CitrixBleed 2 Vulnerability Exploited Recalling Earlier CitrixBleed Fallout – Infosecurity Magazine
Published on: 2025-06-27
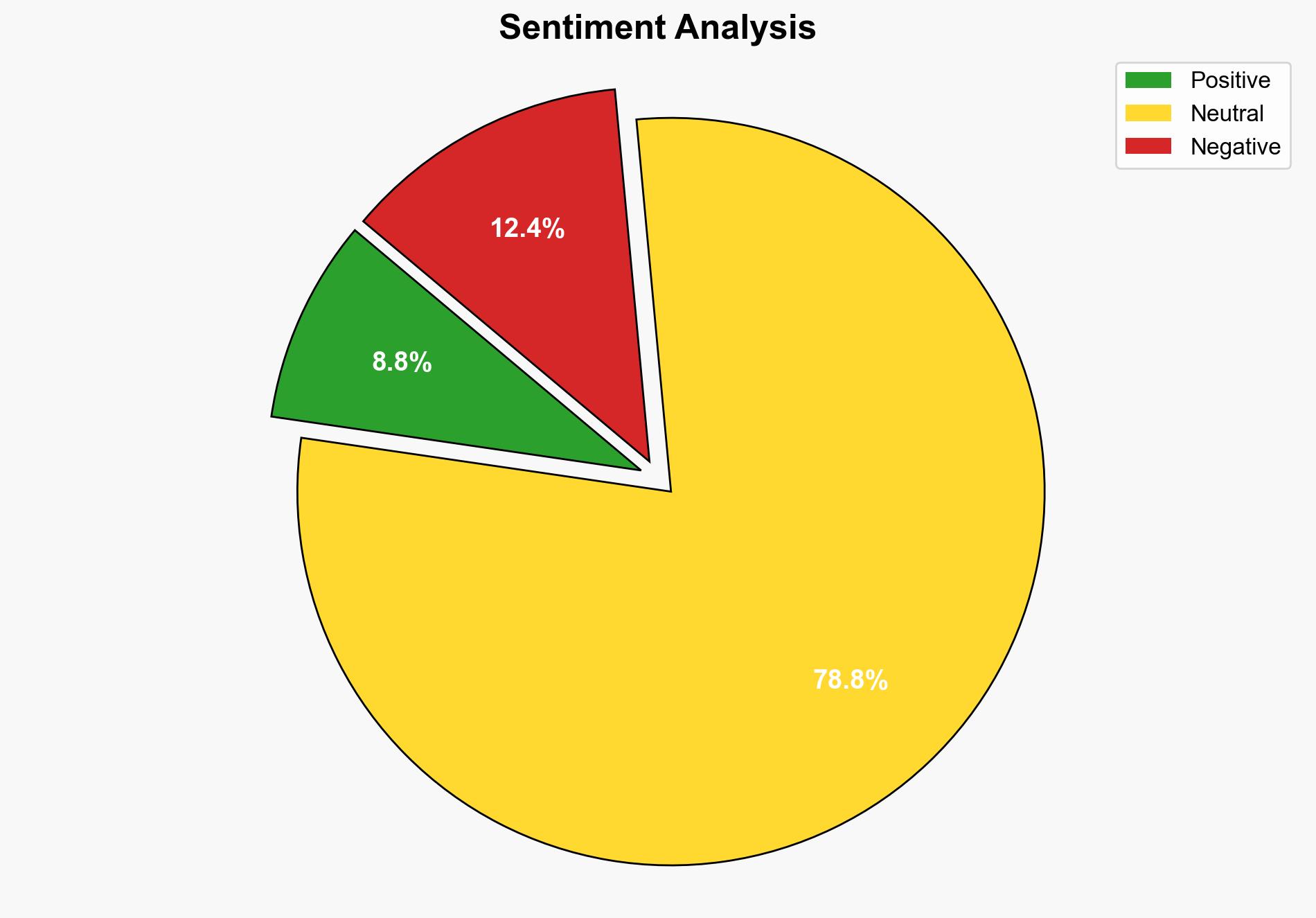
Intelligence Report: CitrixBleed 2 Vulnerability Exploited Recalling Earlier CitrixBleed Fallout – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
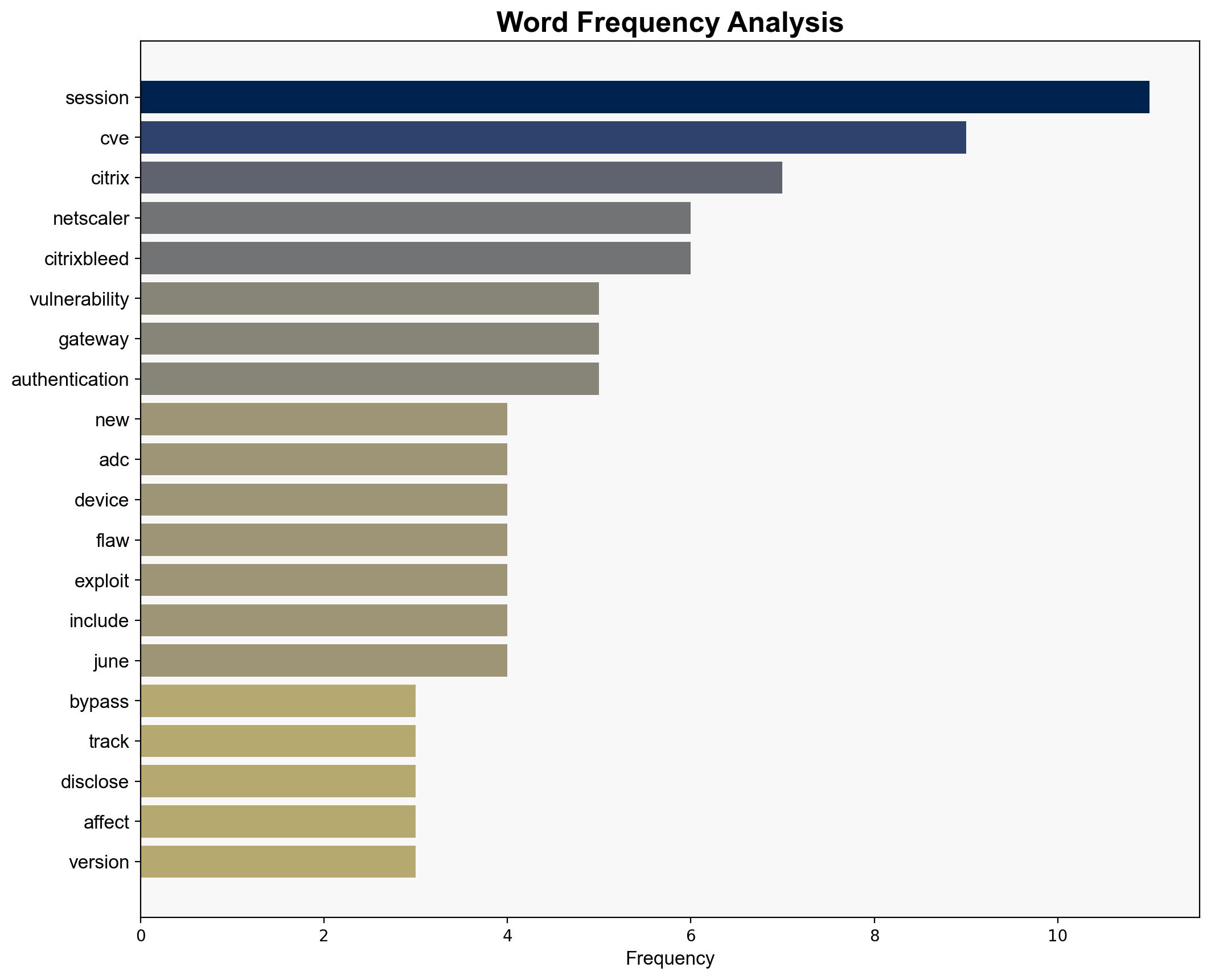
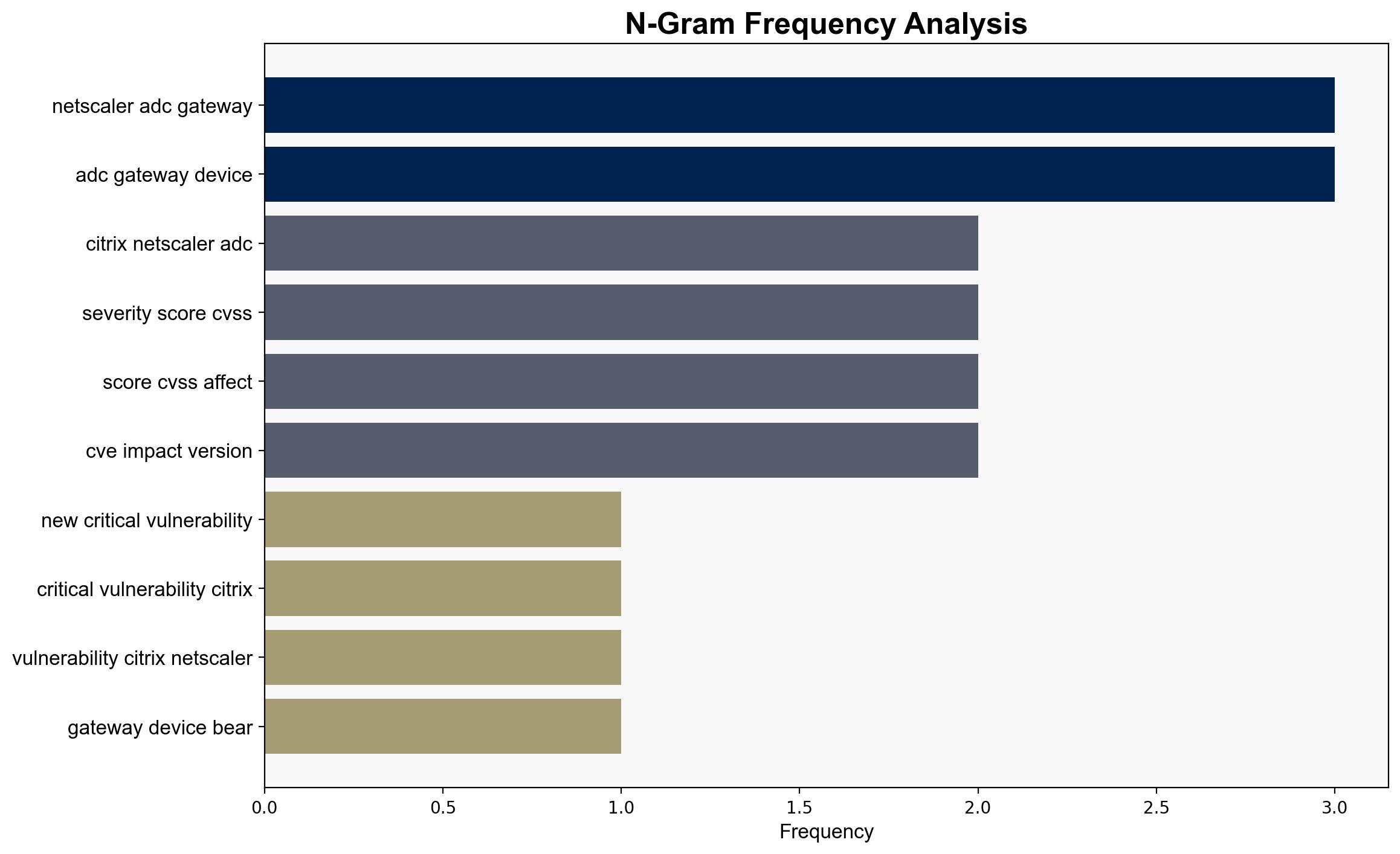
A new critical vulnerability, dubbed CitrixBleed 2, has been identified in Citrix NetScaler ADC and Gateway devices. This vulnerability allows attackers to bypass authentication mechanisms, including multifactor authentication (MFA), and hijack user sessions. The flaw is being actively exploited, posing significant risks to affected systems. Immediate action is recommended to mitigate potential breaches.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations indicate that attackers can exploit this vulnerability to gain unauthorized access, potentially leading to data breaches and system compromises.
Indicators Development
Key indicators include hijacked Citrix web sessions, suspicious IP combinations, and LDAP queries associated with Active Directory reconnaissance.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of continued exploitation, with potential pathways leading to widespread system infiltration.
3. Implications and Strategic Risks
The exploitation of CitrixBleed 2 could lead to significant disruptions in critical infrastructure, particularly in sectors reliant on Citrix systems. The vulnerability’s ability to bypass MFA increases the risk of unauthorized data access and potential ransomware attacks. Cross-domain risks include potential impacts on economic stability and national security.
4. Recommendations and Outlook
- Immediate patching of affected Citrix systems is critical to prevent exploitation.
- Enhance monitoring for indicators of compromise, focusing on session hijacking and unauthorized access attempts.
- Scenario-based projections suggest that without mitigation, the worst-case scenario could involve widespread data breaches and operational disruptions.
5. Key Individuals and Entities
Kevin Beaumont
6. Thematic Tags
national security threats, cybersecurity, vulnerability management, Citrix systems