48 of security pros are falling behind compliance requirements – Help Net Security
Published on: 2025-06-02
Intelligence Report: 48% of Security Professionals Are Falling Behind Compliance Requirements
1. BLUF (Bottom Line Up Front)
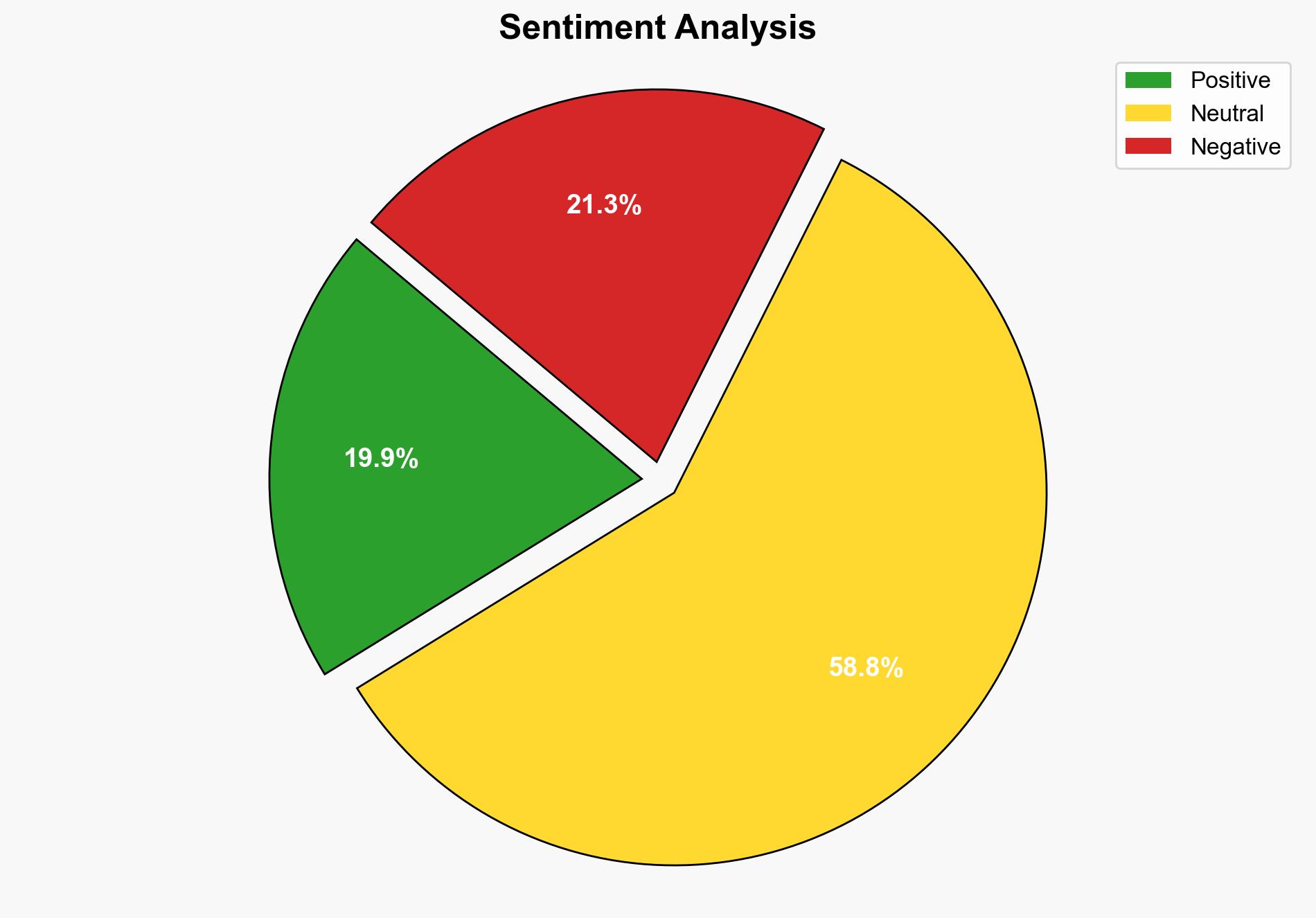
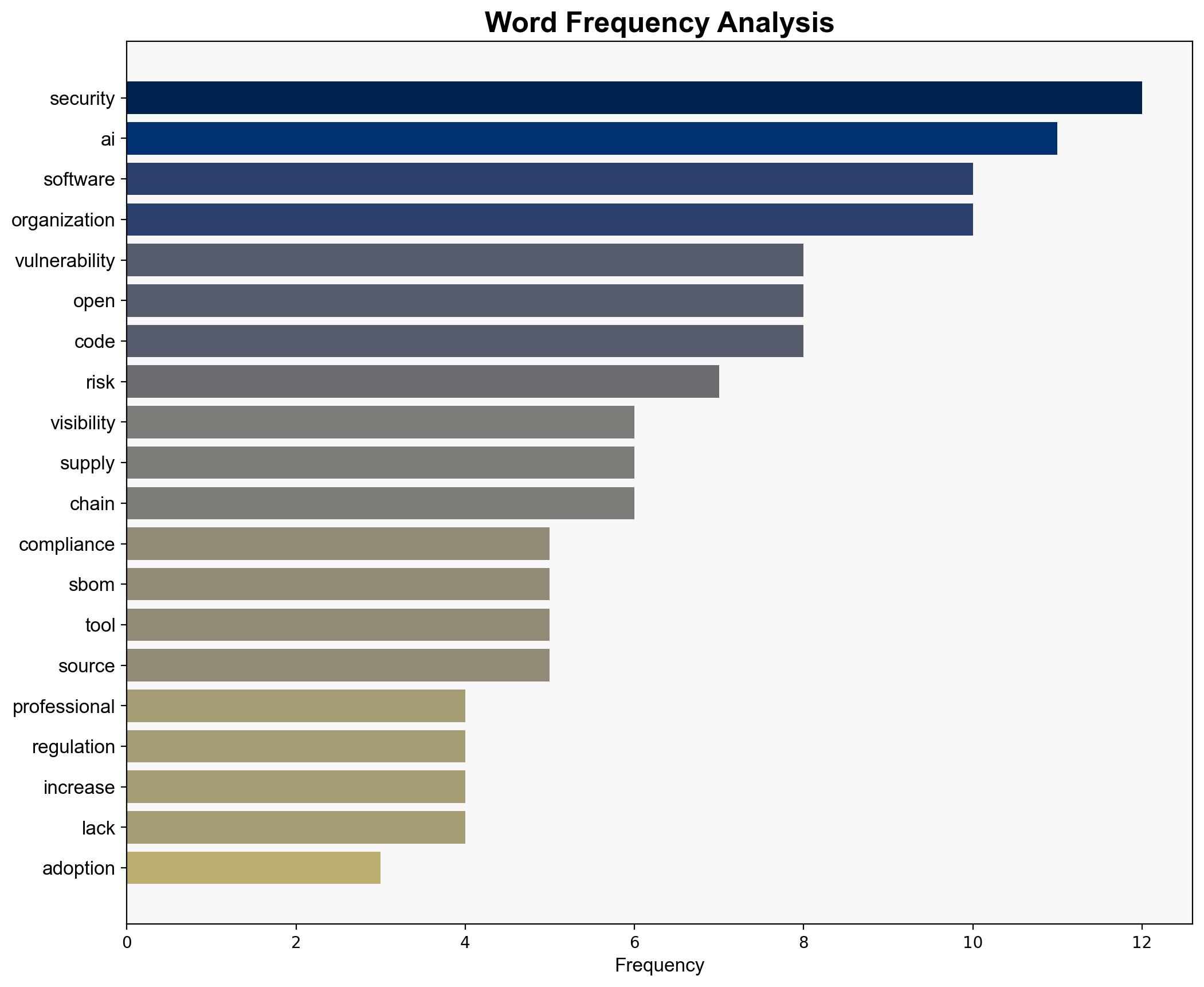
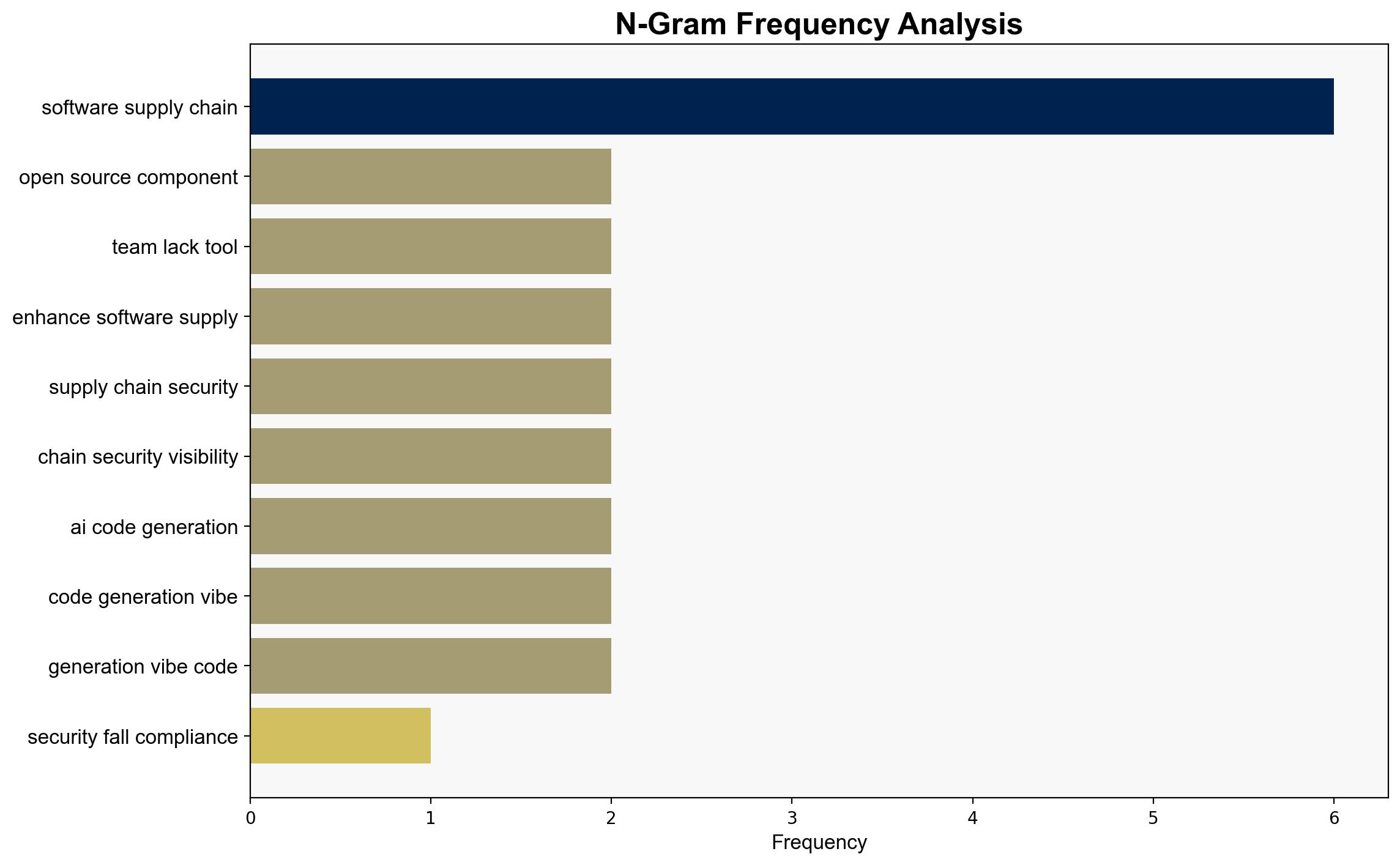
A significant portion of security professionals are struggling to meet compliance requirements due to insufficient tools and processes. This gap in compliance, particularly with Software Bill of Materials (SBOM) regulations, exposes organizations to increased risks of data breaches and legal penalties. Immediate action is necessary to enhance visibility and management of software supply chains, especially with the growing reliance on open-source components.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations indicate that adversaries exploit vulnerabilities in software supply chains, particularly those involving open-source dependencies. The lack of visibility and inadequate tools for tracking these components heighten the risk of successful cyberattacks.
Indicators Development
Key indicators of vulnerability include the inability to accurately identify and track open-source components, as well as the absence of automated risk prioritization tools. Monitoring these indicators can aid in early threat detection.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of cyberattacks exploiting known vulnerabilities in open-source components, with potential pathways leading to significant data breaches and compliance failures.
3. Implications and Strategic Risks
The failure to comply with SBOM regulations poses systemic risks, including substantial financial penalties and reputational damage. The reliance on open-source software without adequate oversight increases the attack surface, potentially leading to cascading effects across sectors reliant on digital infrastructure.
4. Recommendations and Outlook
- Invest in advanced tools for SBOM analysis and vulnerability management to enhance compliance and reduce risk exposure.
- Implement AI-driven solutions for automated risk prioritization and remediation to improve response times and mitigate vulnerabilities.
- Scenario-based projections:
- Best Case: Full compliance achieved with enhanced security posture, reducing breach incidents.
- Worst Case: Continued non-compliance leading to significant breaches and financial penalties.
- Most Likely: Gradual improvement in compliance with ongoing challenges in open-source management.
5. Key Individuals and Entities
Jave Hasan
6. Thematic Tags
national security threats, cybersecurity, compliance, open-source software, AI-driven security