Prometei botnet activity has surged since March 2025 – Securityaffairs.com
Published on: 2025-06-25
Intelligence Report: Prometei Botnet Activity Surge Since March 2025
1. BLUF (Bottom Line Up Front)
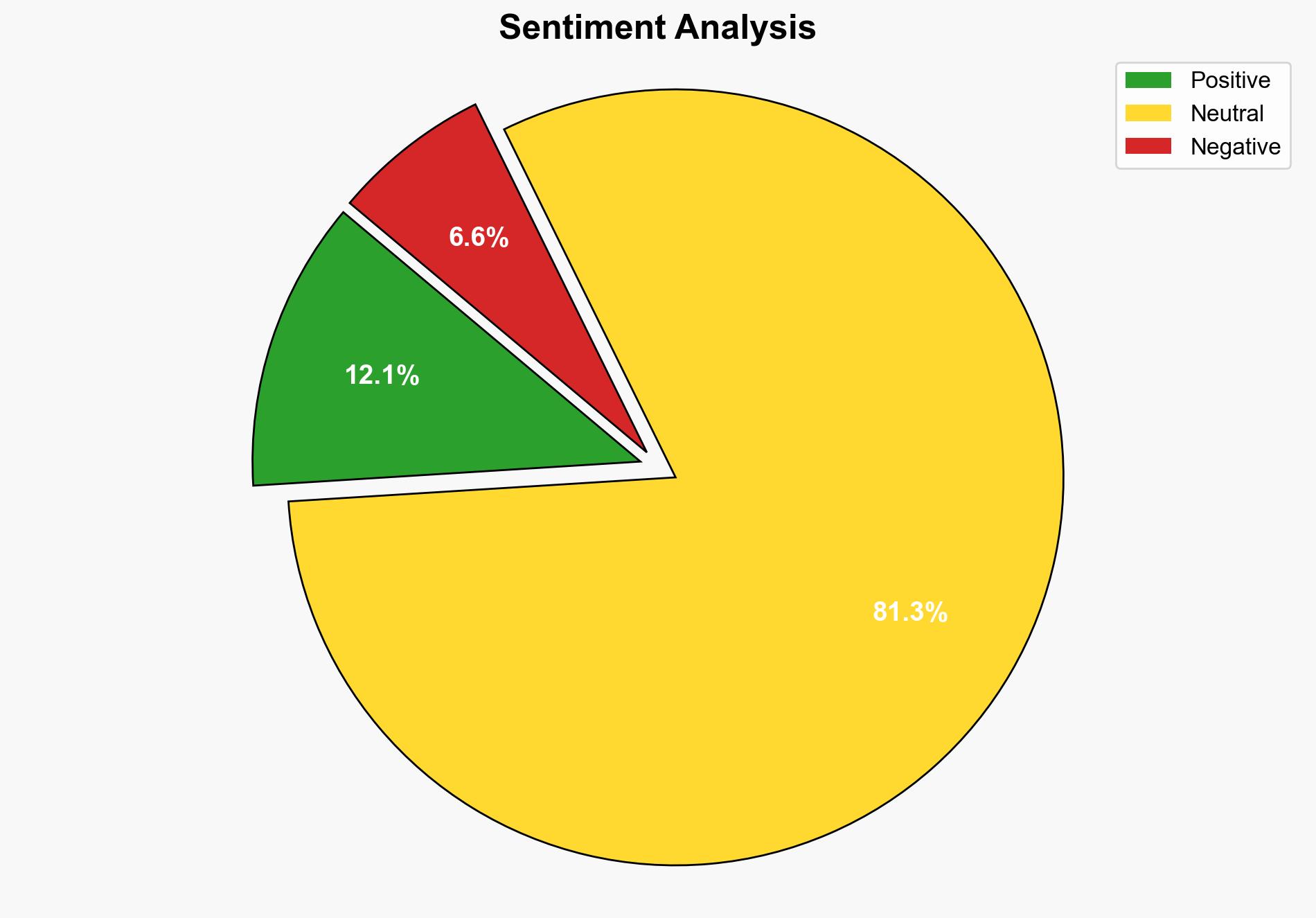
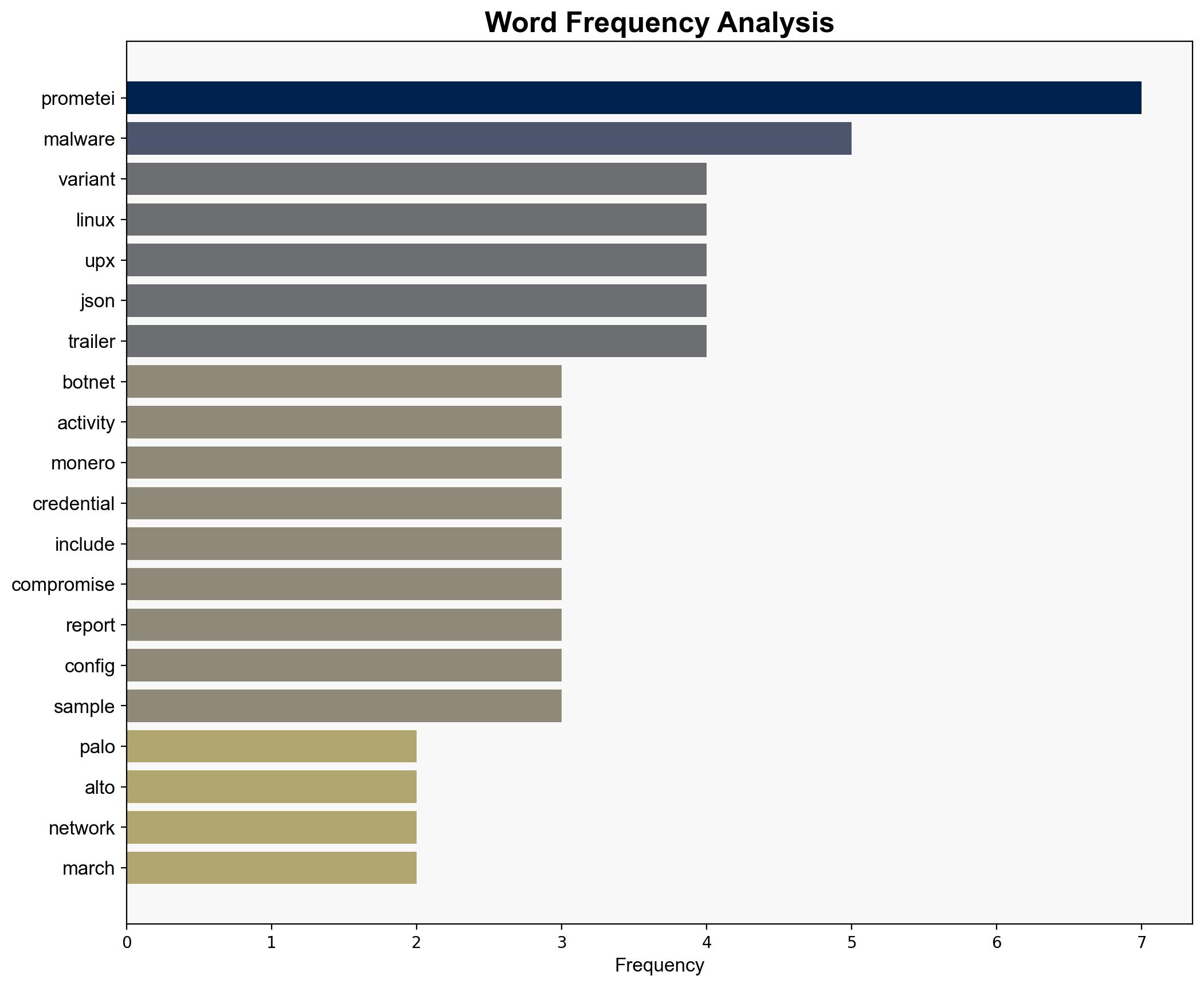
The Prometei botnet has experienced a significant surge in activity since March 2025, primarily targeting Linux systems for Monero mining and credential theft. This resurgence involves a new variant with enhanced evasion techniques and modular architecture, posing increased risks to cybersecurity. Immediate attention is required to update detection mechanisms and strengthen system defenses.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations indicate that the Prometei botnet’s modular design allows it to adapt quickly, exploiting vulnerabilities like the EternalBlue SMB flaw to spread and deploy multiple payloads.
Indicators Development
Key indicators include the use of domain generation algorithms, UPX-packed Linux ELF files disguised as PHP scripts, and dynamic configuration settings to evade detection.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of continued botnet evolution, with potential for increased targeting of high-value systems for financial gain.
Network Influence Mapping
Analysis of network traffic patterns reveals significant influence from servers based in Indonesia, suggesting a strategic distribution point for the botnet’s activities.
3. Implications and Strategic Risks
The resurgence of the Prometei botnet highlights systemic vulnerabilities in Linux systems, with potential cascading effects on financial sectors reliant on these systems. The botnet’s financial motivation and evolving capabilities pose a cross-domain risk, potentially impacting economic stability and national security.
4. Recommendations and Outlook
- Enhance monitoring and detection systems using updated YARA rules and indicators of compromise (IOCs) to identify Prometei-related activities.
- Implement robust patch management practices to mitigate vulnerabilities like EternalBlue.
- Scenario-based projections suggest a best-case scenario of containment through coordinated international cybersecurity efforts, a worst-case scenario of widespread financial disruption, and a most likely scenario of ongoing targeted attacks.
5. Key Individuals and Entities
The report does not identify specific individuals by name; however, it emphasizes the role of entities involved in cybersecurity research and defense, such as Palo Alto Networks.
6. Thematic Tags
national security threats, cybersecurity, financial crime, Linux vulnerabilities