How a tied shoelace will mark a turning point in US history – CNN
Published on: 2025-07-09
Intelligence Report: How a tied shoelace will mark a turning point in US history – CNN
1. BLUF (Bottom Line Up Front)
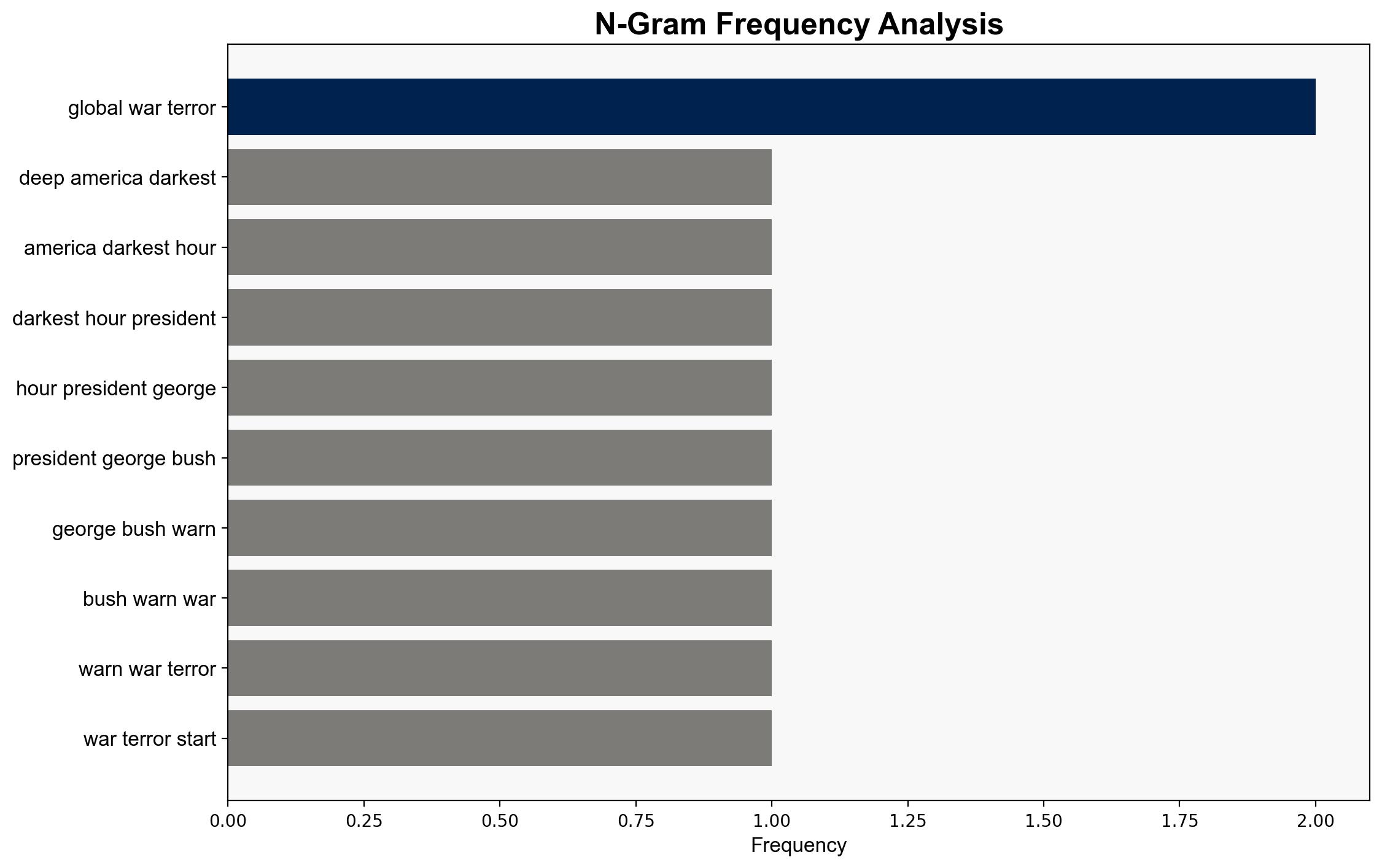
The article discusses the symbolic end of an era marked by the Global War on Terror, initiated after the September 11 attacks. The removal of the shoe-removal requirement at airports signifies a shift in security protocols and reflects broader geopolitical changes. The report identifies key strategic shifts, including the transition from counter-terrorism to great power competition, primarily involving the United States, China, and Russia. Recommendations focus on adapting to new security paradigms and addressing emerging geopolitical challenges.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Causal Layered Analysis (CLA)
Surface events include the end of the shoe-removal requirement, representing a shift in security measures. Systemic structures involve evolving security technologies and changing geopolitical priorities. The worldview reflects a move from a terrorism-focused narrative to addressing great power competition. Myths include the enduring impact of 9/11 on American security policy.
Cross-Impact Simulation
The shift in security focus may influence international relations, particularly with allies and adversaries. The reallocation of resources from counter-terrorism to addressing threats from China and Russia could alter global power dynamics and economic dependencies.
Scenario Generation
Scenarios explore potential futures where the U.S. successfully transitions to addressing great power competition, or where challenges in adapting to new threats lead to strategic vulnerabilities. Scenarios also consider the impact of domestic political changes on foreign policy.
3. Implications and Strategic Risks
The transition from a terrorism-focused security strategy to addressing great power competition presents risks, including potential underestimation of non-state threats. Cybersecurity and economic vulnerabilities may be exploited by adversaries. The shift could also lead to domestic political tensions as resources are reallocated.
4. Recommendations and Outlook
- Enhance cybersecurity measures to protect against state and non-state actors.
- Invest in intelligence capabilities to monitor and counter emerging threats from great powers.
- Foster international alliances to address shared security challenges.
- Scenario-based projections: Best case involves successful adaptation to new security paradigms; worst case includes strategic missteps leading to increased vulnerabilities; most likely scenario involves gradual adaptation with intermittent challenges.
5. Key Individuals and Entities
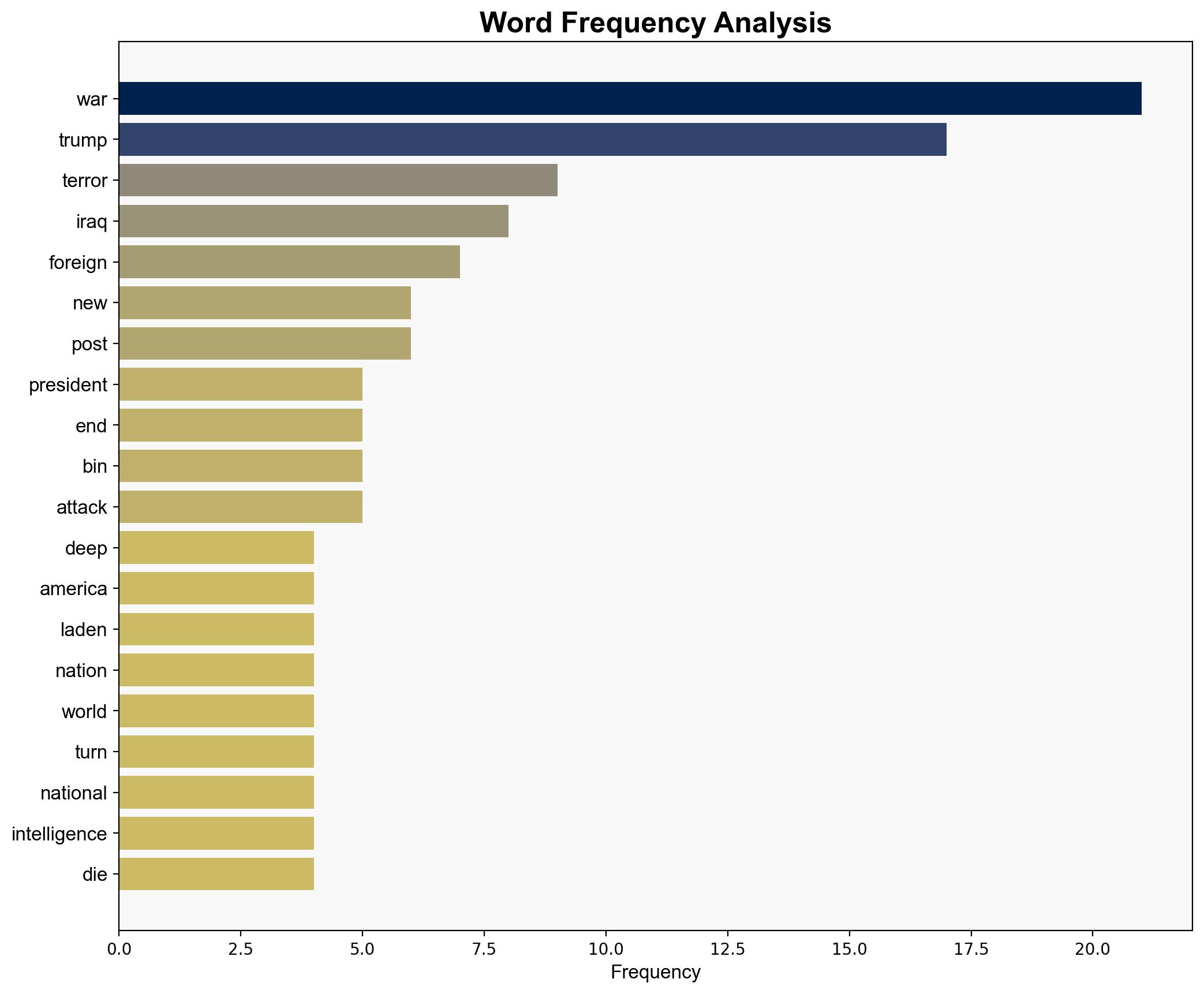
George Bush, Osama bin Laden, Kristi Noem, Barack Obama, Donald Trump
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus