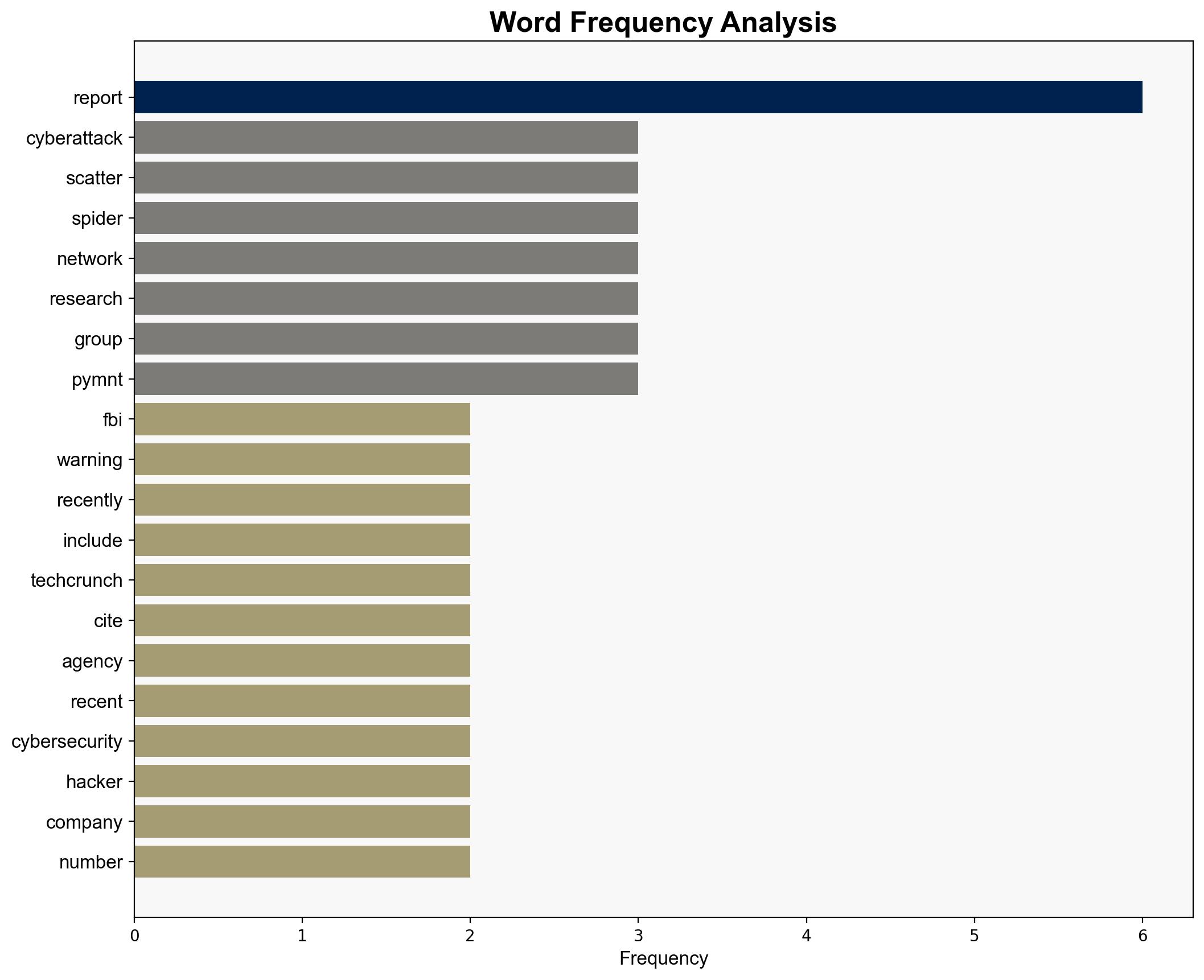
Scattered Spider Hackers Reportedly Targeting Airline Industry – pymnts.com
Published on: 2025-06-29
Intelligence Report: Scattered Spider Hackers Reportedly Targeting Airline Industry – pymnts.com
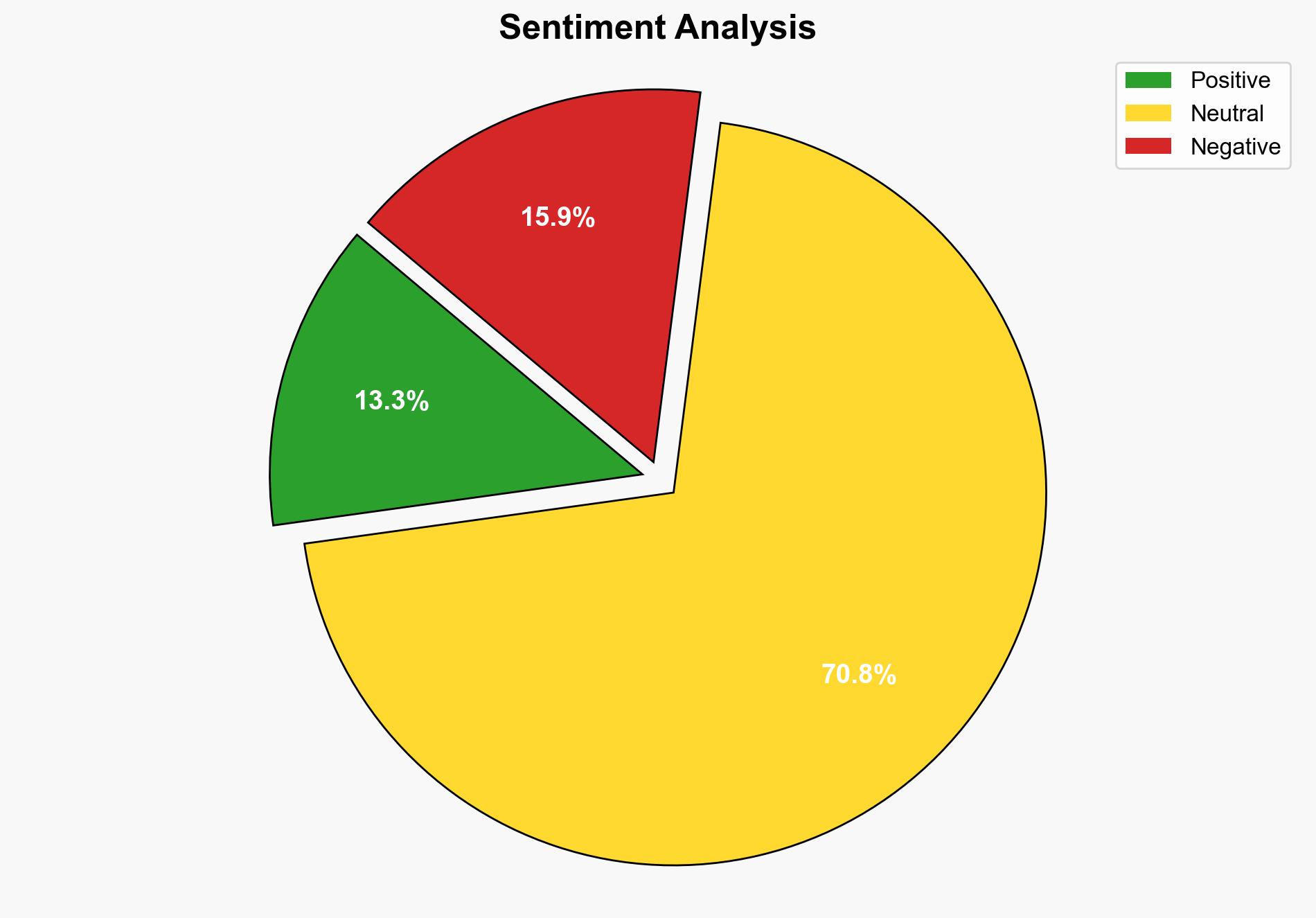
1. BLUF (Bottom Line Up Front)
Recent intelligence indicates that the hacker group known as Scattered Spider is actively targeting the airline industry. This group employs sophisticated tactics, including social engineering and phishing, to infiltrate networks. Their activities pose significant risks to the aviation sector and its associated supply chain. Immediate action is recommended to enhance cybersecurity measures and protect critical infrastructure.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Scattered Spider’s tactics have been modeled to anticipate potential vulnerabilities within airline networks, highlighting the need for robust defense mechanisms.
Indicators Development
Key indicators of compromise include unusual access patterns and phishing attempts targeting airline employees and contractors.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of continued attacks on the aviation sector, with potential expansion to other critical industries.
Network Influence Mapping
Mapping reveals Scattered Spider’s influence extends through a network of trusted vendors and contractors, increasing systemic risk.
3. Implications and Strategic Risks
The attacks on the airline industry could disrupt global travel and logistics, leading to economic repercussions. The interconnected nature of the aviation ecosystem means that breaches in one area could have cascading effects across the sector. Additionally, the group’s ability to target high-profile entities suggests a potential for broader geopolitical impacts.
4. Recommendations and Outlook
- Enhance cybersecurity protocols across the aviation sector, focusing on employee training and network security.
- Implement real-time monitoring systems to detect and respond to anomalies swiftly.
- Develop contingency plans to mitigate operational disruptions in the event of a cyberattack.
- Scenario-based projections:
- Best case: Strengthened defenses deter future attacks.
- Worst case: Successful breaches lead to significant operational and financial losses.
- Most likely: Continued attempts with varying degrees of success, necessitating ongoing vigilance.
5. Key Individuals and Entities
Brian Boat, a key figure in risk management, has emphasized the complexity of intervention in such scenarios.
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus