25 billion Gmail users at risk after Googles databases were hacked – PCWorld
Published on: 2025-08-18
Intelligence Report: 25 billion Gmail users at risk after Googles databases were hacked – PCWorld
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that the reported hacking incident is a sophisticated phishing campaign exploiting a data leak from Google’s Salesforce database. Confidence level: Moderate. Recommended action: Immediate enhancement of user security protocols and public awareness campaigns to mitigate phishing risks.
2. Competing Hypotheses
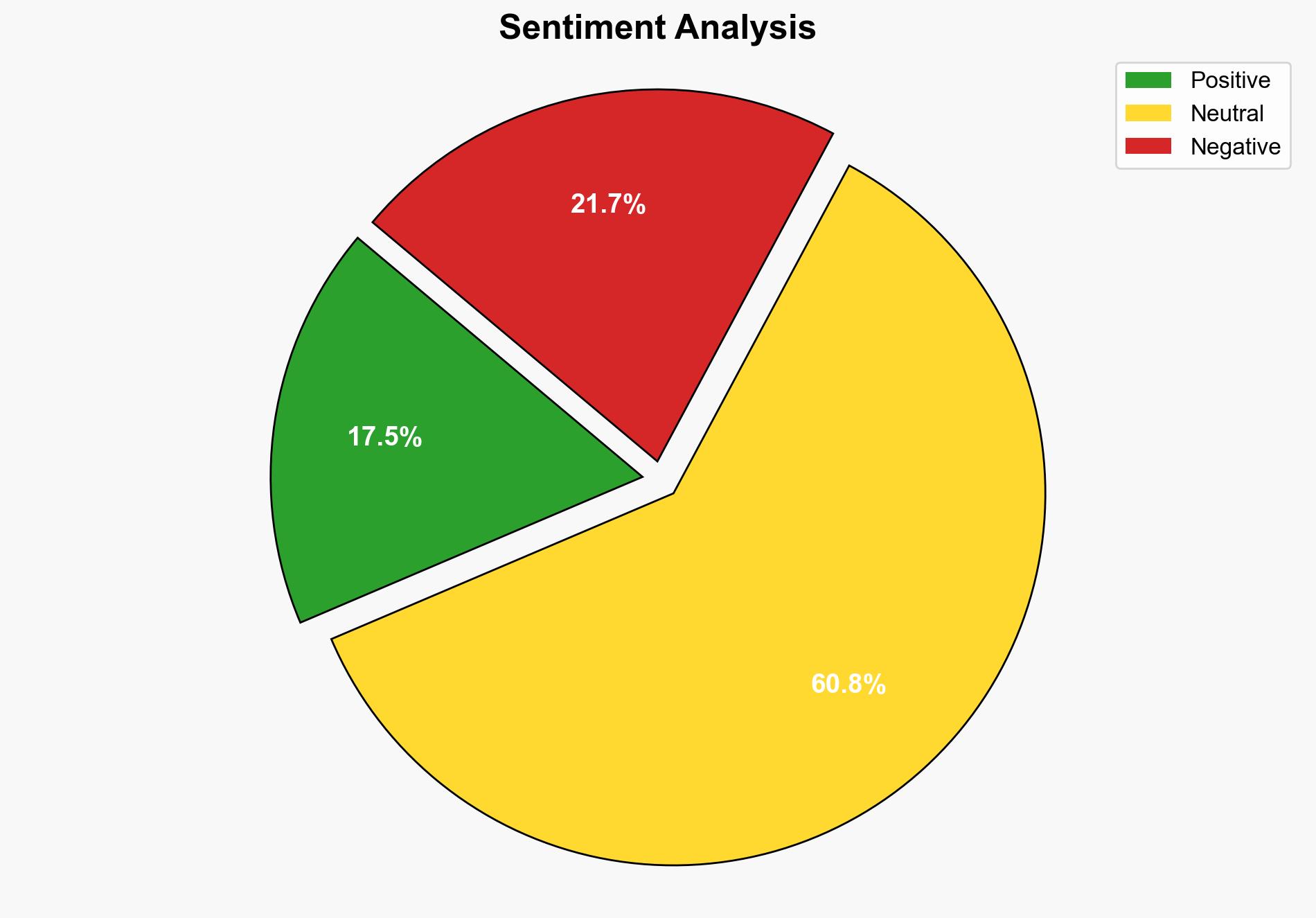
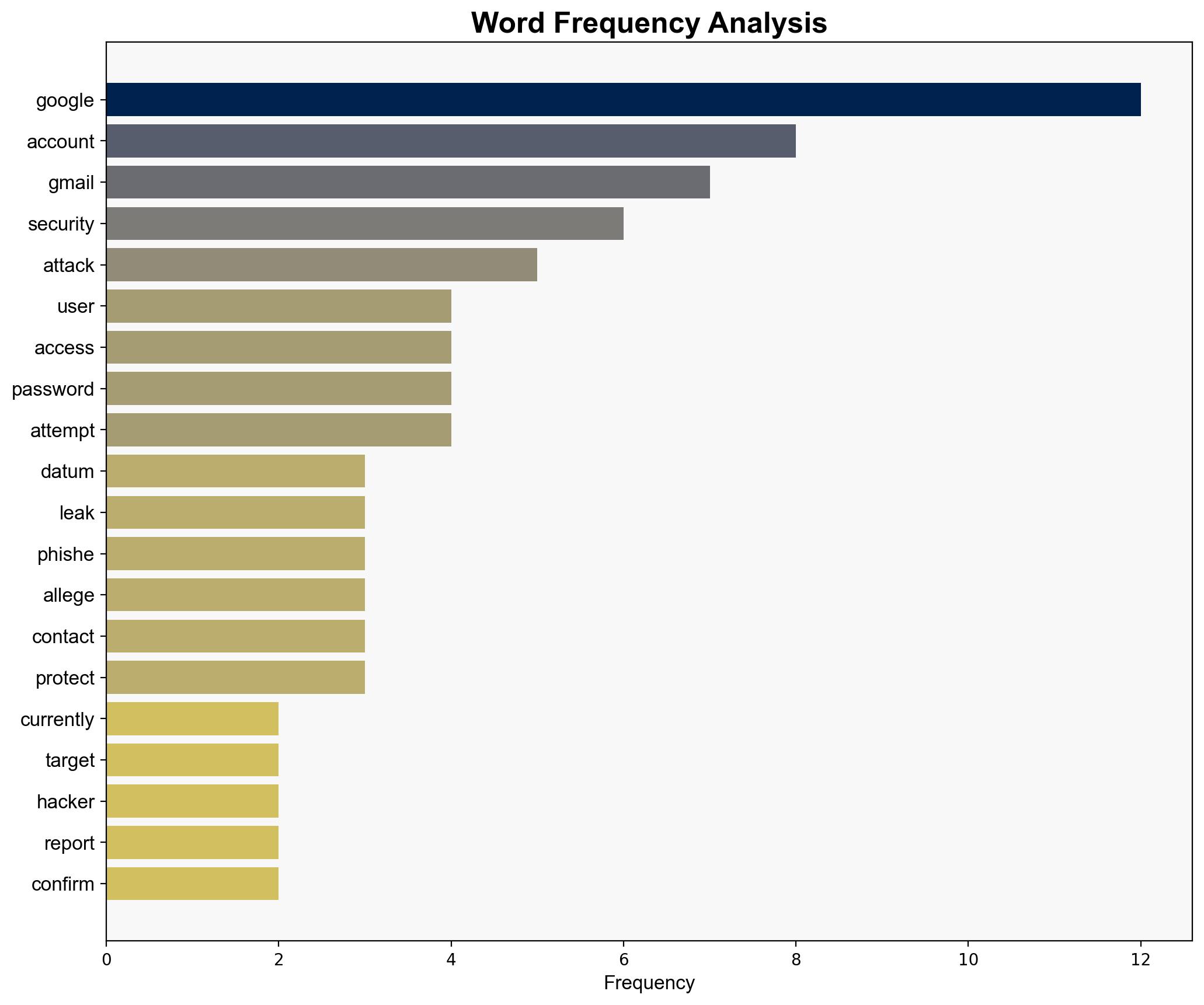
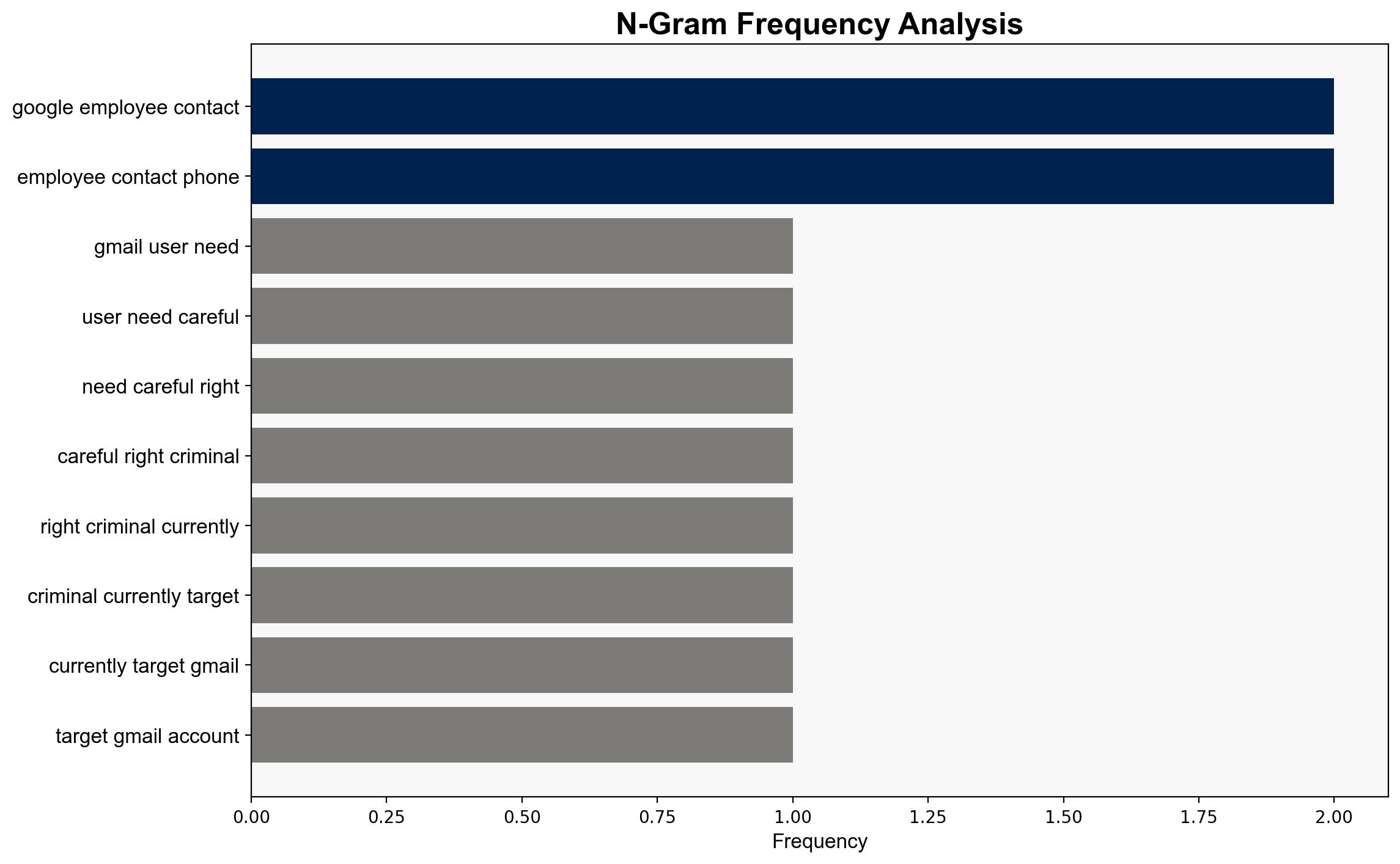
Hypothesis 1: The hacking incident is a large-scale phishing campaign exploiting leaked data from Google’s Salesforce database. This hypothesis is supported by reports of phishing attempts and the nature of the data accessed, which includes customer names and company information, useful for targeted phishing.
Hypothesis 2: The incident is a misinformation campaign aimed at undermining trust in Google’s security infrastructure. This hypothesis considers the possibility of exaggeration or fabrication of the breach details to damage Google’s reputation.
Using ACH 2.0, Hypothesis 1 is better supported due to the specific nature of the data accessed and the alignment with reported phishing activities. Hypothesis 2 lacks corroborative evidence and relies on speculative motives.
3. Key Assumptions and Red Flags
Assumptions:
– The data leak is genuine and not overstated.
– The phishing attempts are directly linked to the leaked data.
Red Flags:
– Lack of detailed confirmation from Google about the extent of the breach.
– Potential bias in reporting, as the source is a translated article.
4. Implications and Strategic Risks
The primary risk is a surge in phishing attacks targeting Gmail users, potentially leading to unauthorized access to sensitive information. Secondary risks include reputational damage to Google and increased scrutiny from regulatory bodies. Geopolitically, this could escalate tensions if state actors are suspected of involvement.
5. Recommendations and Outlook
- Enhance security measures, including two-factor authentication and advanced protection programs for users.
- Launch a public awareness campaign to educate users on phishing risks and security best practices.
- Scenario Projections:
- Best Case: Rapid containment of phishing attempts with minimal impact on users.
- Worst Case: Widespread data breaches leading to significant financial and reputational damage.
- Most Likely: Increased phishing attempts with moderate impact, mitigated by enhanced security measures.
6. Key Individuals and Entities
– ShinyHunter (hacker group)
– Google (entity)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus