OpenAI Vulnerability 48 Days No Response – Any.org
Published on: 2025-07-15
Intelligence Report: OpenAI Vulnerability 48 Days No Response – Any.org
1. BLUF (Bottom Line Up Front)
A vulnerability in OpenAI’s system was reported but remained unaddressed for 48 days, potentially exposing sensitive user data. The issue stems from a tokenization bug affecting audio inputs, leading to unintended data exposure. OpenAI’s delayed response highlights a need for improved vulnerability management and communication protocols. Immediate action is recommended to patch the vulnerability and enhance disclosure practices.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
The vulnerability allows adversaries to exploit the system’s flaw, potentially accessing confidential user data. Simulations suggest that attackers could use this flaw to extract sensitive information, emphasizing the need for robust security measures.
Indicators Development
Monitoring for unusual data access patterns and unauthorized data retrieval attempts can help detect exploitation of this vulnerability. Implementing real-time alerts for such anomalies is crucial.
Bayesian Scenario Modeling
Probabilistic models indicate a moderate likelihood of exploitation if the vulnerability remains unpatched. The potential impact includes data breaches and loss of user trust, necessitating immediate remediation.
Narrative Pattern Analysis
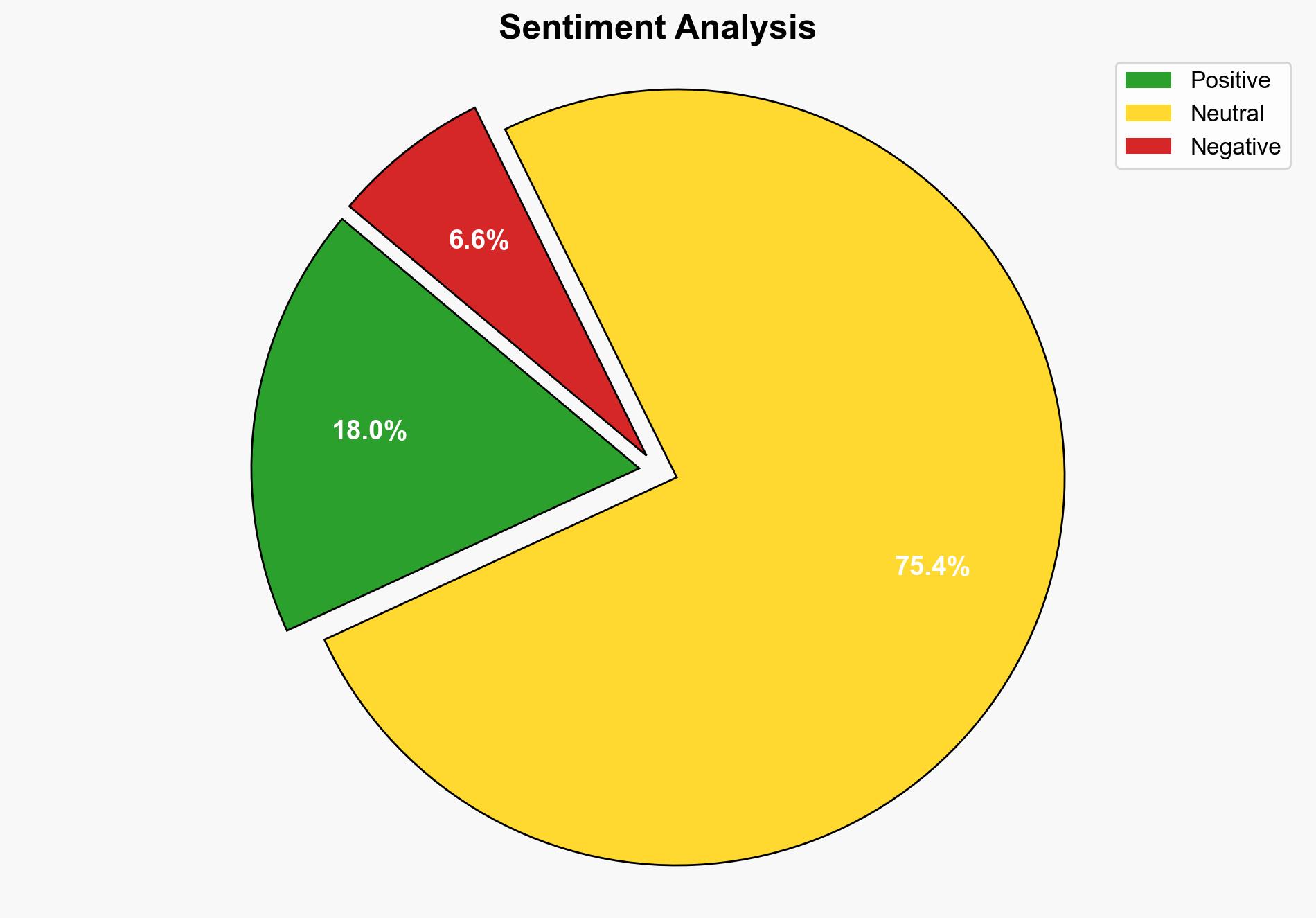
The narrative surrounding OpenAI’s response to the vulnerability reflects broader concerns about transparency and accountability in tech companies. Addressing these issues is vital for maintaining public trust.
3. Implications and Strategic Risks
The unpatched vulnerability poses significant risks to user privacy and data security. Failure to address the issue promptly could lead to reputational damage for OpenAI and increased scrutiny from regulatory bodies. Additionally, the incident underscores the importance of timely and transparent communication in vulnerability management.
4. Recommendations and Outlook
- Patch the identified vulnerability immediately and conduct a comprehensive security audit to identify other potential weaknesses.
- Revise and publish a clear vulnerability response policy with defined service-level objectives (SLOs) to ensure timely responses.
- Enhance communication channels to ensure that security reports receive prompt human attention.
- Implement regular third-party penetration testing to strengthen security posture.
- Best Case: Rapid patch deployment and improved communication restore user trust and mitigate risks.
- Worst Case: Continued delays in addressing vulnerabilities lead to data breaches and regulatory penalties.
- Most Likely: OpenAI addresses the vulnerability but faces ongoing scrutiny over its response practices.
5. Key Individuals and Entities
No specific individuals are mentioned in the source text. The focus remains on OpenAI as the primary entity involved.
6. Thematic Tags
national security threats, cybersecurity, data privacy, vulnerability management, corporate accountability