2025 Cybersecurity Reality Check Breaches Hidden Attack Surfaces Growing and AI Misperceptions Rising – Internet
Published on: 2025-10-01
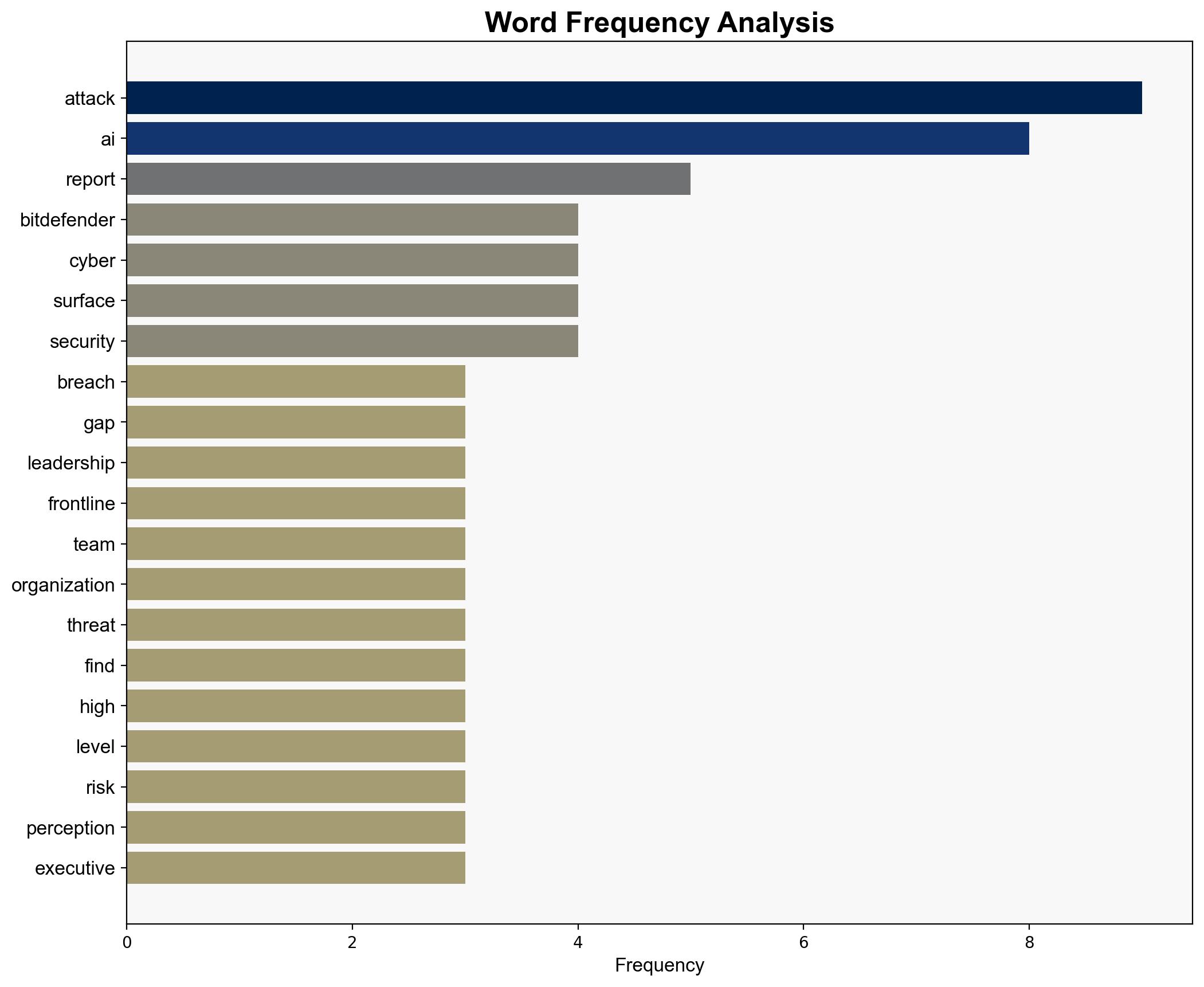
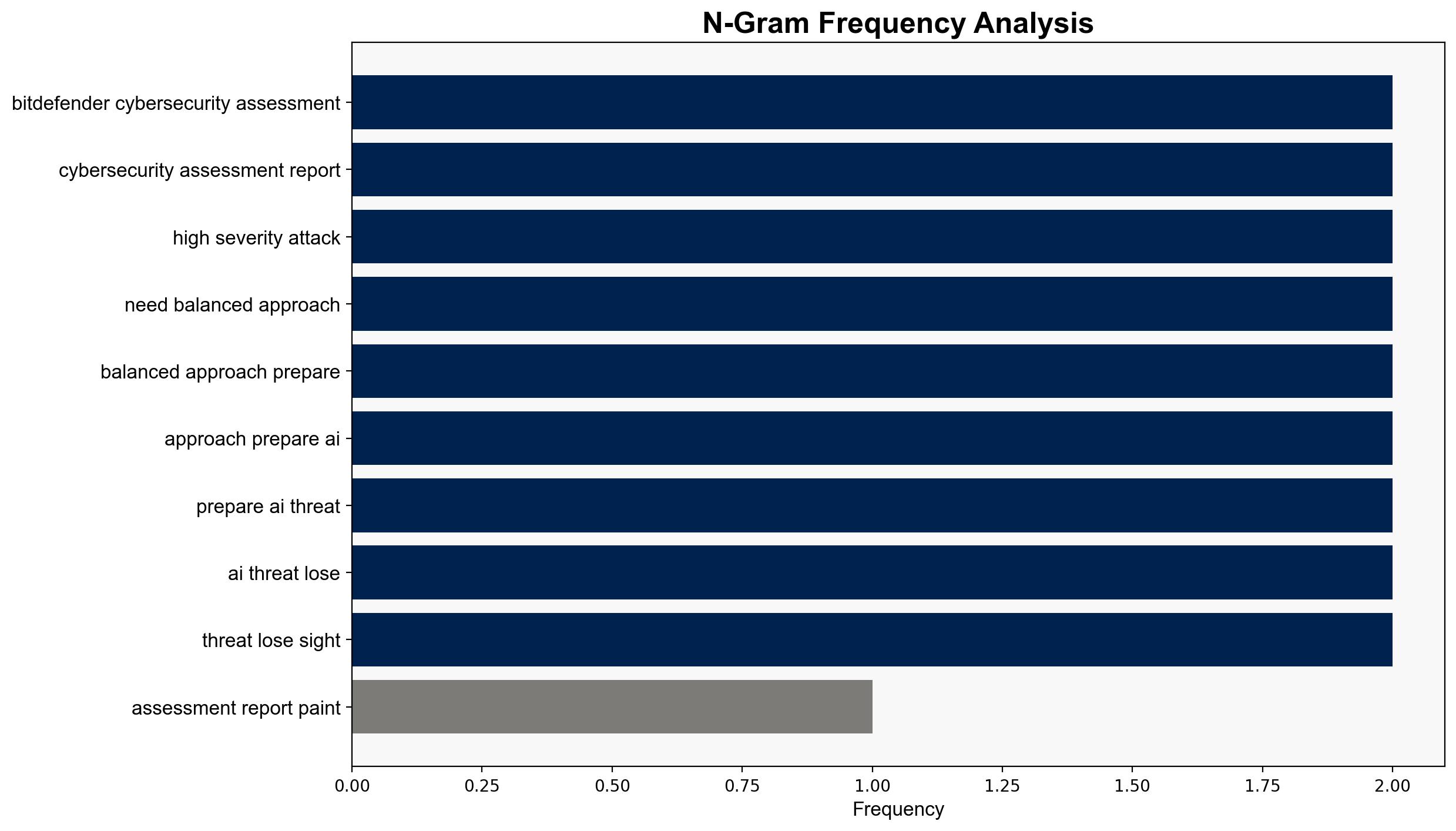
Intelligence Report: 2025 Cybersecurity Reality Check Breaches Hidden Attack Surfaces Growing and AI Misperceptions Rising – Internet
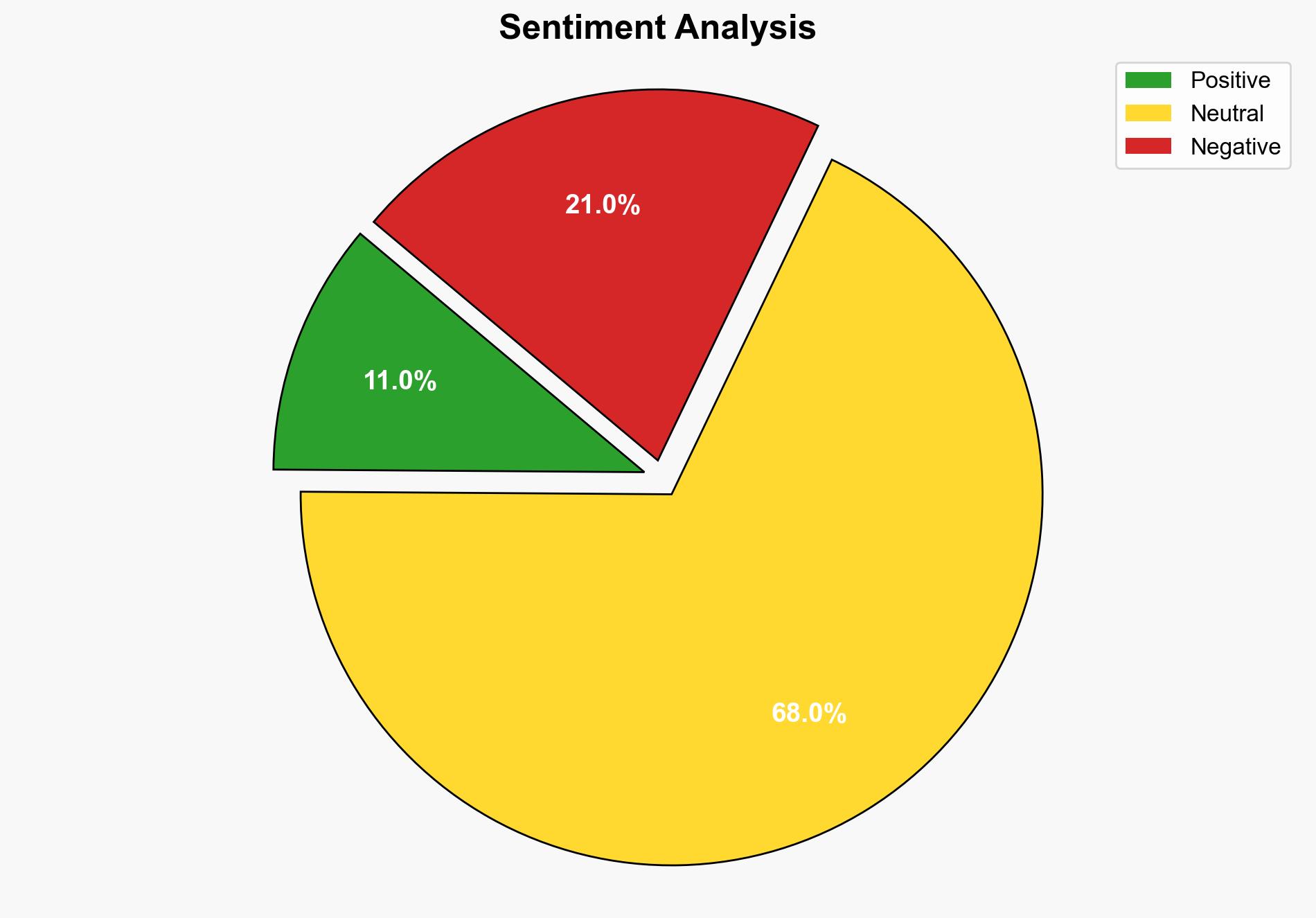
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that organizations are underestimating the complexity of their attack surfaces and overestimating the immediate threat posed by AI-driven attacks. This misalignment in threat perception and response strategy could lead to increased vulnerability. Confidence Level: Moderate. Recommended action includes prioritizing attack surface reduction and aligning leadership and operational teams on realistic AI threat assessments.
2. Competing Hypotheses
1. **Hypothesis A**: Organizations are primarily focused on AI threats, neglecting the more immediate and prevalent risks associated with complex attack surfaces and live-off-the-land (LotL) techniques.
2. **Hypothesis B**: The emphasis on AI threats is justified as AI-driven attacks are rapidly evolving and pose a significant future risk, necessitating preemptive focus despite current prevalence.
Using ACH 2.0, Hypothesis A is better supported due to the evidence of a disconnect between leadership and frontline perceptions, and the current prevalence of LotL techniques over AI-driven attacks.
3. Key Assumptions and Red Flags
– **Assumptions**: Hypothesis A assumes that current attack vectors are more pressing than AI threats. Hypothesis B assumes rapid AI threat evolution.
– **Red Flags**: Potential bias in overemphasizing AI threats due to media and industry narrative. Lack of specific data on AI attack prevalence versus traditional methods.
– **Inconsistent Data**: Discrepancy between executive confidence in managing cyber risks and frontline observations.
4. Implications and Strategic Risks
– **Economic**: Misallocation of resources towards AI threats could lead to financial inefficiencies.
– **Cyber**: Increased vulnerability due to neglected attack surface management.
– **Geopolitical**: Potential exploitation by state actors leveraging LotL techniques.
– **Psychological**: Erosion of trust in leadership due to perceived misalignment and lack of transparency.
5. Recommendations and Outlook
- **Mitigation**: Enhance focus on reducing attack surfaces by disabling unnecessary services and applications.
- **Alignment**: Foster better communication and alignment between leadership and operational teams regarding threat priorities.
- **Scenario Projections**:
- **Best Case**: Organizations achieve balanced threat management, reducing vulnerabilities and optimizing resource allocation.
- **Worst Case**: Continued misalignment leads to significant breaches, eroding stakeholder trust and financial stability.
- **Most Likely**: Gradual improvement in attack surface management with ongoing challenges in AI threat perception.
6. Key Individuals and Entities
– Bitdefender (source of the report)
– CISOs and CIOs (referenced in the context of leadership expectations)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus