5 myths about Windows 10 End of Life you need to know of – TechRadar
Published on: 2025-10-09
Intelligence Report: 5 myths about Windows 10 End of Life you need to know of – TechRadar
1. BLUF (Bottom Line Up Front)
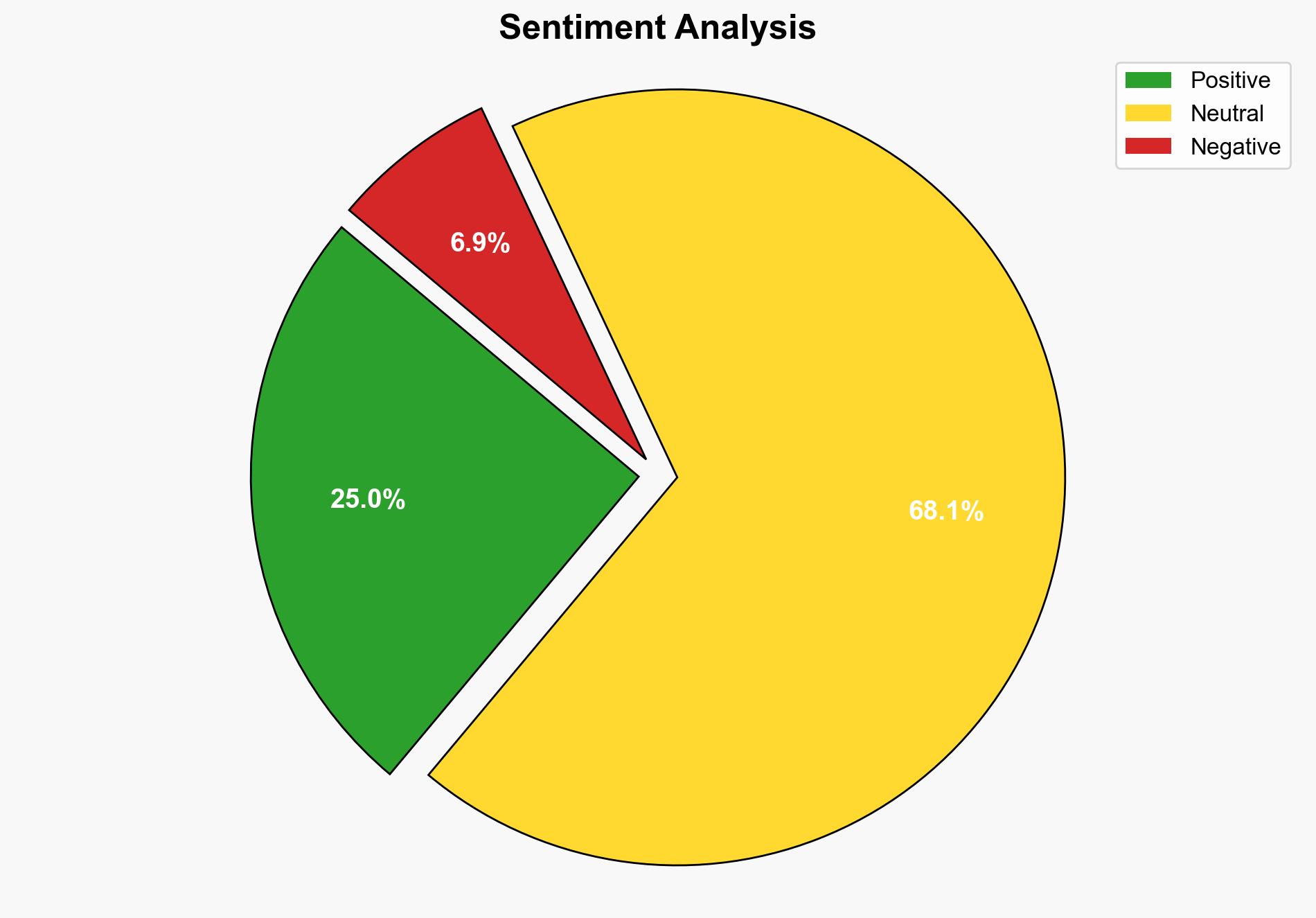
The most supported hypothesis is that while Windows 10 will continue to function post-support, the lack of security updates will significantly increase cybersecurity risks. Confidence level: High. Recommended action: Users should transition to supported operating systems or ensure robust cybersecurity measures are in place.
2. Competing Hypotheses
– **Hypothesis 1**: Windows 10 will remain functional and secure post-support with careful online behavior and antivirus protection.
– **Hypothesis 2**: Windows 10 will be increasingly vulnerable to security threats post-support, making it unsafe without updates.
Using ACH 2.0, Hypothesis 2 is better supported due to the historical precedence of vulnerabilities in unsupported systems and the increasing sophistication of cyber threats.
3. Key Assumptions and Red Flags
– **Assumptions**:
– Hypothesis 1 assumes that antivirus software and cautious online behavior can fully mitigate risks.
– Hypothesis 2 assumes that new vulnerabilities will be exploited without timely patches.
– **Red Flags**:
– Over-reliance on antivirus solutions without updates.
– Underestimation of the speed and scale of emerging cyber threats.
– **Blind Spots**:
– Potential for Microsoft to extend support or offer alternative security measures.
4. Implications and Strategic Risks
– **Cybersecurity Risks**: Increased exposure to malware and ransomware attacks.
– **Economic Risks**: Potential costs associated with data breaches and system downtime.
– **Geopolitical Risks**: Exploitation by state-sponsored actors targeting unsupported systems.
– **Psychological Risks**: User complacency due to misinformation about system security.
5. Recommendations and Outlook
- Transition to a supported operating system before the end-of-life date.
- Implement comprehensive cybersecurity measures, including regular data backups and network monitoring.
- Scenario Projections:
– **Best Case**: Users transition smoothly with minimal disruption.
– **Worst Case**: Widespread exploitation of vulnerabilities leading to significant data breaches.
– **Most Likely**: Gradual increase in security incidents as unsupported systems persist.
6. Key Individuals and Entities
– Microsoft Corporation
– Users of Windows 10
7. Thematic Tags
cybersecurity, software lifecycle, risk management, technology transition