Ex-student hacked uni for free parking before threatening data drop police say – ABC News (AU)
Published on: 2025-06-26
Intelligence Report: Ex-student hacked uni for free parking before threatening data drop police say – ABC News (AU)
1. BLUF (Bottom Line Up Front)
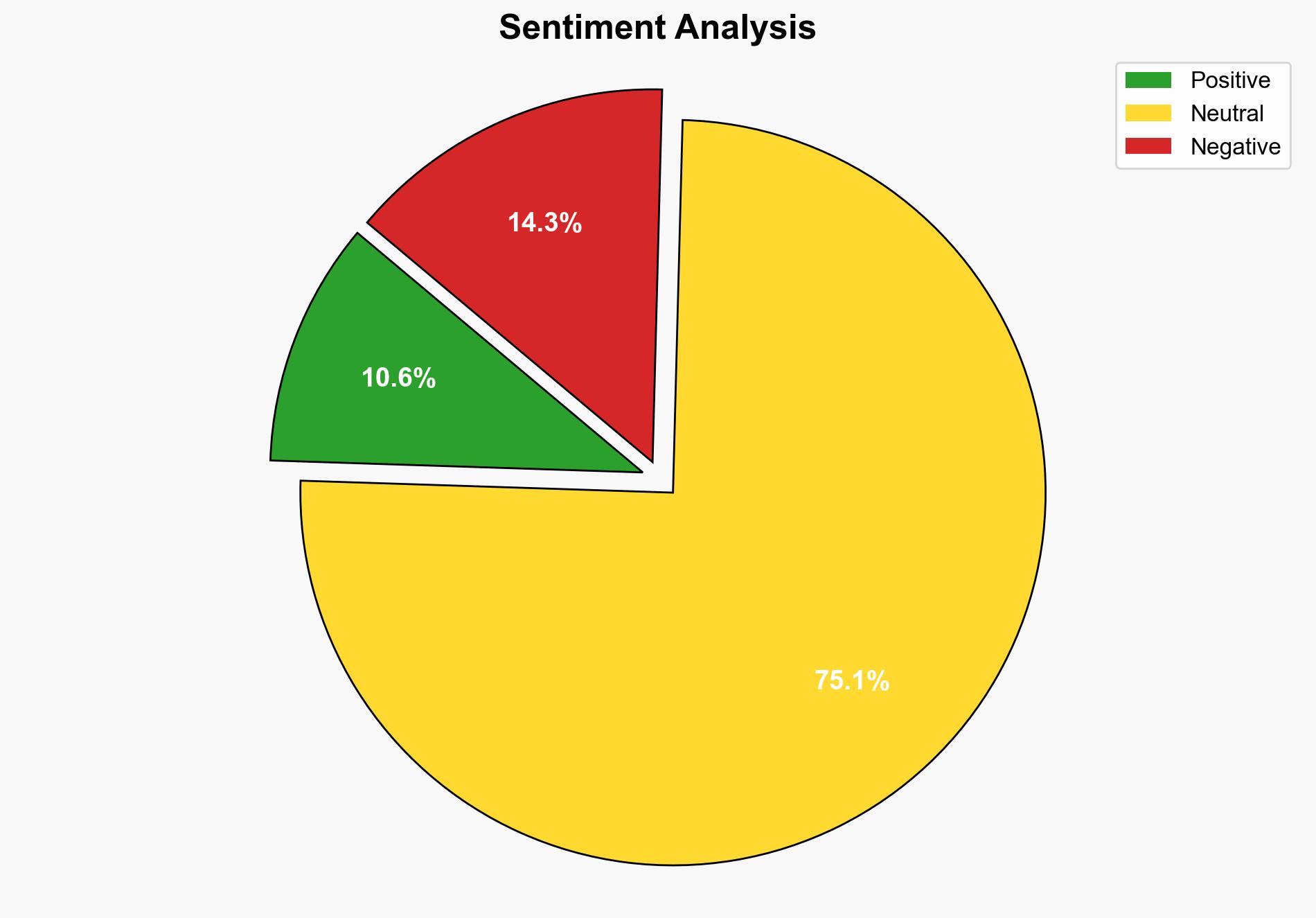
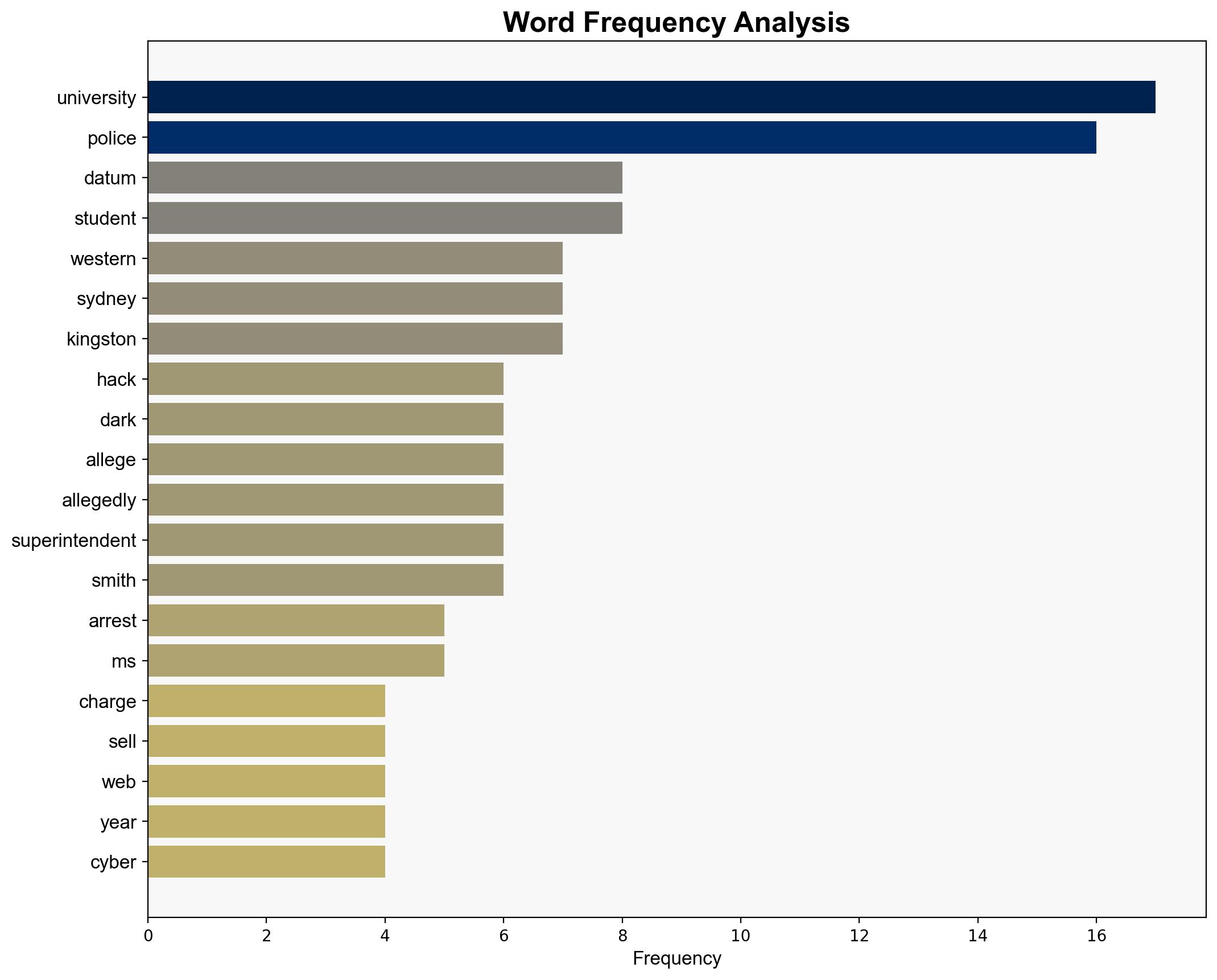
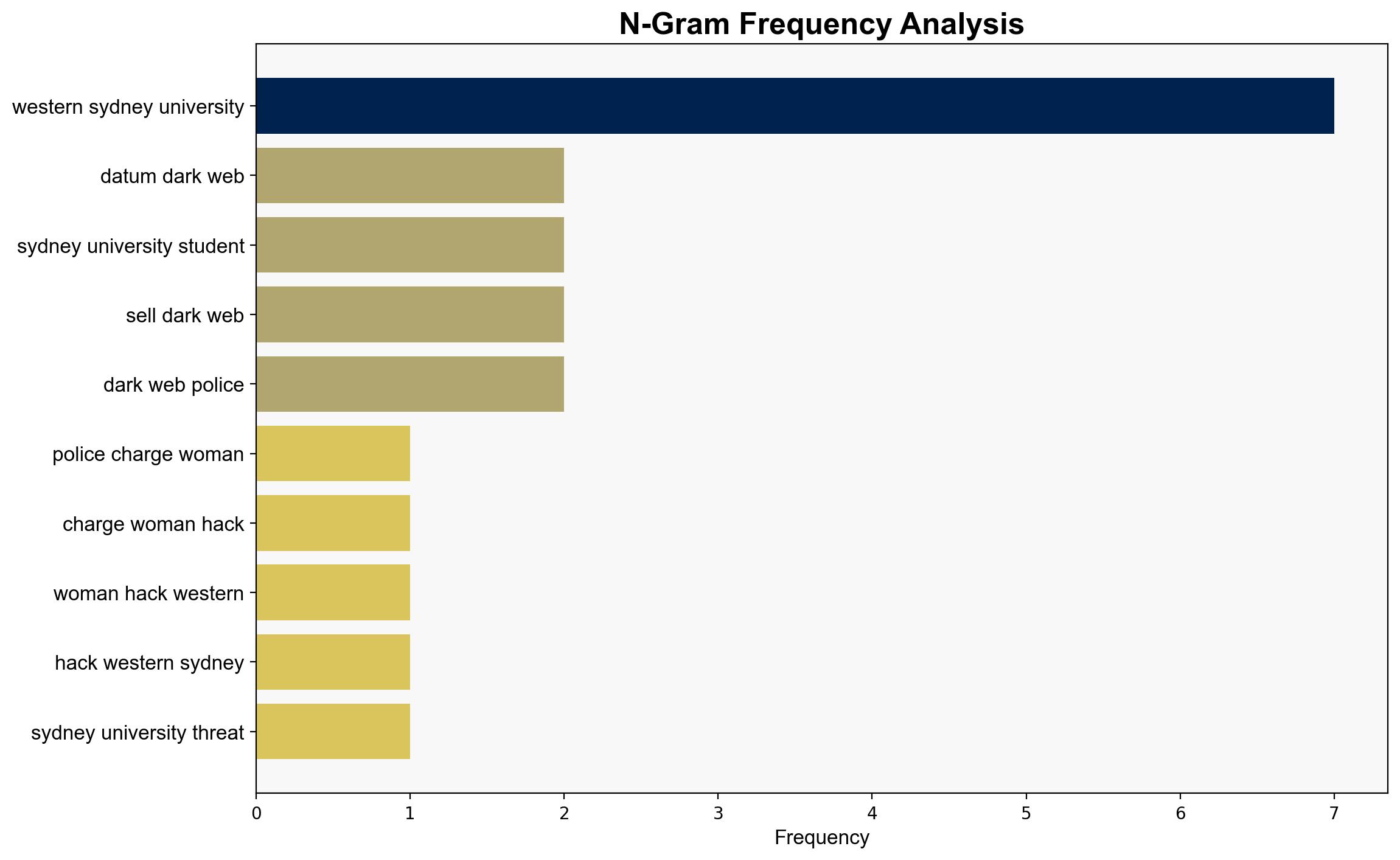
An ex-student, Birdie Kingston, allegedly hacked Western Sydney University’s systems to secure free parking and later threatened to sell sensitive data on the dark web. The incident underscores significant cybersecurity vulnerabilities within educational institutions. Immediate actions are recommended to enhance cyber defenses and prevent future breaches.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulated actions of the cyber adversary, Birdie Kingston, revealed potential vulnerabilities in university IT infrastructure, emphasizing the need for robust access controls and monitoring systems.
Indicators Development
Identified anomalies in system access patterns and data modification activities as key indicators of potential insider threats within educational institutions.
Bayesian Scenario Modeling
Utilized probabilistic inference to predict potential pathways for similar cyberattacks, highlighting the likelihood of insider threats exploiting system weaknesses for personal gain.
3. Implications and Strategic Risks
The breach highlights systemic vulnerabilities in university cybersecurity protocols, posing risks of data theft and financial loss. The incident could inspire similar attacks across educational institutions, potentially leading to widespread data breaches and reputational damage.
4. Recommendations and Outlook
- Implement comprehensive cybersecurity training for staff and students to recognize and report suspicious activities.
- Enhance access controls and regularly audit IT systems to detect and mitigate unauthorized access attempts.
- Develop incident response plans tailored to educational institutions to swiftly address and contain breaches.
- Scenario-based projections:
- Best case: Strengthened cybersecurity measures prevent future breaches.
- Worst case: Continued vulnerabilities lead to further data compromises.
- Most likely: Incremental improvements reduce but do not eliminate risks.
5. Key Individuals and Entities
Birdie Kingston
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus