Protecting Business Data From Unauthorized Encryption Threats – HackRead
Published on: 2025-06-26
Intelligence Report: Protecting Business Data From Unauthorized Encryption Threats – HackRead
1. BLUF (Bottom Line Up Front)
Unauthorized encryption of business data, primarily through ransomware, poses a significant financial threat, with average costs reaching millions per incident. Traditional security measures are insufficient against sophisticated threats. Implementing a Zero Trust Architecture and AI-driven solutions is crucial for enhancing security posture and mitigating financial impacts.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulating cyber adversary actions reveals vulnerabilities in existing security frameworks, emphasizing the need for proactive resilience strategies.
Indicators Development
Monitoring behavioral and technical anomalies is essential for early detection of unauthorized encryption activities.
Bayesian Scenario Modeling
Probabilistic modeling predicts potential cyberattack pathways, aiding in the anticipation and prevention of breaches.
Network Influence Mapping
Mapping influence relationships helps assess the impact of various actors on cybersecurity threats.
3. Implications and Strategic Risks
The evolving nature of cybersecurity threats, particularly in healthcare and finance, poses systemic vulnerabilities with potential cascading effects on economic stability. The increasing sophistication of attacks necessitates a comprehensive approach to risk management.
4. Recommendations and Outlook
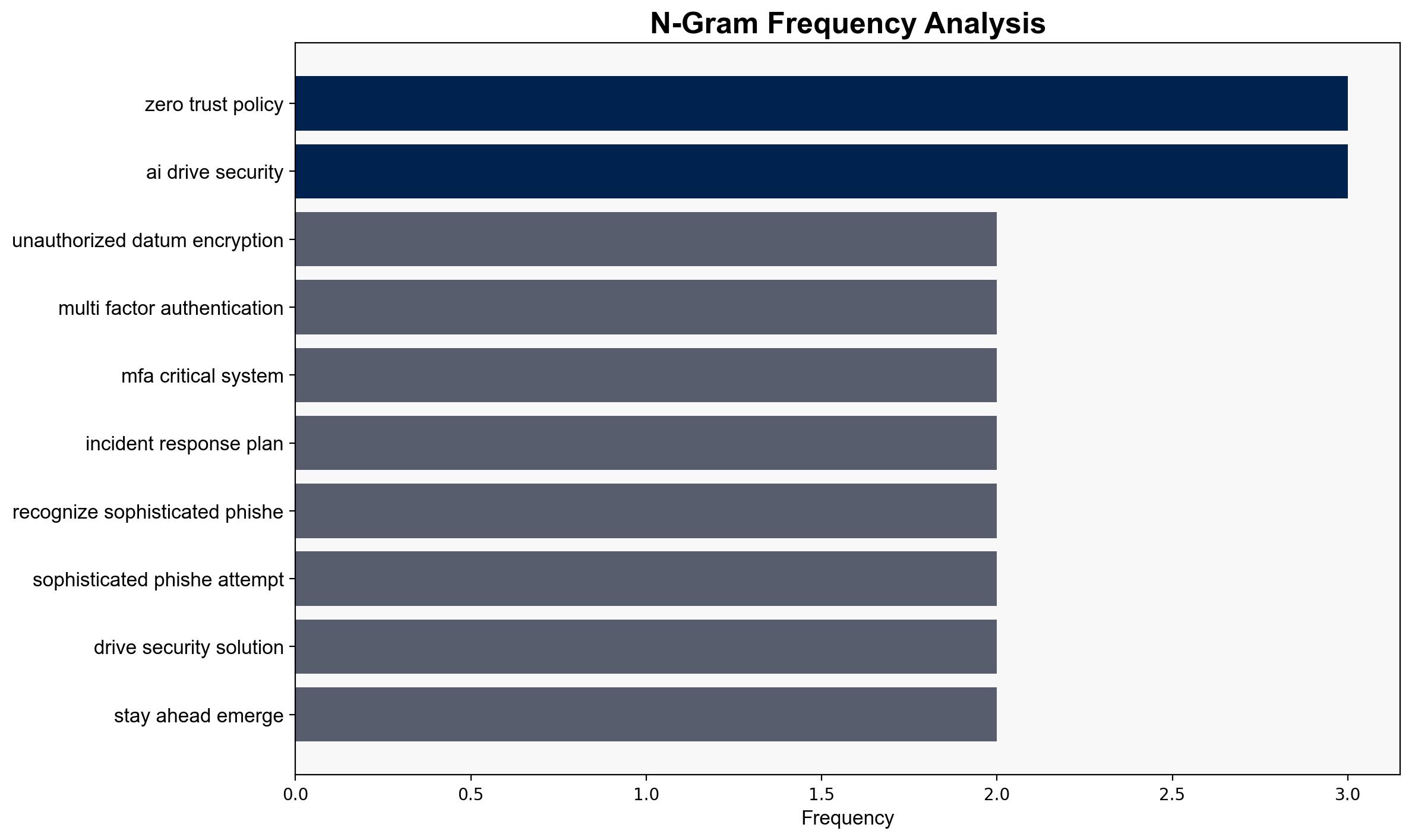
- Adopt a Zero Trust policy with multi-factor authentication and continuous identity monitoring to build a robust defense against breaches.
- Implement network micro-segmentation and real-time traffic analysis to limit lateral movement and detect anomalies.
- Develop an effective incident response plan to ensure business continuity post-attack.
- Scenario-based projections suggest that adopting these measures could significantly reduce breach costs and enhance resilience.
5. Key Individuals and Entities
UnitedHealth Group is highlighted as a recent victim of a ransomware attack, underscoring the vulnerabilities even among large organizations.
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus