26 Terror Attack Plans Disrupted by Malaysian Special Branch from 2012 to 2024, Reports Deputy Inspector-Gene…
Published on: 2026-01-28
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: 26 militant terror plots foiled by Special Branch since 2012-2024
1. BLUF (Bottom Line Up Front)
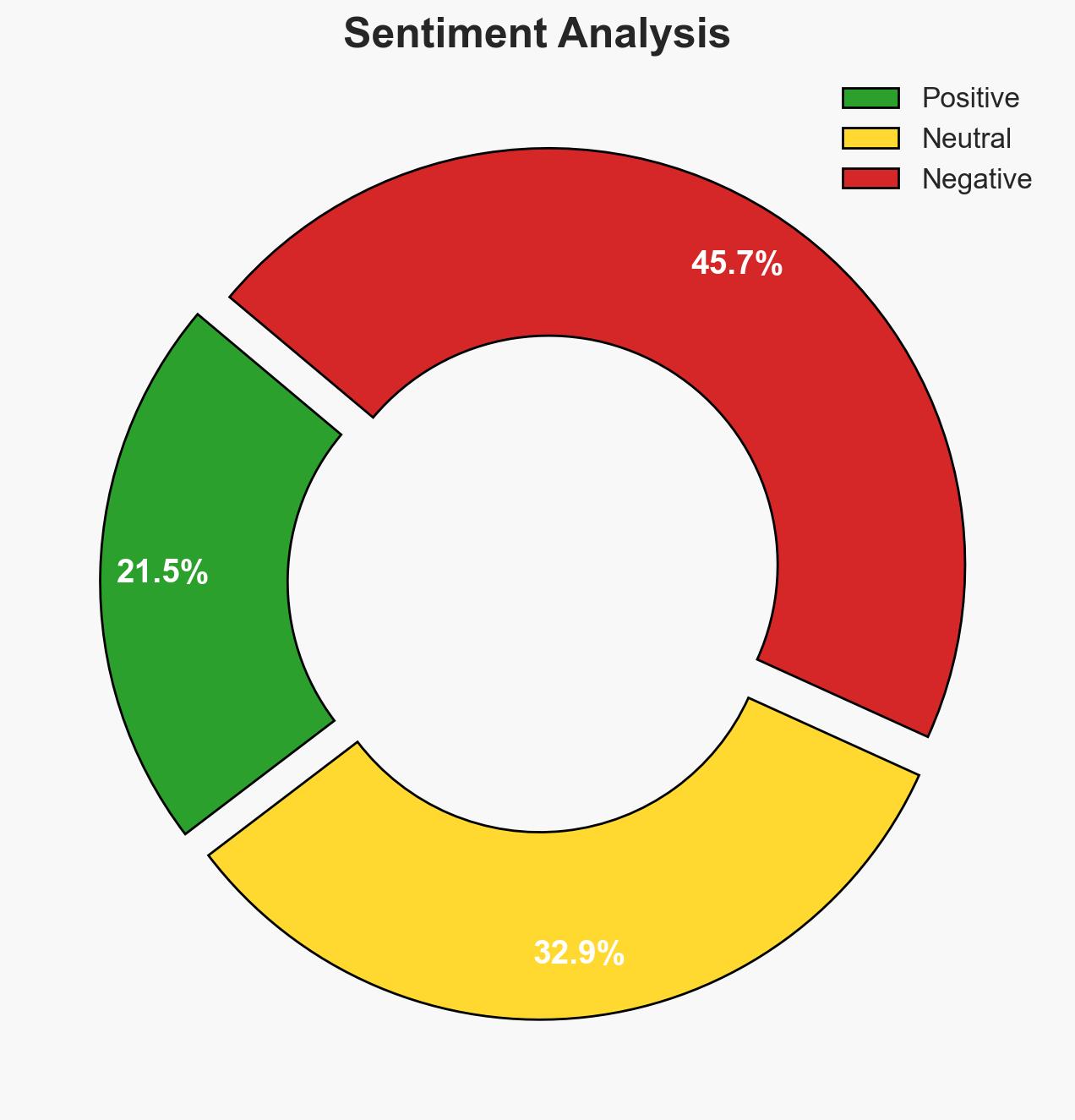
The Bukit Aman Special Branch Counter Terrorism division (E8) successfully thwarted 26 militant and terrorist plots from 2012 to 2024, demonstrating effective adaptation to legislative changes post-ISA repeal. Despite these successes, two attacks were executed, indicating persistent threats. This assessment is made with moderate confidence due to potential information gaps and the evolving nature of terrorist threats.
2. Competing Hypotheses
- Hypothesis A: The E8’s success in thwarting plots is primarily due to effective intelligence-led operations and legal adaptations post-ISA repeal. Supporting evidence includes the number of plots foiled and the legal framework’s adaptation. However, uncertainties remain regarding the full scope of threats and potential undisclosed plots.
- Hypothesis B: The thwarting of plots is partly due to external factors such as decreased operational capabilities of terrorist groups or shifts in their strategic focus. While the number of plots foiled supports E8’s effectiveness, the successful execution of two attacks suggests that external factors may also play a role.
- Assessment: Hypothesis A is currently better supported, given the documented success of E8’s operations and legal adaptations. Key indicators that could shift this judgment include evidence of increased external pressures on terrorist groups or changes in their operational strategies.
3. Key Assumptions and Red Flags
- Assumptions: The E8’s intelligence capabilities are robust; legislative changes have not hindered counter-terrorism efforts; the threat landscape is accurately represented by the reported plots.
- Information Gaps: Details on the nature and scope of the two successful attacks; comprehensive data on unreported or undiscovered plots; insights into terrorist group strategies and capabilities.
- Bias & Deception Risks: Potential over-reliance on official sources may introduce bias; risk of underestimating the adaptive capabilities of terrorist networks.
4. Implications and Strategic Risks
The continued threat of terrorism in Malaysia requires sustained vigilance and adaptive counter-terrorism strategies. The interplay between legislative frameworks and operational effectiveness will be crucial in shaping future security dynamics.
- Political / Geopolitical: Legislative changes could influence regional counter-terrorism cooperation and diplomatic relations.
- Security / Counter-Terrorism: Persistent threats necessitate ongoing adaptation of intelligence and enforcement strategies.
- Cyber / Information Space: Potential for increased cyber operations by terrorist groups targeting critical infrastructure.
- Economic / Social: Successful attacks could destabilize social cohesion and impact economic stability through heightened security measures.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance intelligence-sharing mechanisms; conduct a comprehensive review of recent successful attacks to identify vulnerabilities.
- Medium-Term Posture (1–12 months): Strengthen legal frameworks to ensure flexibility in counter-terrorism operations; invest in technology and training for intelligence personnel.
- Scenario Outlook:
- Best: Continued success in thwarting plots with no successful attacks; requires sustained intelligence and operational enhancements.
- Worst: Increase in successful attacks due to adaptive terrorist strategies; triggered by intelligence failures or legislative constraints.
- Most-Likely: Intermittent successes and failures; ongoing adaptation and intelligence improvements needed to maintain security.
6. Key Individuals and Entities
- Tan Sri Ayob Khan Mydin Pitchay, Deputy Inspector-General of Police, former head of E8
- Bukit Aman Special Branch Counter Terrorism division (E8)
- Tandzim Al-Qaeda Malaysia (TAQM)
7. Thematic Tags
Counter-Terrorism, intelligence operations, legislative adaptation, Salafi-jihadist ideology, national security, Malaysia, terrorist plots
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us