UK set up secret Afghan relocation scheme after major breach – BBC News
Published on: 2025-07-15
Intelligence Report: UK set up secret Afghan relocation scheme after major breach – BBC News
1. BLUF (Bottom Line Up Front)
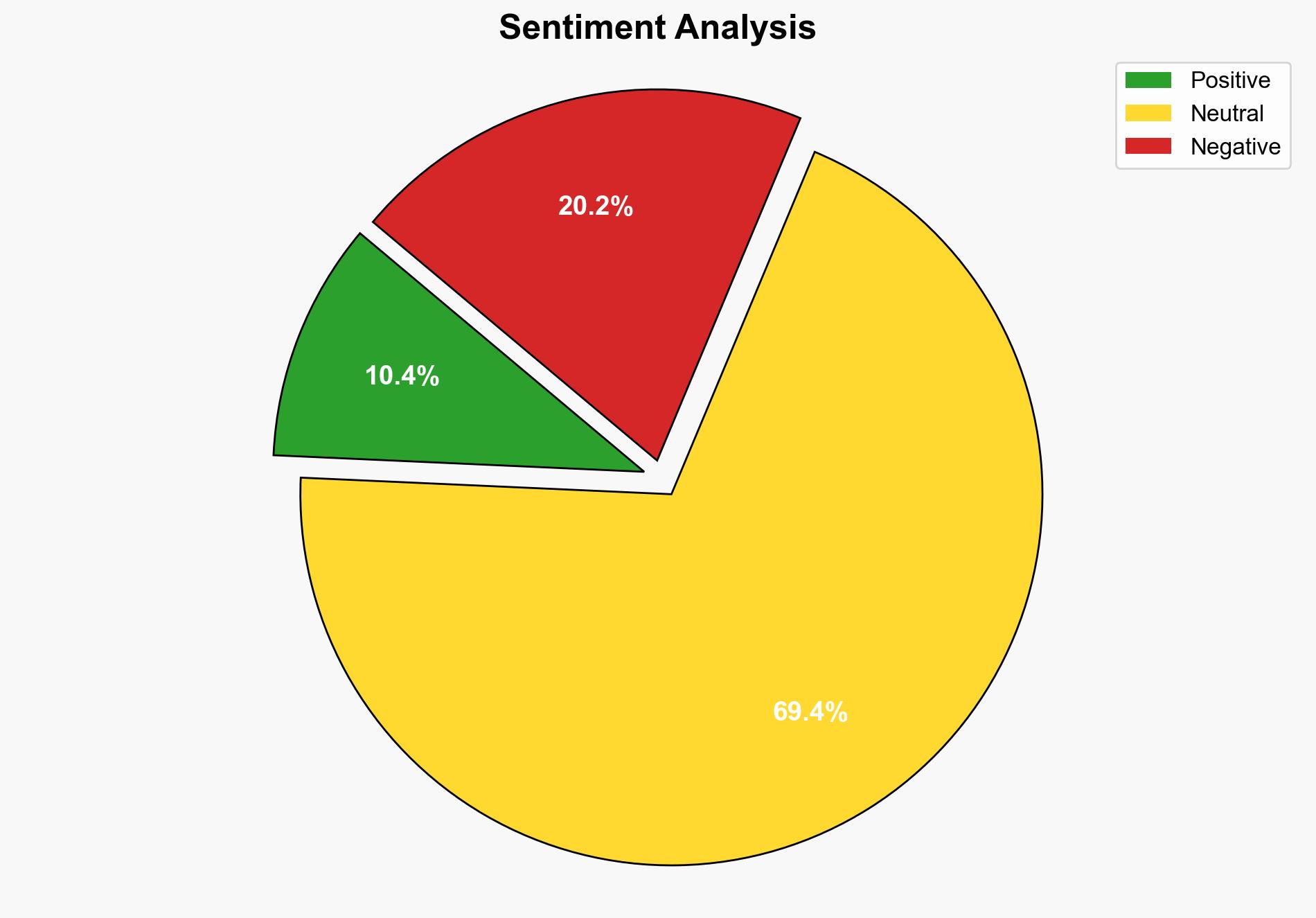
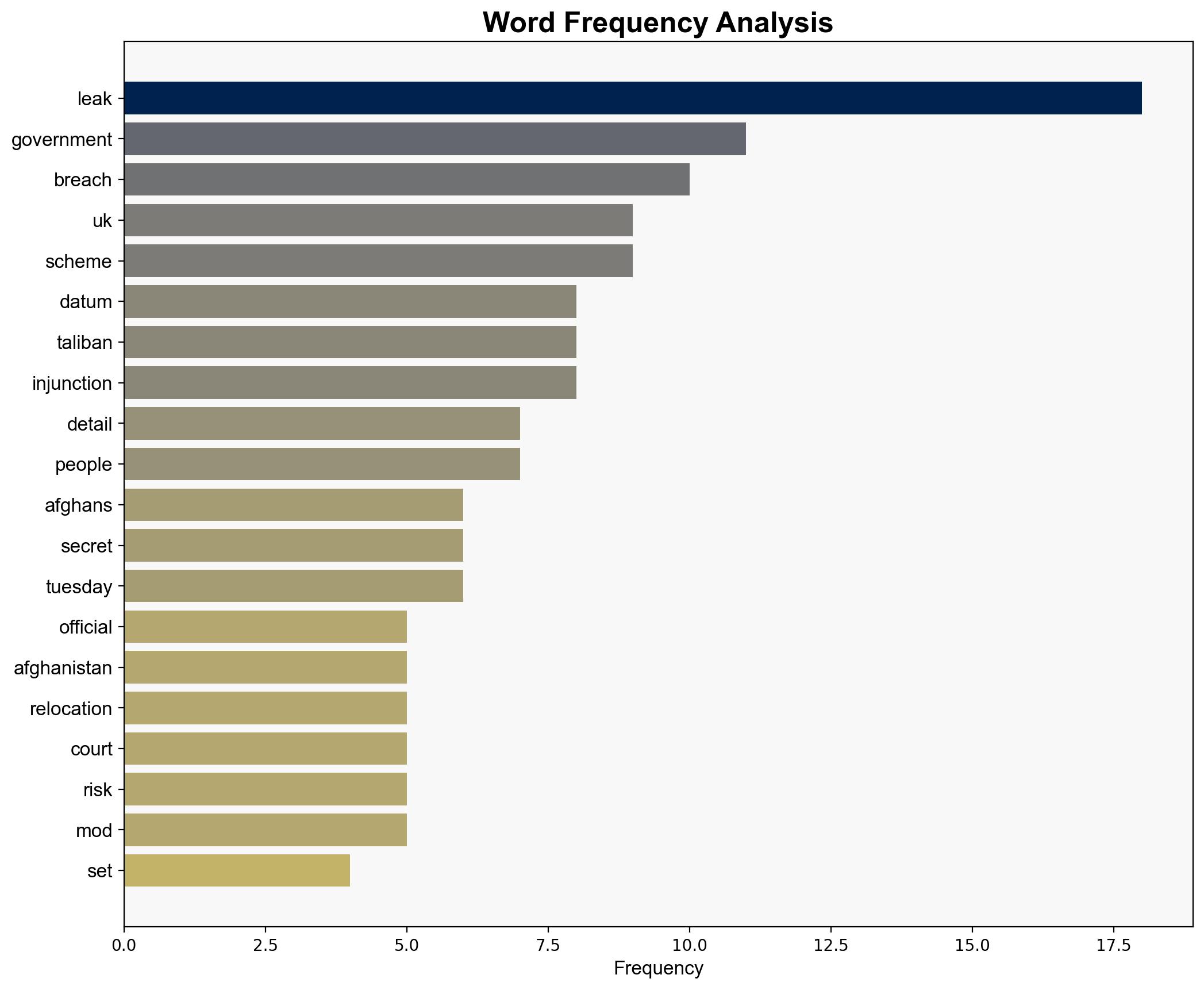
The UK government established a clandestine Afghan relocation scheme following a significant data breach that exposed personal details of individuals applying for relocation. This breach posed potential risks to those listed, including threats from the Taliban. The scheme’s secrecy was maintained through a super injunction, which has now been lifted, revealing the extent of the breach and subsequent relocation efforts. Recommendations include enhancing data security protocols and improving crisis communication strategies.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
ACH 2.0
Reconstructing the intentions behind the data breach suggests it was an inadvertent error rather than a deliberate act. The rapid response in setting up a secret relocation scheme indicates a high priority on mitigating risks to affected individuals.
Indicators Development
Monitoring digital communications and travel patterns of those relocated could provide early warnings of potential threats or radicalization attempts by hostile actors.
Narrative Pattern Analysis
The breach narrative may be exploited by adversaries to undermine trust in government processes, necessitating careful management of public communications to prevent misinformation.
3. Implications and Strategic Risks
The data breach underscores vulnerabilities in handling sensitive information, with potential repercussions on national security and diplomatic relations. The exposure of personal details could lead to targeted threats against individuals by the Taliban. Additionally, the incident may erode public confidence in government capabilities to manage sensitive operations.
4. Recommendations and Outlook
- Enhance cybersecurity measures to prevent future data breaches, including regular audits and staff training.
- Develop a robust crisis management framework to swiftly address data breaches and communicate effectively with affected parties.
- Scenario-based projections:
- Best Case: Strengthened security protocols prevent future breaches, and relocated individuals integrate successfully.
- Worst Case: Further breaches occur, leading to increased threats against relocated individuals and diplomatic fallout.
- Most Likely: Incremental improvements in data security reduce breach risks, but ongoing vigilance is required.
5. Key Individuals and Entities
John Healey, Kemi Badenoch, Justice Chamberlain
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus