Flying kangaroo goes to ground on data breach – ABC News (AU)
Published on: 2025-07-03
Intelligence Report: Flying kangaroo goes to ground on data breach – ABC News (AU)
1. BLUF (Bottom Line Up Front)
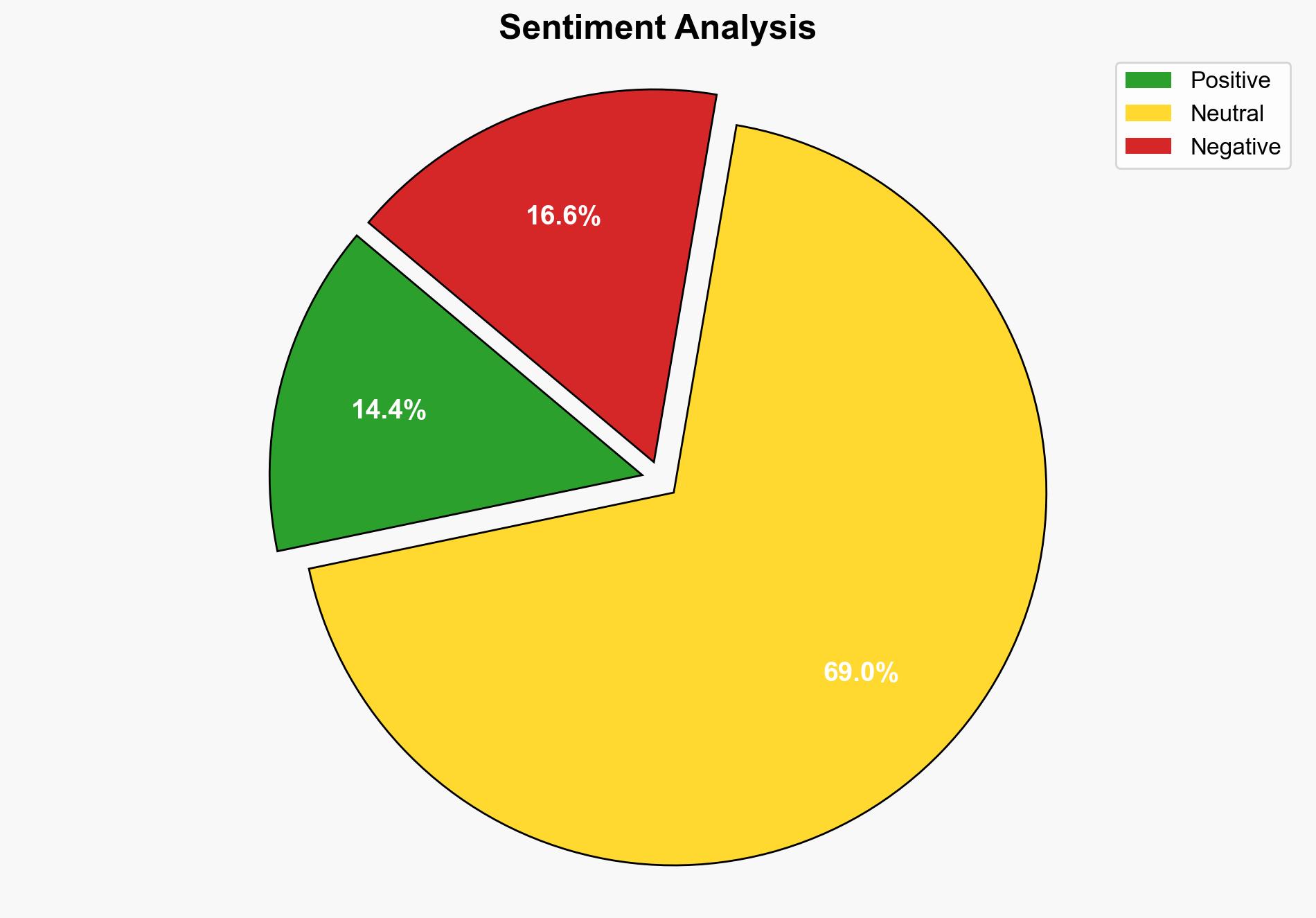
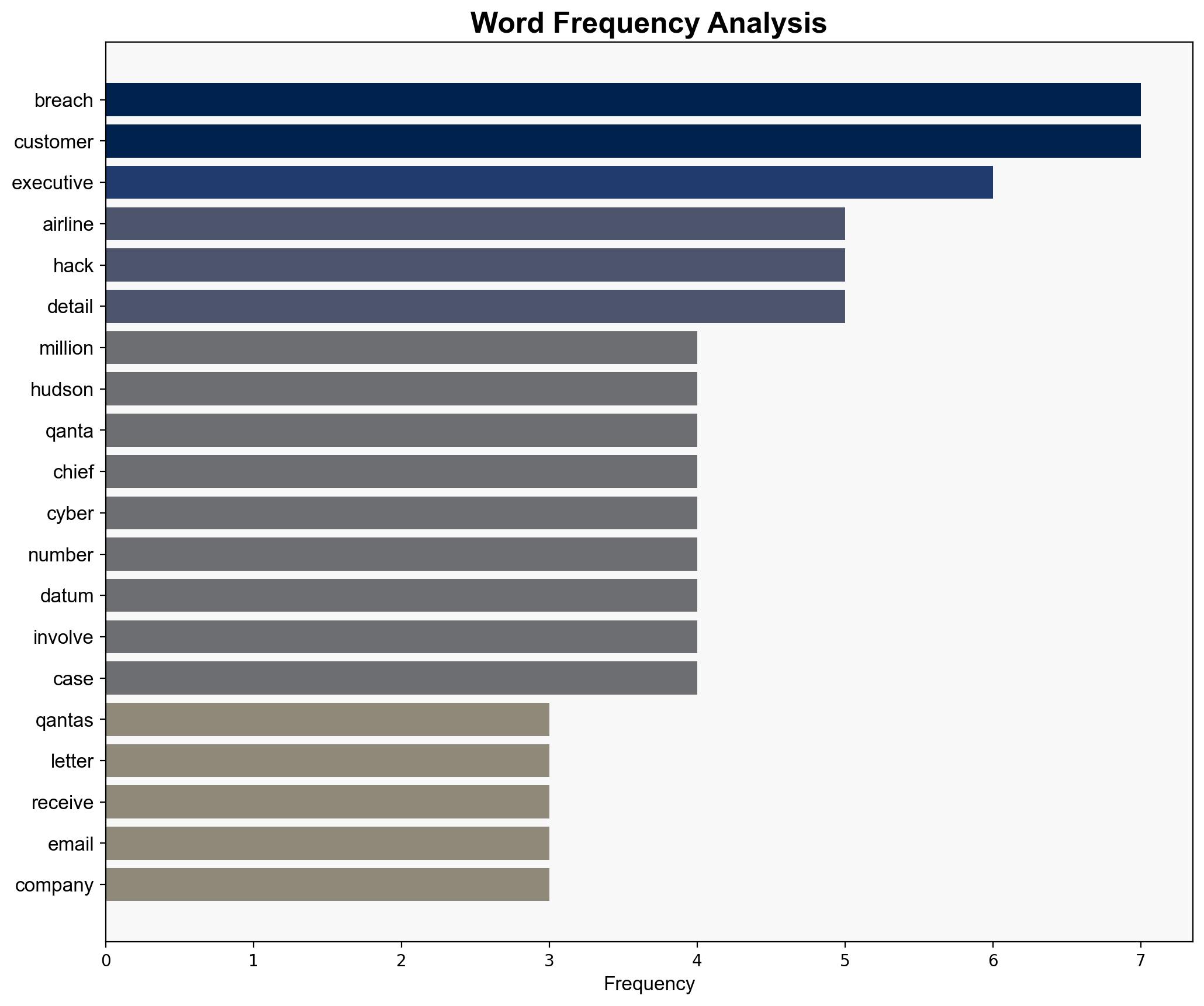
Qantas has experienced a significant data breach affecting millions of customers, exposing personal information but not financial details. The breach highlights vulnerabilities in outsourced operations and the need for robust cybersecurity measures. Immediate action is required to address customer concerns and strengthen data protection protocols.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Cyber adversaries exploited weaknesses in Qantas’s outsourced operations, particularly in Manila, to gain unauthorized access to customer data. This simulation underscores the importance of securing third-party vendor relationships.
Indicators Development
Monitoring for abnormal access patterns and unauthorized MFA device registrations could provide early warnings of similar breaches.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of future attacks targeting outsourced operations, emphasizing the need for enhanced security measures.
3. Implications and Strategic Risks
The breach exposes systemic vulnerabilities in Qantas’s reliance on third-party providers, posing risks to customer trust and corporate reputation. The incident may lead to increased regulatory scrutiny and potential financial penalties. Additionally, it highlights the broader risk of cyberattacks on critical infrastructure sectors.
4. Recommendations and Outlook
- Enhance cybersecurity protocols with a focus on third-party vendor management and employee training.
- Implement advanced threat detection systems to identify and mitigate potential breaches swiftly.
- Develop a comprehensive incident response plan to manage future breaches effectively.
- Scenario Projections:
- Best Case: Strengthened security measures prevent future breaches, restoring customer trust.
- Worst Case: Continued vulnerabilities lead to further breaches, damaging reputation and incurring regulatory penalties.
- Most Likely: Incremental improvements in security reduce breach frequency but require ongoing vigilance.
5. Key Individuals and Entities
Vanessa Hudson, Tony Burke, Alan Joyce, Ahmed Fahour, Kelly Bayer Rosmarin, David Koczkar
6. Thematic Tags
national security threats, cybersecurity, data breach, third-party risk, customer data protection