5 warning signs that your phone’s been hacked – and how to fight back – ZDNet
Published on: 2025-04-12
Intelligence Report: 5 Warning Signs That Your Phone’s Been Hacked – and How to Fight Back – ZDNet
1. BLUF (Bottom Line Up Front)
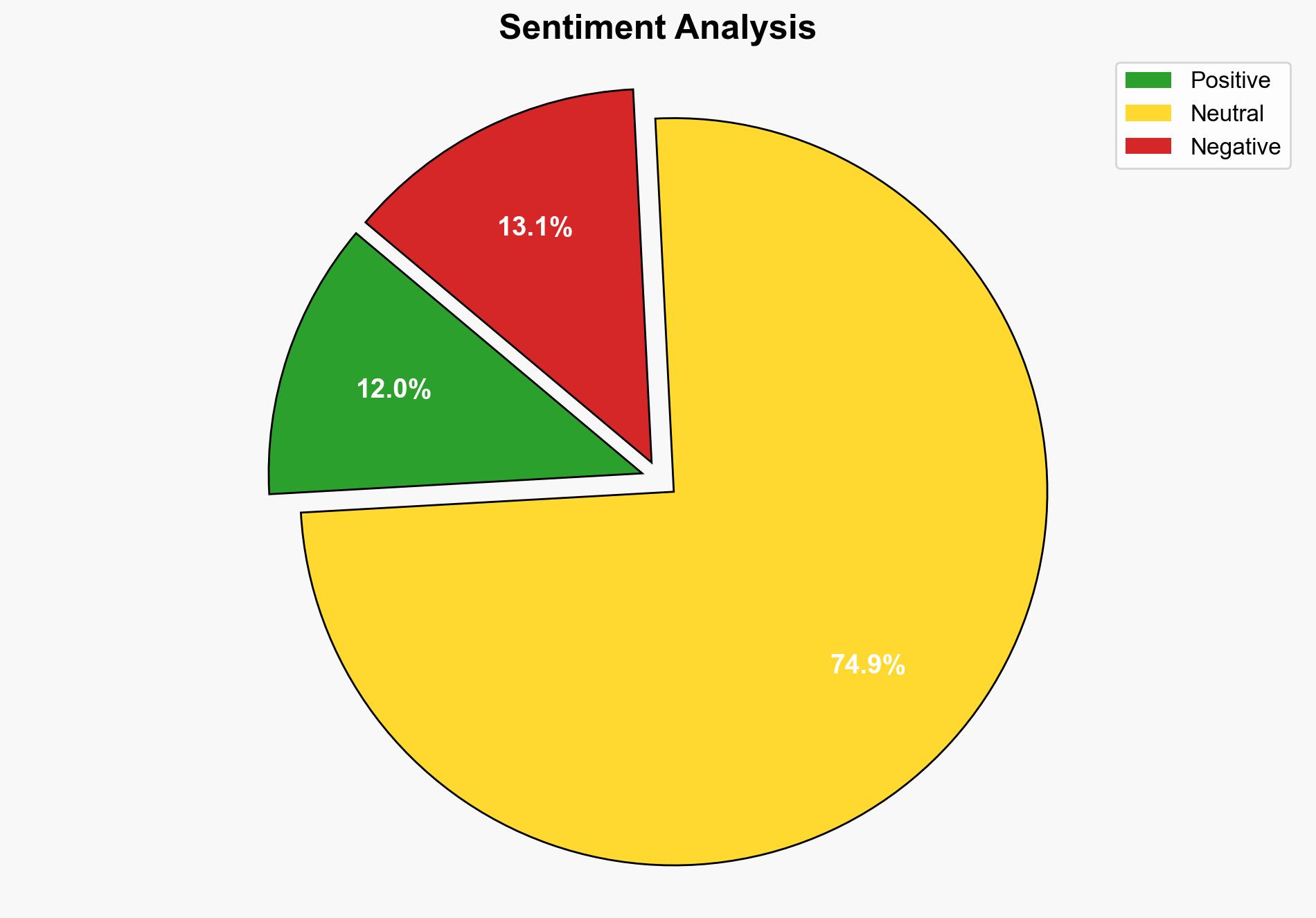
This report identifies five critical indicators that a mobile phone may have been compromised by hackers. These signs include rapid battery drain, sluggish performance, unfamiliar logins, reduced storage space, and the presence of unauthorized apps. Effective countermeasures include using USSD codes to detect call redirections and removing suspicious apps. Stakeholders should prioritize enhancing mobile security protocols to safeguard personal and confidential information.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
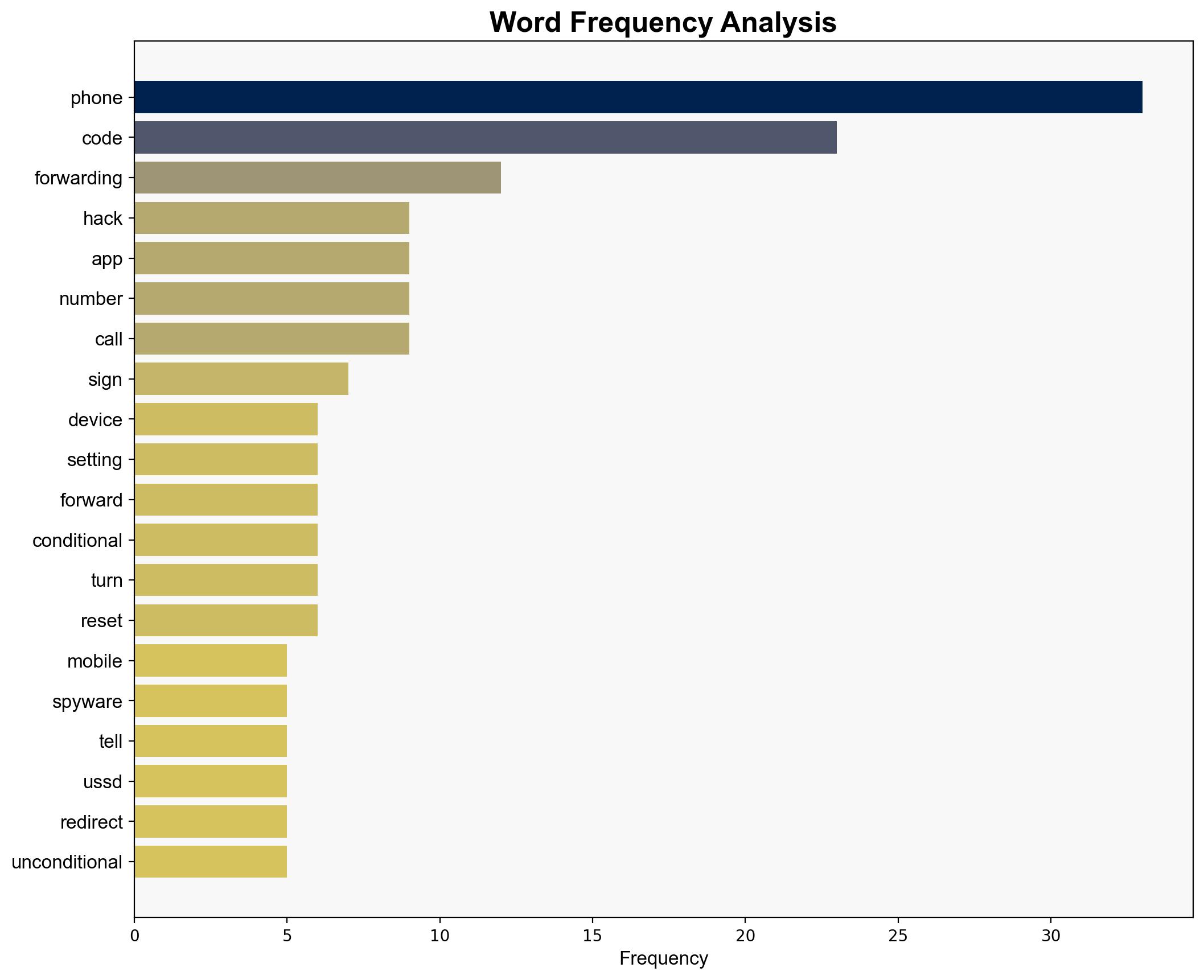
The report outlines the vulnerability of mobile phones to hacking through various methods such as spyware, phishing, and malicious apps. The analysis highlights the potential for significant data breaches and unauthorized access to personal information. The presence of spyware can lead to faster battery depletion and reduced device performance. Unfamiliar logins and unauthorized apps suggest possible unauthorized access to accounts and data. The use of USSD codes is recommended as a diagnostic tool to identify potential call redirections.
3. Implications and Strategic Risks
The increasing prevalence of mobile phone hacking poses substantial risks to personal privacy, national security, and economic interests. Unauthorized access to sensitive information can lead to identity theft, financial fraud, and compromised communications. The trend of mobile device exploitation could undermine public trust in digital security and impact regional stability if leveraged for espionage or cyber warfare.
4. Recommendations and Outlook
Recommendations:
- Enhance mobile security measures by implementing robust authentication methods and regular security updates.
- Encourage public awareness campaigns on recognizing and responding to signs of phone hacking.
- Advocate for regulatory frameworks that mandate stringent security standards for mobile applications and services.
Outlook:
In a best-case scenario, increased awareness and improved security measures will reduce the incidence of mobile phone hacking. In a worst-case scenario, sophisticated hacking techniques could outpace security advancements, leading to widespread data breaches. The most likely outcome involves a continued arms race between hackers and security professionals, necessitating ongoing vigilance and adaptation.
5. Key Individuals and Entities
The report references Amy Clark, who has compiled a guide on phone hacking threats and countermeasures. The analysis is based on insights from a consumer reviews site, Techreport, which provides guidance on identifying and mitigating phone hacking risks.