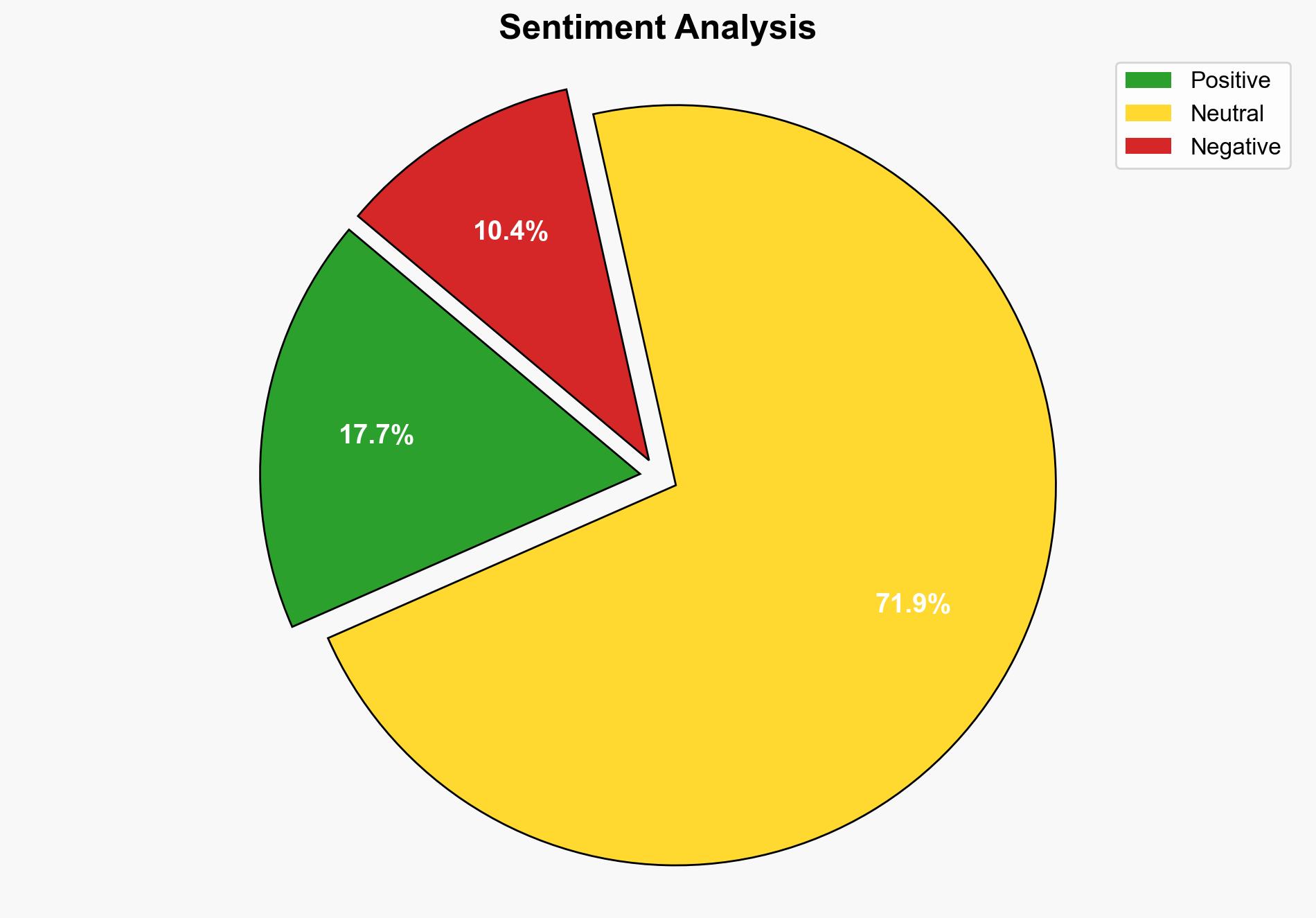
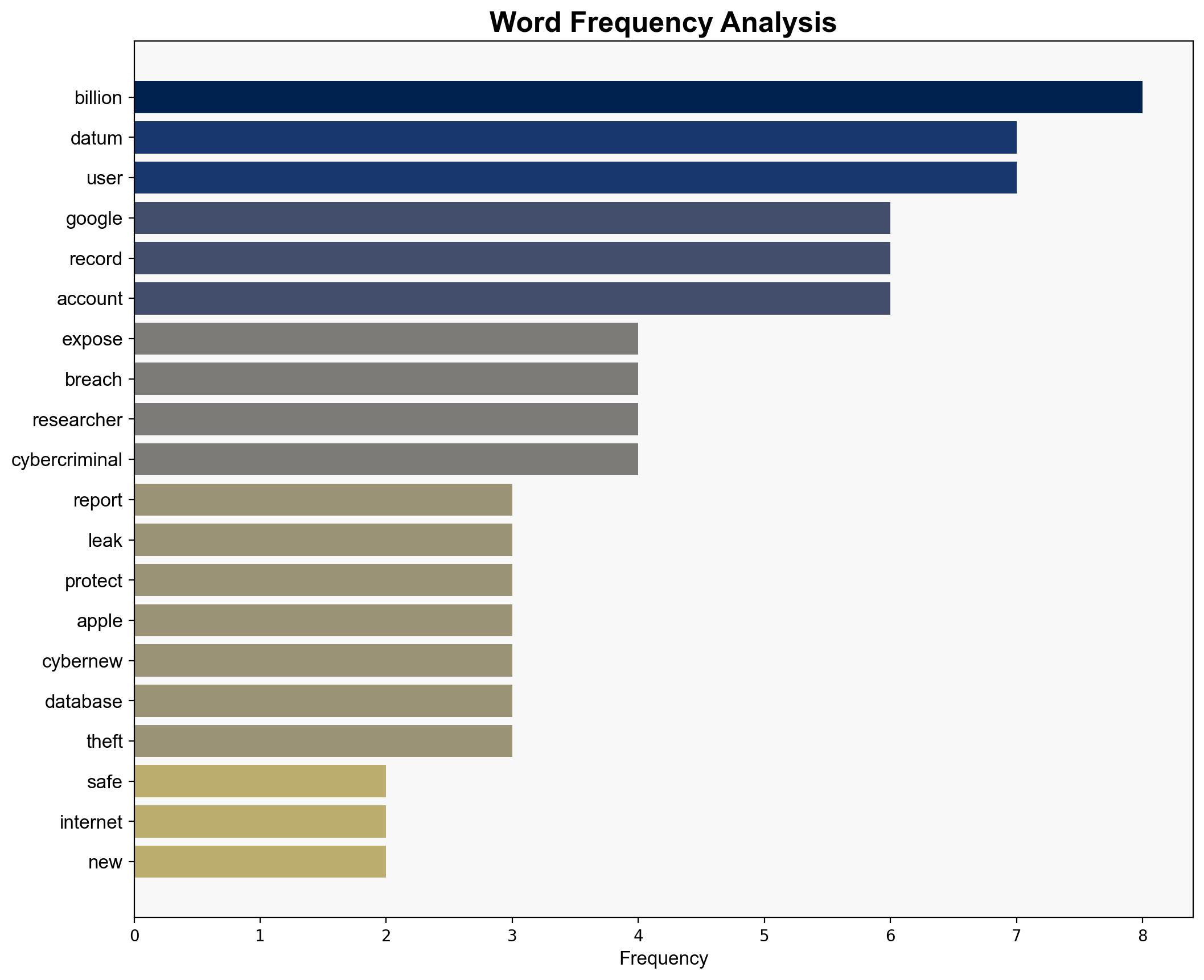
A massive data breach has exposed 16 billion records, primarily containing login credentials for major brands like Google, Apple, and Facebook. This breach poses significant risks of identity theft, account takeovers, and financial fraud. Immediate action is required to enhance cybersecurity measures, including the adoption of multi-factor authentication and regular password updates.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations indicate that cyber adversaries could exploit these credentials for targeted phishing campaigns and identity theft. Organizations must anticipate these actions to bolster defenses.
Indicators Development
Monitoring for anomalies in login patterns and unauthorized access attempts is crucial for early detection of potential breaches.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of increased cyberattacks targeting compromised accounts, necessitating robust security protocols.
3. Implications and Strategic Risks
The breach highlights systemic vulnerabilities in data storage and protection practices. The potential for cascading effects includes increased cybercrime rates and economic impacts due to fraud. Cross-domain risks involve potential exploitation by state-sponsored actors for espionage or disruption.
4. Recommendations and Outlook
- Implement multi-factor authentication across all platforms to reduce unauthorized access risks.
- Regularly update passwords and employ advanced security features like passkeys.
- Best Case: Enhanced security measures prevent further exploitation, and affected users secure their accounts.
- Worst Case: Widespread identity theft and financial fraud lead to significant economic losses and erosion of trust in digital platforms.
- Most Likely: A mixed outcome where some users and organizations effectively mitigate risks, while others remain vulnerable.
5. Key Individuals and Entities
No specific individuals are mentioned in the source text. Entities involved include Google, Apple, Facebook, and various VPN providers.
6. Thematic Tags
national security threats, cybersecurity, data breach, identity theft, cybercrime