25 billion Gmail users endangered after Google database hack – PCWorld
Published on: 2025-08-24
Intelligence Report: 25 billion Gmail users endangered after Google database hack – PCWorld
1. BLUF (Bottom Line Up Front)
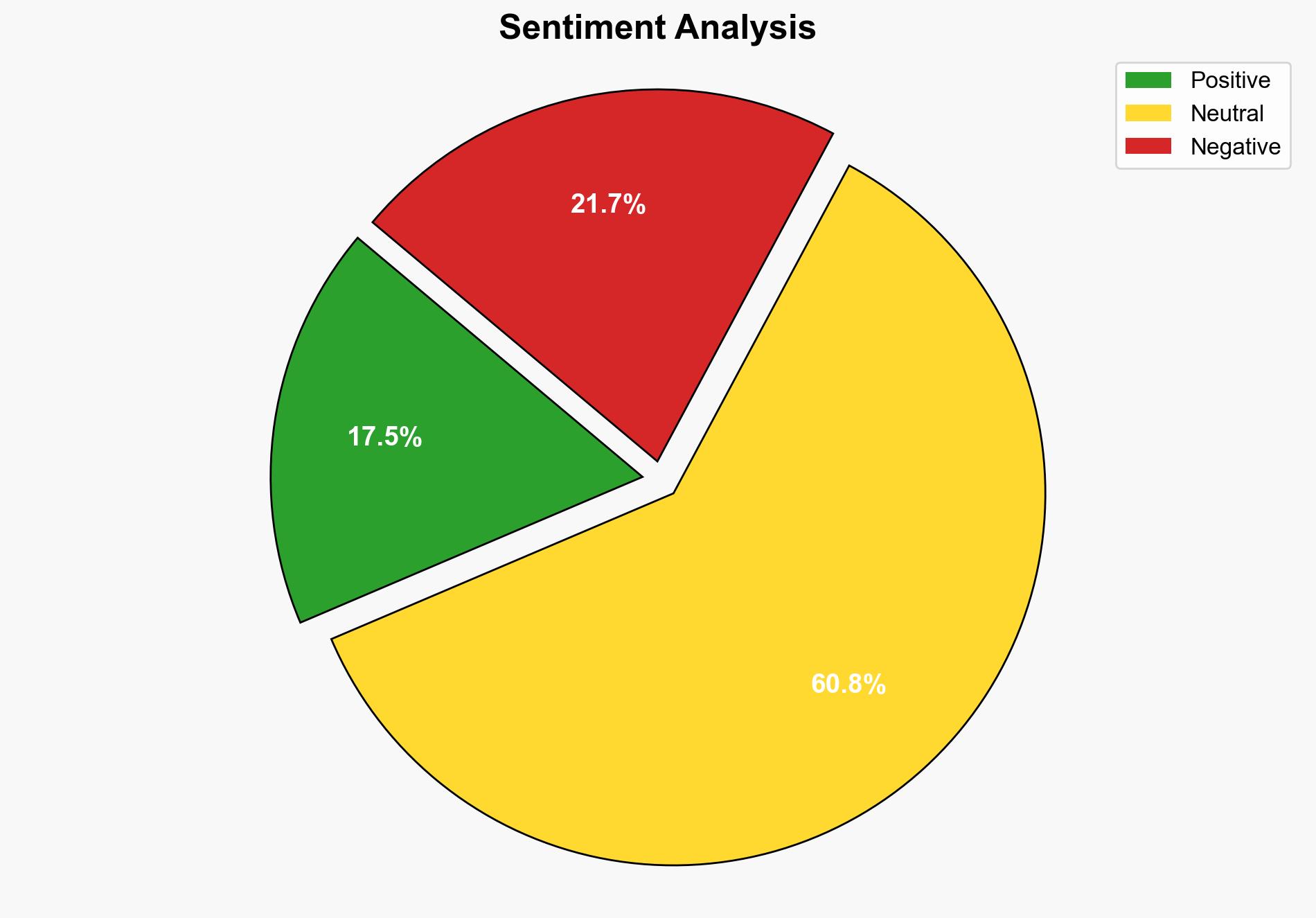
The most supported hypothesis is that the reported hack is a sophisticated phishing campaign rather than a direct breach of Google’s core systems. Confidence level is moderate due to the lack of direct evidence confirming the breach of Google’s database. Recommended action includes enhancing user awareness on phishing tactics and reinforcing multi-factor authentication protocols.
2. Competing Hypotheses
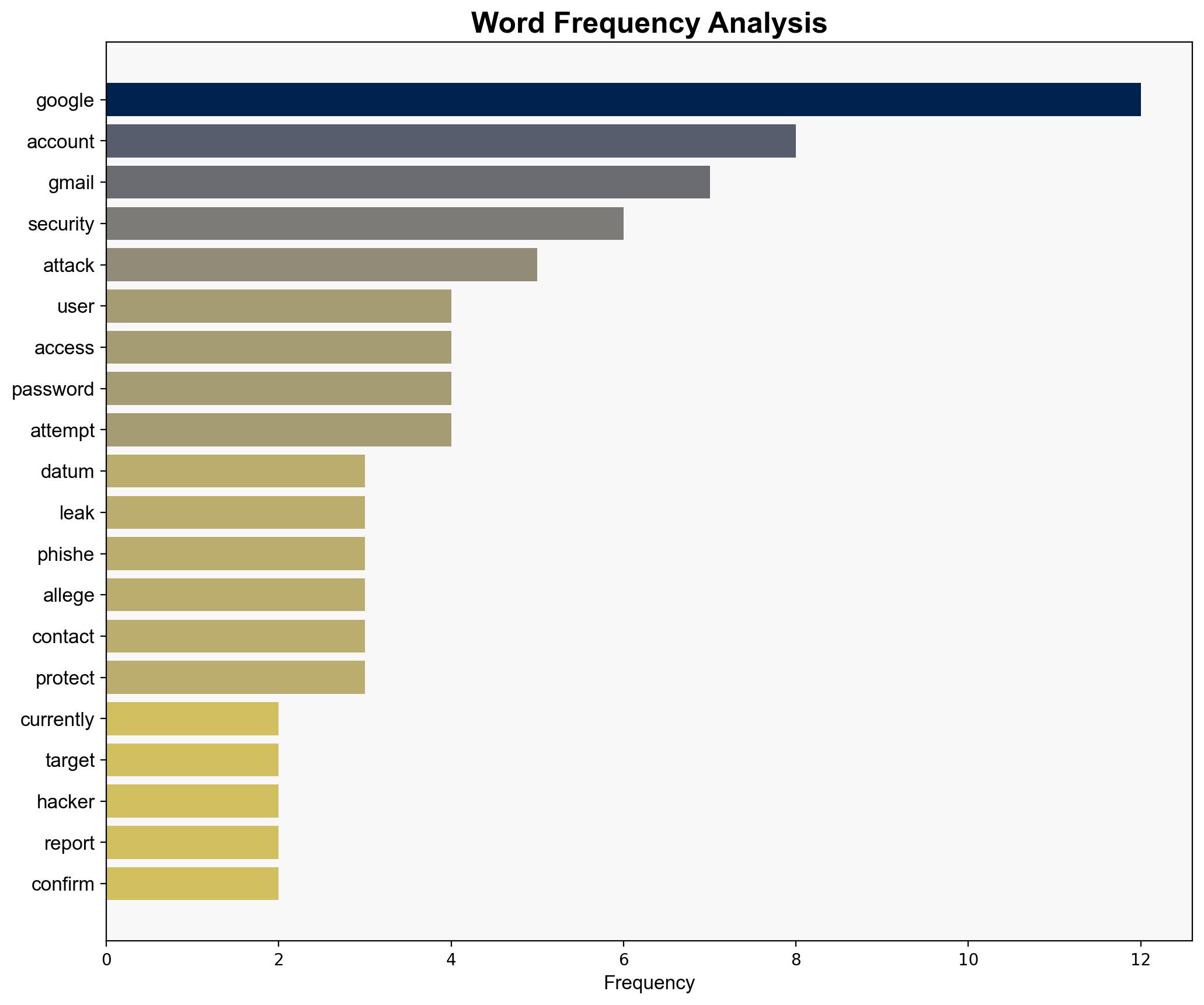
Hypothesis 1: The hack represents a direct breach of Google’s core database systems, compromising sensitive user data on a large scale. This scenario suggests a significant vulnerability in Google’s infrastructure, potentially impacting billions of users globally.
Hypothesis 2: The incident is primarily a phishing campaign exploiting leaked data from a third-party source, such as Salesforce, rather than a direct breach of Google’s systems. This hypothesis posits that attackers are using social engineering tactics to gain access to Gmail accounts.
3. Key Assumptions and Red Flags
Assumptions:
– Hypothesis 1 assumes that Google’s core systems were directly breached, which requires evidence of system vulnerabilities.
– Hypothesis 2 assumes that the data leak originated from a third-party source, not directly from Google.
Red Flags:
– Lack of direct confirmation from Google about a breach of their core systems.
– The report relies heavily on secondary sources like Reddit, which may lack credibility.
– The absence of specific technical details about the breach method raises questions about the accuracy of the reported scale.
4. Implications and Strategic Risks
The implications of a direct breach (Hypothesis 1) include significant reputational damage to Google, potential legal liabilities, and increased scrutiny from regulatory bodies. If Hypothesis 2 is accurate, the primary risk involves user susceptibility to phishing attacks, leading to potential financial losses and identity theft. Both scenarios could escalate into broader cybersecurity concerns, affecting trust in cloud services and digital communications.
5. Recommendations and Outlook
- Enhance public awareness campaigns on phishing tactics and secure account management.
- Encourage users to activate multi-factor authentication and regularly update passwords.
- Google should conduct a thorough internal audit to identify any potential vulnerabilities.
- Scenario Projections:
- Best Case: Incident is contained as a phishing scam with minimal impact.
- Worst Case: A confirmed breach of Google’s systems leads to widespread data compromise.
- Most Likely: The event remains a phishing campaign with increased user awareness mitigating further risks.
6. Key Individuals and Entities
– Google
– ShinyHunter (hacker group)
– Salesforce (potential third-party data source)
7. Thematic Tags
national security threats, cybersecurity, cybercrime, data protection