NSA says Volt Typhoon was not successful at persisting in critical infrastructure – TechRadar
Published on: 2025-07-16
Intelligence Report: NSA says Volt Typhoon was not successful at persisting in critical infrastructure – TechRadar
1. BLUF (Bottom Line Up Front)
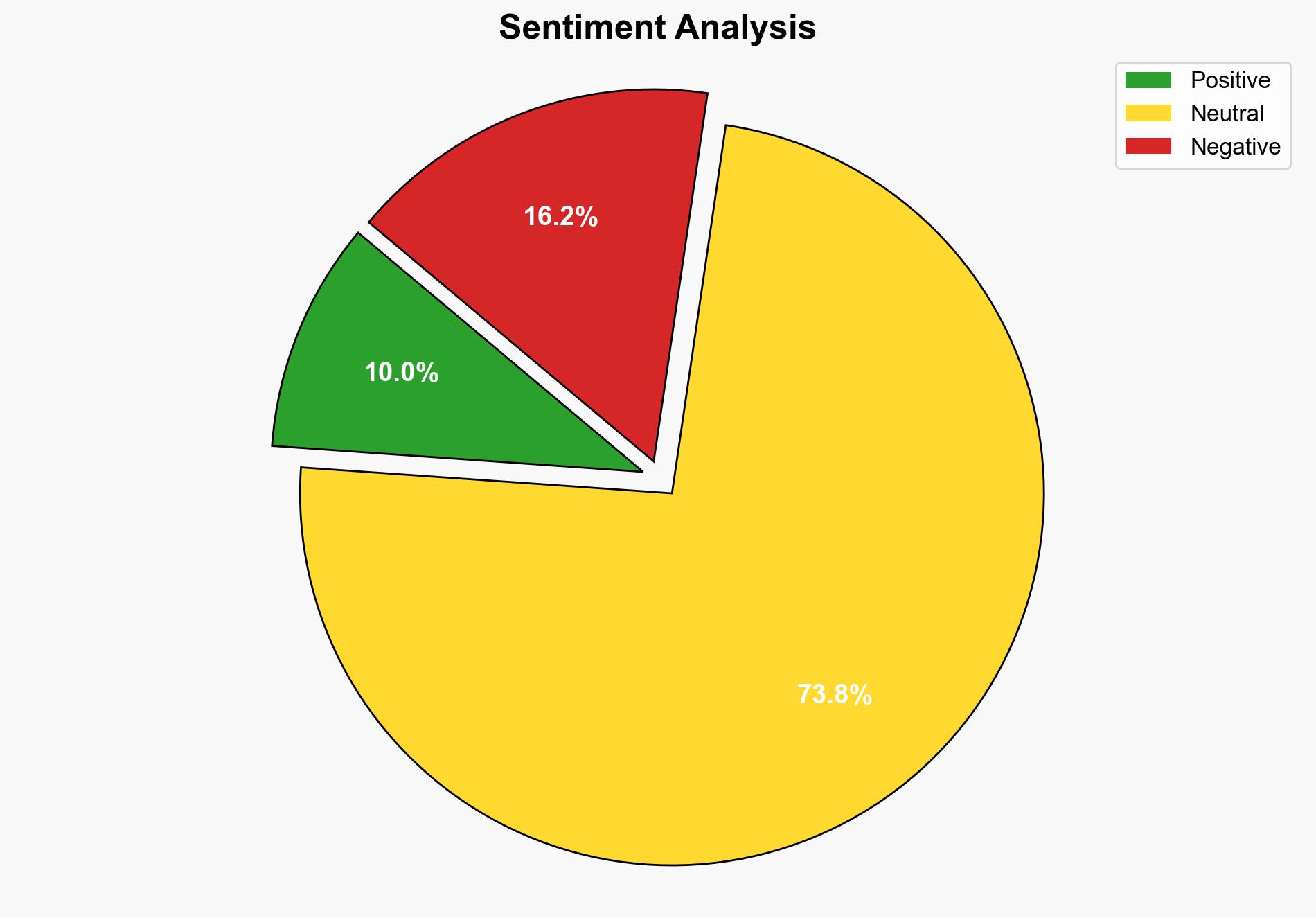
The NSA has confirmed that the Chinese state-sponsored threat actor known as Volt Typhoon was unsuccessful in maintaining long-term persistence within critical infrastructure networks. Despite initial access, the campaign failed to achieve its objective of remaining undetected over time. This report recommends enhancing cybersecurity measures and collaboration between government and private sectors to prevent future threats.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Cognitive Bias Stress Test
Potential biases were addressed through red teaming exercises, ensuring that assessments of Volt Typhoon’s capabilities and intentions were thoroughly challenged and validated.
Bayesian Scenario Modeling
Probabilistic forecasting suggests a low likelihood of immediate escalation but highlights the potential for increased cyber activities in the event of heightened tensions over Taiwan.
Network Influence Mapping
Analysis of influence networks indicates that Volt Typhoon’s activities are part of a broader strategy to prepare for potential geopolitical conflicts, particularly concerning Taiwan.
3. Implications and Strategic Risks
The failure of Volt Typhoon to maintain persistence reduces immediate risks but underscores the ongoing threat of state-sponsored cyber activities targeting critical infrastructure. The campaign highlights vulnerabilities that could be exploited in future conflicts, particularly in regions with significant geopolitical tensions such as Taiwan.
4. Recommendations and Outlook
- Enhance joint cybersecurity initiatives between government agencies and the private sector to improve detection and response capabilities.
- Conduct regular security audits and penetration testing to identify and mitigate vulnerabilities within critical infrastructure networks.
- Scenario-based projections suggest that in the best case, improved defenses deter future attacks; in the worst case, failure to act could lead to successful breaches with significant impact.
5. Key Individuals and Entities
Kristina Walter
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus