Ubuntu Security Flaw Lets Attackers Bypass Full Disk Encryption – Omgubuntu.co.uk
Published on: 2025-07-06
Intelligence Report: Ubuntu Security Flaw Lets Attackers Bypass Full Disk Encryption – Omgubuntu.co.uk
1. BLUF (Bottom Line Up Front)
A critical security vulnerability has been identified in several Linux distributions, including Ubuntu and Fedora, allowing attackers with physical access to bypass full disk encryption. This flaw is exploitable via a debug shell, which can be accessed by entering an incorrect decryption password multiple times. The vulnerability requires physical access, making it a significant risk for high-value targets rather than average users. Immediate mitigation strategies are recommended to prevent potential exploitation.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
The vulnerability allows adversaries to simulate physical access attacks, such as the “evil maid” scenario, where an attacker gains access to a device left unattended. This simulation highlights the need for robust physical security measures.
Indicators Development
Key indicators include unauthorized access attempts, unusual boot sequences, and the presence of modified initramfs files. Monitoring these can aid in early detection of exploitation attempts.
Bayesian Scenario Modeling
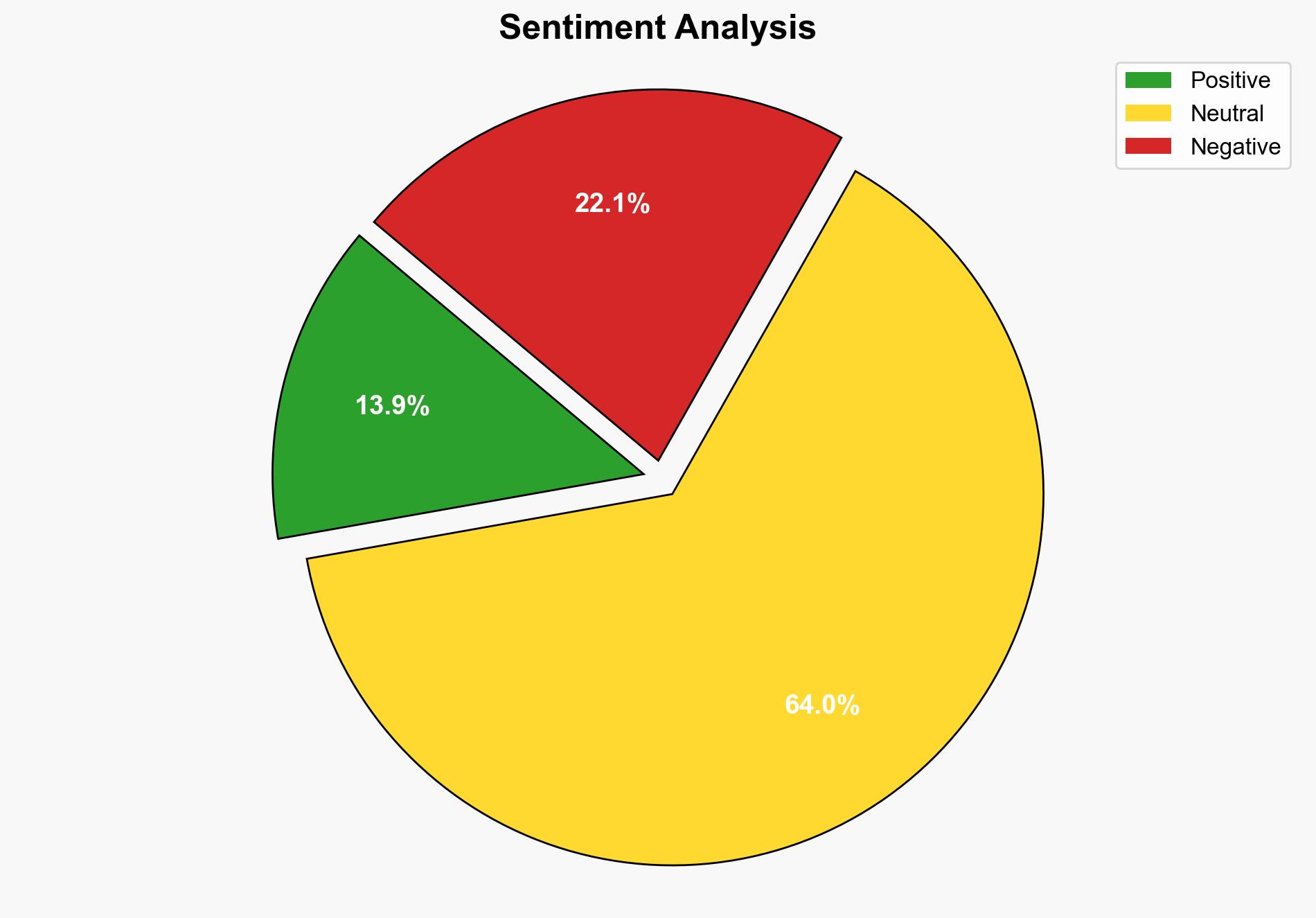
The likelihood of exploitation is higher in environments with lax physical security. Probabilistic modeling suggests that while the average user faces low risk, high-value targets should prioritize mitigation.
3. Implications and Strategic Risks
The vulnerability poses a strategic risk primarily to organizations and individuals with sensitive data, such as government agencies and political activists. The potential for data theft or system compromise could have cascading effects on national security and privacy. The flaw underscores the importance of securing physical access to devices.
4. Recommendations and Outlook
- Implement physical security measures to prevent unauthorized access to devices.
- Modify system kernel parameters to disable the debug shell upon failed password attempts.
- Ensure initramfs files are signed and verified during the boot process.
- Scenario Projections:
- Best Case: Vulnerability is patched swiftly, with minimal exploitation incidents.
- Worst Case: High-profile targets experience data breaches, leading to significant political and economic repercussions.
- Most Likely: Targeted attacks on high-value individuals or organizations, with limited impact on the general user base.
5. Key Individuals and Entities
Alexander Moch, ERNW
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus