CitrixBleed 2 The nightmare that echoes the CitrixBleed flaw in Citrix NetScaler devices – Securityaffairs.com
Published on: 2025-06-26
Intelligence Report: CitrixBleed 2 – The Nightmare Echoing the CitrixBleed Flaw in Citrix NetScaler Devices
1. BLUF (Bottom Line Up Front)
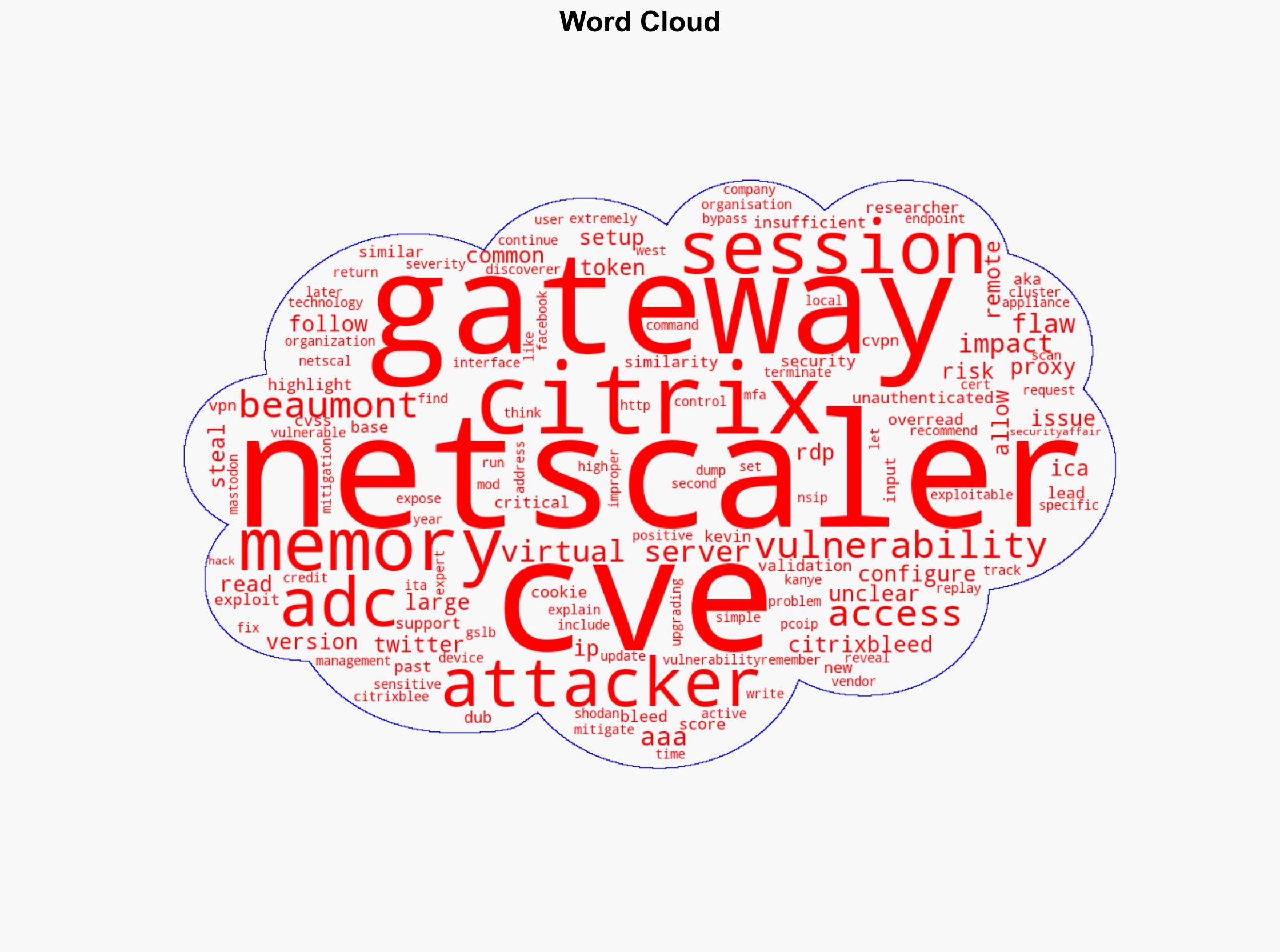
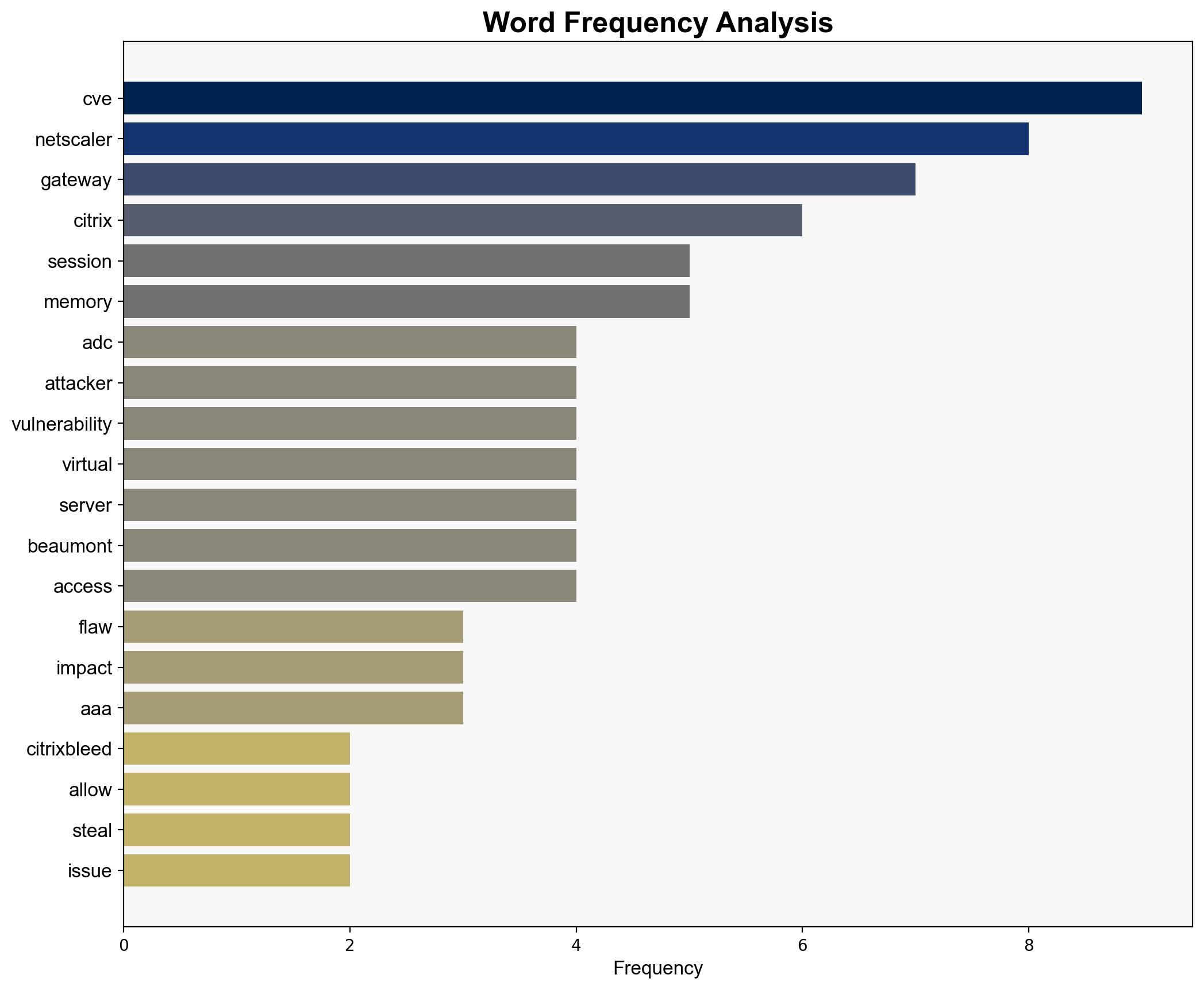
A new vulnerability, dubbed CitrixBleed (CVE), has been identified in Citrix NetScaler ADC and Gateway devices. This flaw allows unauthenticated attackers to steal session cookies through memory overread, posing significant risks to organizations using these devices for remote access. Immediate mitigation strategies are essential to prevent potential exploitation.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
The vulnerability allows adversaries to execute memory overread attacks, potentially leading to unauthorized access to sensitive session tokens. This simulation underscores the need for robust input validation and access controls.
Indicators Development
Monitoring for unusual access patterns and session anomalies is crucial. Indicators such as unexpected session terminations or unauthorized access attempts should be prioritized.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of exploitation if the vulnerability remains unpatched, especially in environments with extensive remote access setups.
3. Implications and Strategic Risks
The vulnerability poses a systemic risk to organizations relying on Citrix for remote access, potentially leading to data breaches and unauthorized access. The cascading effects could impact operational continuity and data integrity, with broader implications for national cybersecurity.
4. Recommendations and Outlook
- Immediate patching of affected Citrix NetScaler devices is critical. Organizations should follow vendor guidelines to update systems and terminate active sessions.
- Implement enhanced monitoring for session anomalies and unauthorized access attempts.
- Scenario-based projections:
- Best Case: Rapid patch deployment mitigates risk with minimal disruption.
- Worst Case: Delayed response leads to widespread exploitation and data breaches.
- Most Likely: Partial mitigation as organizations gradually implement patches.
5. Key Individuals and Entities
Kevin Beaumont, a security researcher, highlighted the similarity to previous vulnerabilities and emphasized the critical nature of the flaw.
6. Thematic Tags
national security threats, cybersecurity, vulnerability management, remote access security