16B Apple Facebook Google passwords leaked in largest data breach – Cryptorank.io
Published on: 2025-06-19
Intelligence Report: 16B Apple Facebook Google passwords leaked in largest data breach – Cryptorank.io
1. BLUF (Bottom Line Up Front)
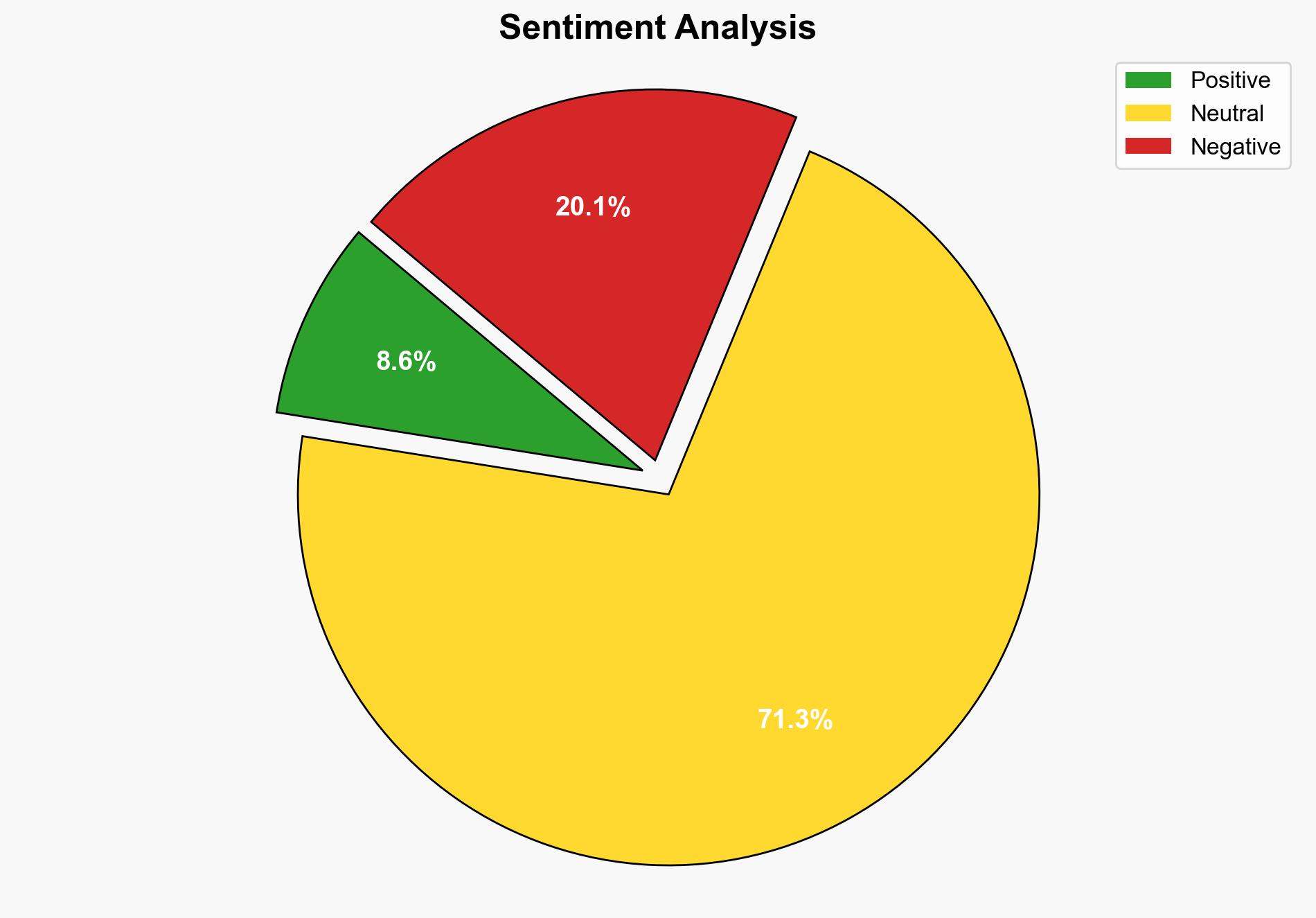
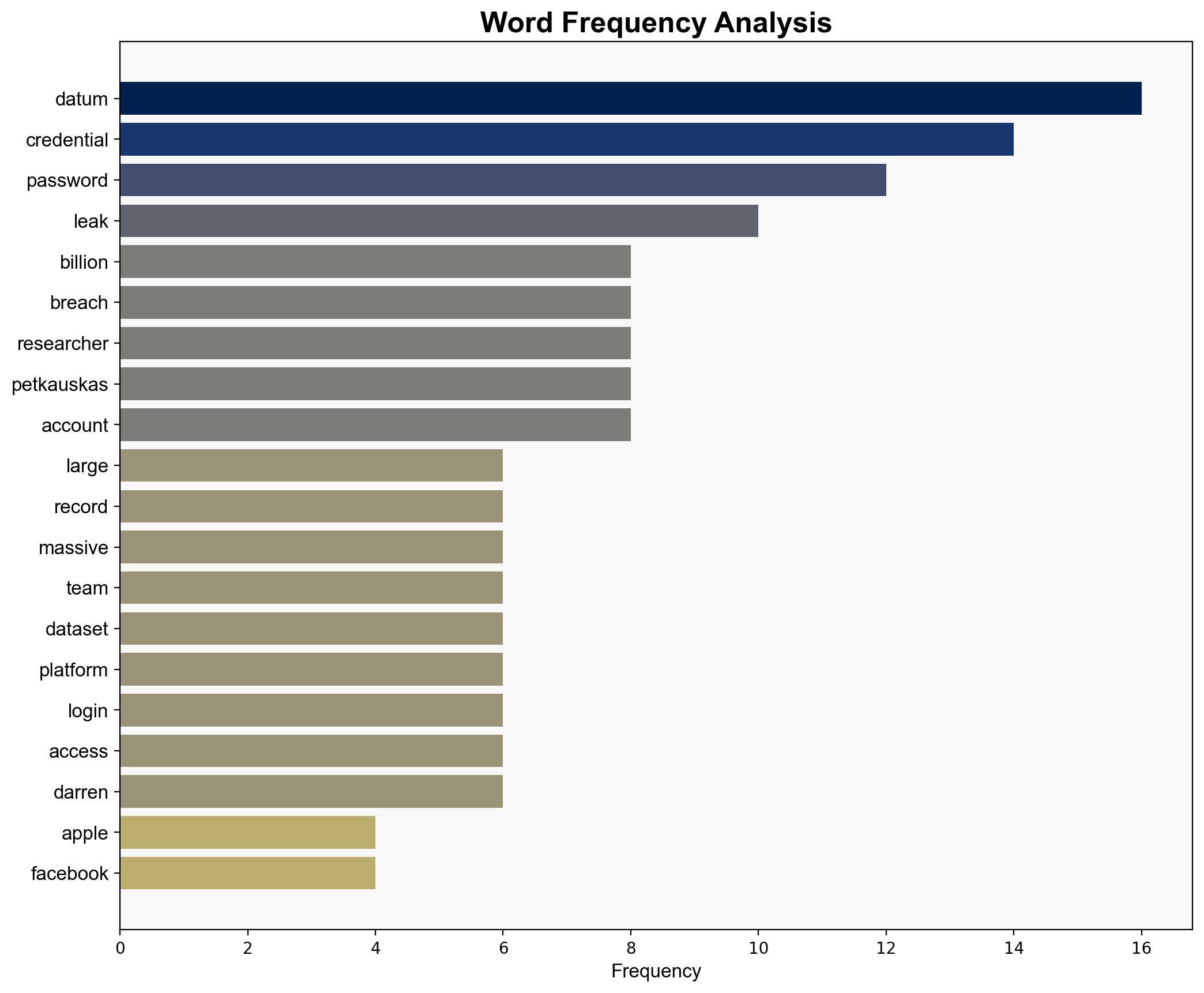
A significant data breach has exposed 16 billion passwords from major platforms including Apple, Facebook, and Google. This breach poses severe risks of mass account takeovers, phishing campaigns, and credential stuffing attacks. Immediate action is required to mitigate potential exploitation and safeguard affected systems.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations suggest that cyber adversaries could exploit the leaked credentials to gain unauthorized access to personal and corporate systems, potentially leading to data theft and service disruptions.
Indicators Development
Monitoring for unusual login attempts and changes in user behavior across platforms is essential for early detection of unauthorized access attempts.
Bayesian Scenario Modeling
Probabilistic models indicate a high likelihood of increased phishing and credential stuffing attacks in the short term, with potential long-term impacts on user trust and platform security.
3. Implications and Strategic Risks
The breach highlights systemic vulnerabilities in data protection practices, particularly concerning cloud storage and access controls. The scale of the breach could lead to widespread economic impacts, undermine public trust in digital services, and increase geopolitical tensions if state actors are involved.
4. Recommendations and Outlook
- Implement multi-factor authentication across all affected platforms to reduce the risk of unauthorized access.
- Conduct comprehensive security audits of cloud storage configurations and access controls.
- Develop and deploy user education campaigns to raise awareness about phishing and credential security.
- Scenario Projections:
- Best Case: Rapid containment and mitigation efforts prevent widespread exploitation.
- Worst Case: Prolonged exploitation leads to significant financial losses and reputational damage.
- Most Likely: Increased short-term attacks with gradual improvement in security posture over time.
5. Key Individuals and Entities
Vilius Petkauskas, Darren Guccione
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus