Insurance Sector Should Be on the Lookout for Scattered Spider Hackers – Insurance Journal
Published on: 2025-06-23
Intelligence Report: Insurance Sector Should Be on the Lookout for Scattered Spider Hackers – Insurance Journal
1. BLUF (Bottom Line Up Front)
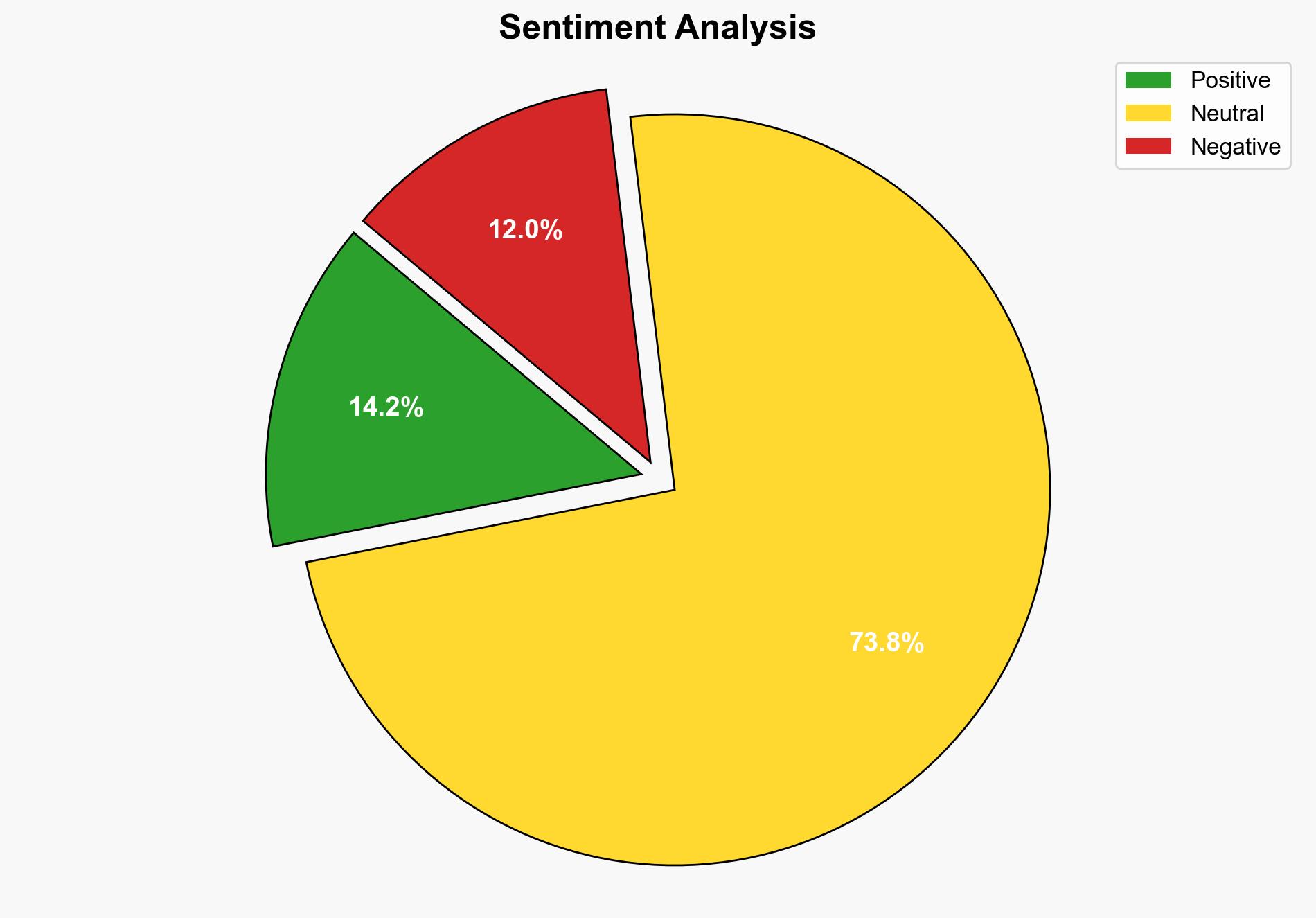
The cybercrime group known as Scattered Spider has shifted its focus from retail to the insurance sector, posing significant risks to insurers due to their valuable data holdings. Recent incidents involving Erie Insurance and Philadelphia Insurance Companies suggest a trend that requires immediate attention. The group employs sophisticated social engineering and phishing tactics to infiltrate systems. It is crucial for insurance companies to enhance their cybersecurity measures and employee training to mitigate these threats.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations indicate that Scattered Spider may exploit vulnerabilities in insurance companies’ data management systems, targeting personal and financial information.
Indicators Development
Key indicators include increased phishing attempts and unusual access patterns in insurer networks, suggesting potential breaches.
Bayesian Scenario Modeling
Probabilistic models predict a high likelihood of continued attacks on insurers, with potential pathways involving ransomware deployment.
Network Influence Mapping
Mapping reveals Scattered Spider’s collaboration with ransomware service groups, increasing their operational impact.
3. Implications and Strategic Risks
The shift in focus by Scattered Spider to the insurance sector could lead to significant financial losses and reputational damage. The systemic vulnerabilities in data protection and employee awareness are critical risks. Cross-domain impacts include potential regulatory scrutiny and increased insurance premiums.
4. Recommendations and Outlook
- Enhance cybersecurity protocols, focusing on data encryption and access controls.
- Implement regular employee training programs to recognize and respond to phishing and social engineering attempts.
- Develop incident response plans with scenario-based projections to prepare for potential breaches.
- Foster partnerships with cybersecurity firms to leverage advanced threat detection technologies.
5. Key Individuals and Entities
John Hultquist, Keith Wojcieszek
6. Thematic Tags
national security threats, cybersecurity, insurance sector, cybercrime, data protection