MacOS Infostealer AMOS Evolves with Backdoor for Persistent Access – Infosecurity Magazine
Published on: 2025-07-09
Intelligence Report: MacOS Infostealer AMOS Evolves with Backdoor for Persistent Access – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
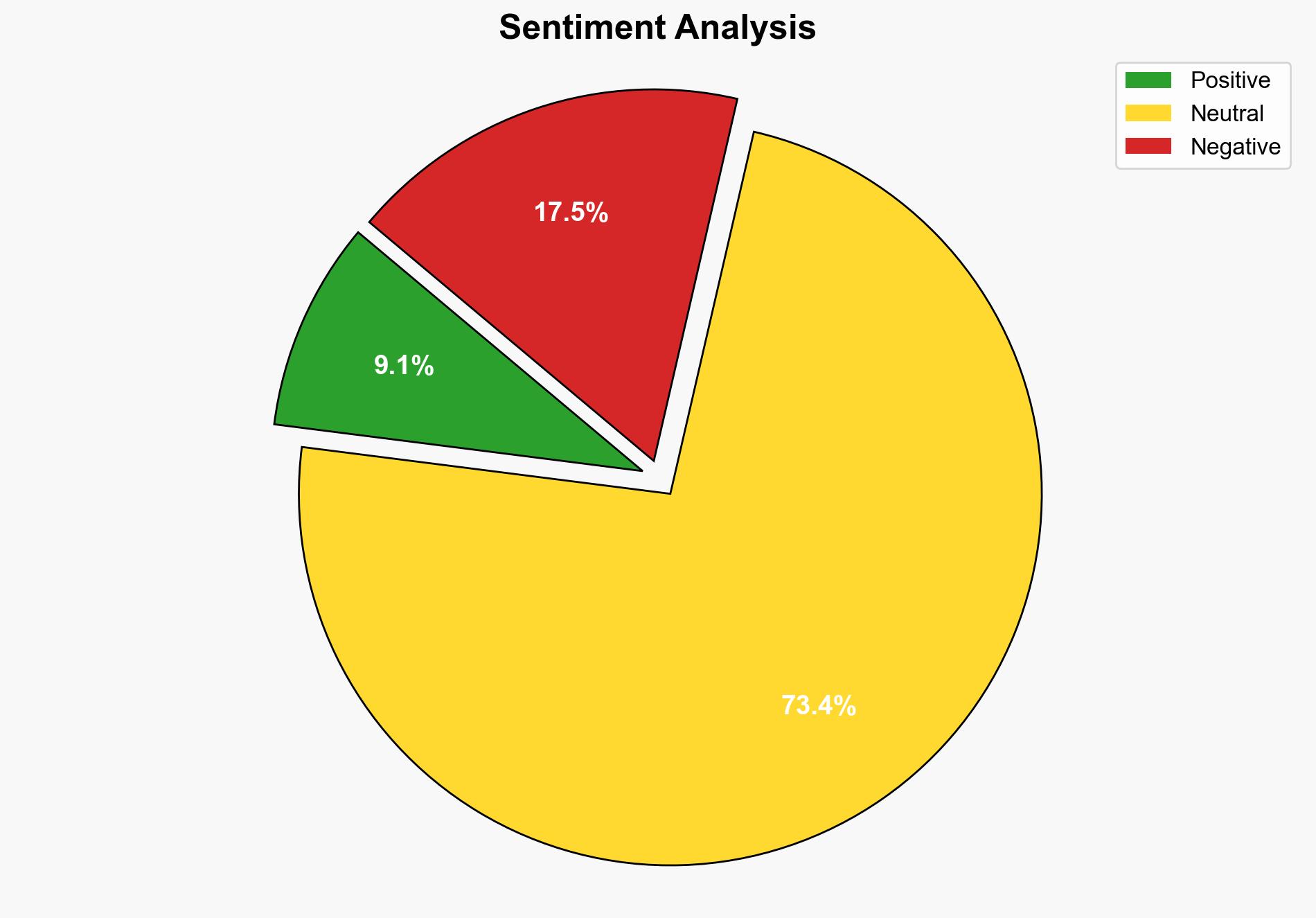
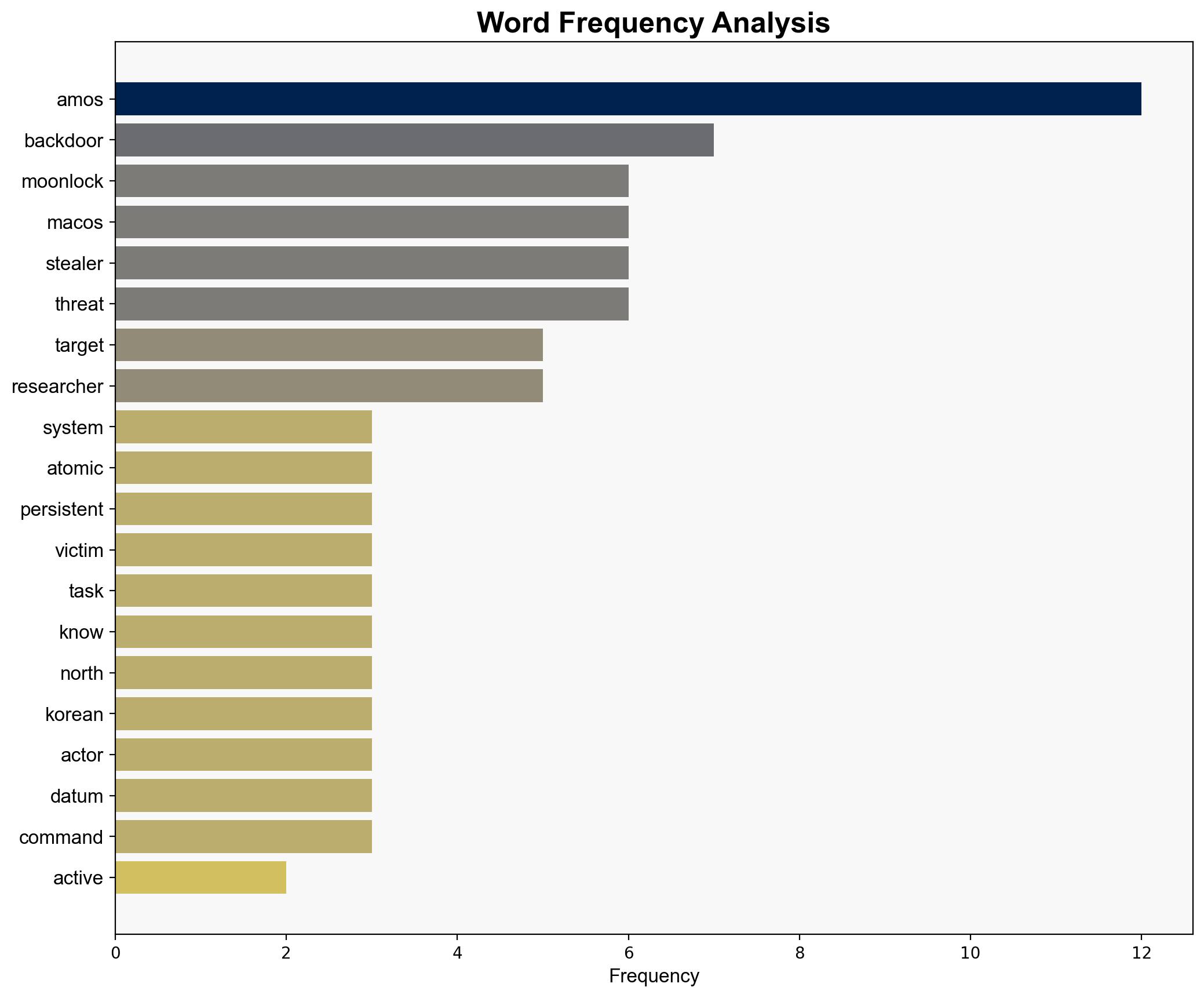
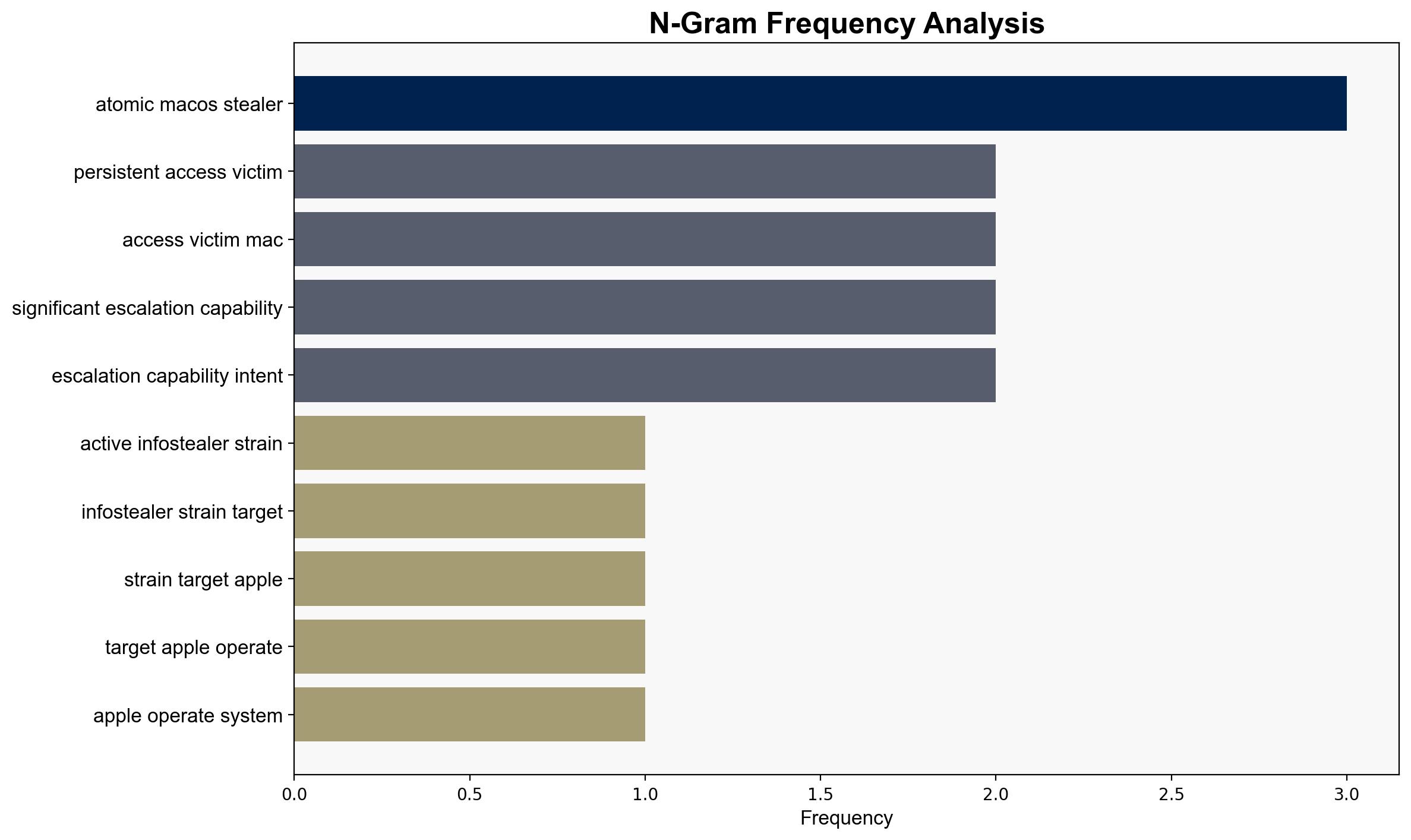
The AMOS infostealer, targeting MacOS systems, has evolved into a more dangerous tool with the addition of a backdoor, enabling persistent access and extended control over compromised machines. This development poses significant risks to MacOS users globally, particularly high-value targets such as cryptocurrency owners. Immediate action is recommended to bolster defenses against this threat.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
AMOS’s evolution suggests a sophisticated adversarial approach, likely involving state-sponsored actors. Simulation of potential attack vectors can aid in identifying vulnerabilities and enhancing defensive measures.
Indicators Development
Key indicators include unusual network traffic, unauthorized access attempts, and the presence of known malicious signatures related to AMOS. Continuous monitoring for these indicators is crucial for early detection.
Bayesian Scenario Modeling
Probabilistic models predict that AMOS will continue to evolve, potentially incorporating additional capabilities such as keylogging. This scenario underscores the need for adaptive security measures.
3. Implications and Strategic Risks
The integration of a backdoor in AMOS represents a strategic escalation in cyber threats against MacOS users. This could lead to widespread data breaches, financial losses, and compromised personal information. The involvement of North Korean threat actors suggests potential geopolitical implications, increasing tensions in cyber diplomacy and international relations.
4. Recommendations and Outlook
- Enhance endpoint security measures and conduct regular system audits to detect and mitigate AMOS-related threats.
- Implement user education programs to recognize and avoid phishing attempts, a common delivery method for AMOS.
- Scenario-based projections:
- Best Case: Rapid detection and patching of vulnerabilities limit AMOS’s impact.
- Worst Case: Widespread exploitation leads to significant data breaches and financial losses.
- Most Likely: Continued evolution of AMOS with incremental improvements in attack sophistication.
5. Key Individuals and Entities
The report does not specify individual names but highlights the involvement of North Korean threat actors and Russian-based groups in the development and deployment of AMOS.
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus