How were identities of thousands of Afghan refugees leaked by UK military – Al Jazeera English
Published on: 2025-07-17
Intelligence Report: How were identities of thousands of Afghan refugees leaked by UK military – Al Jazeera English
1. BLUF (Bottom Line Up Front)
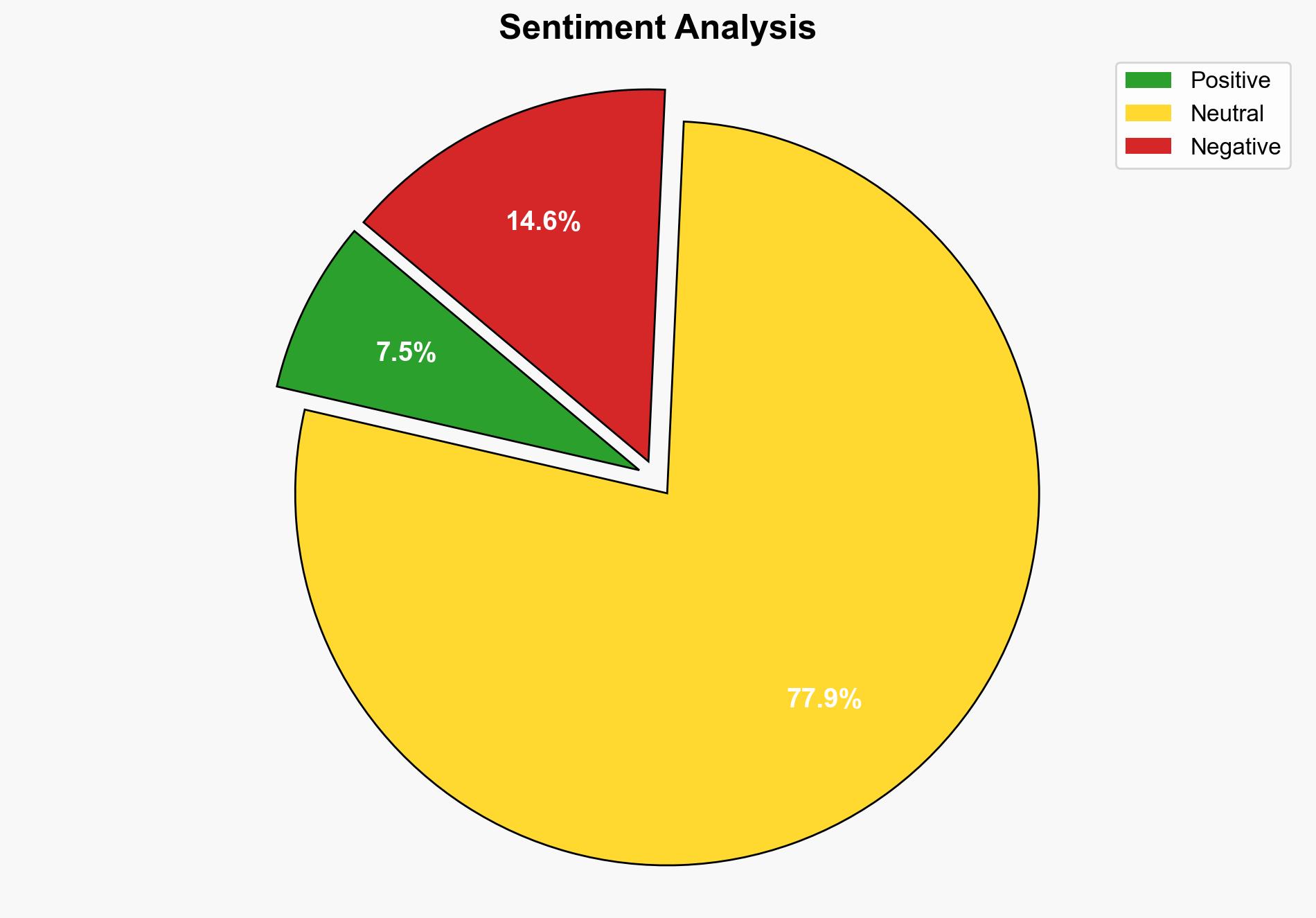
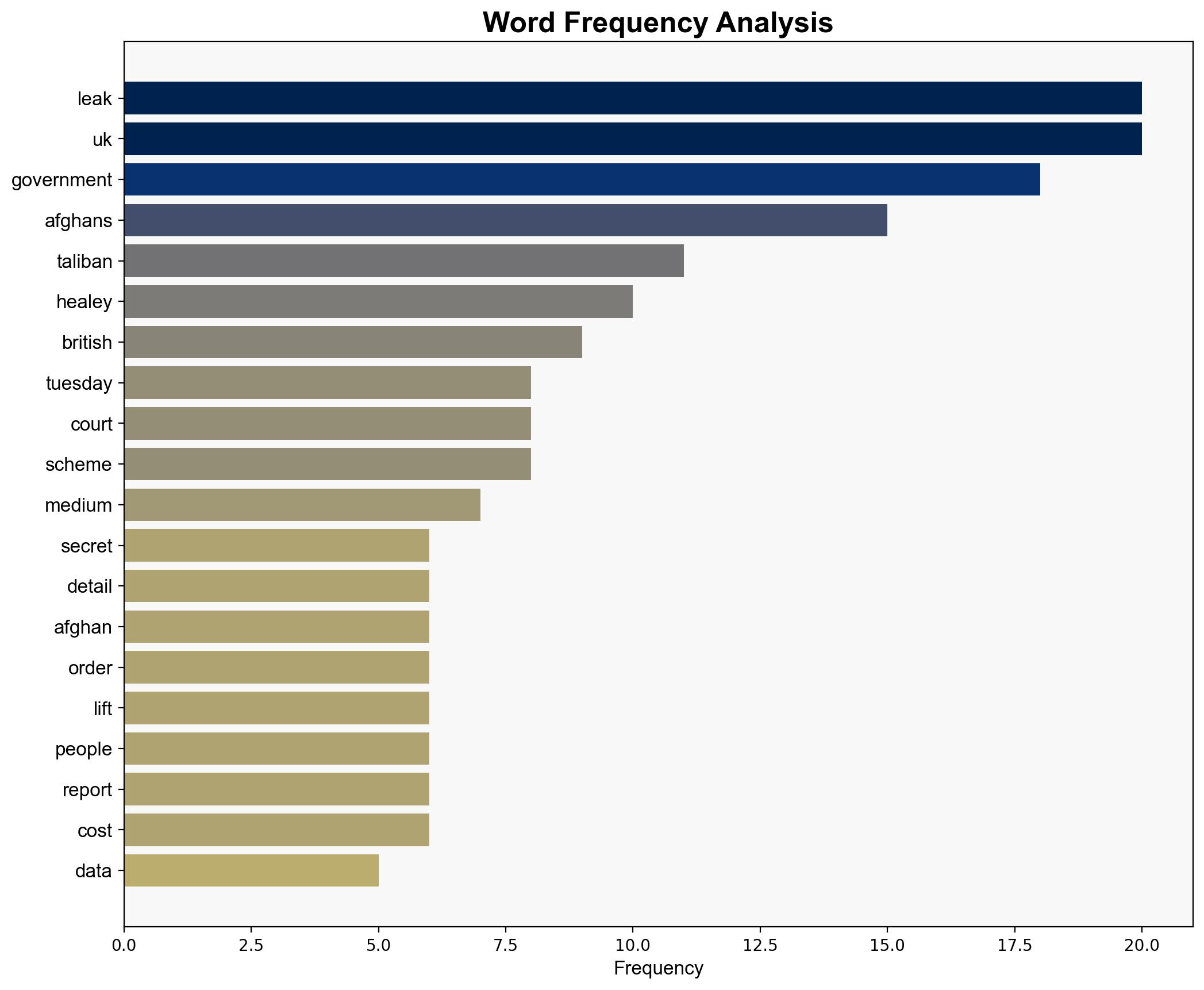
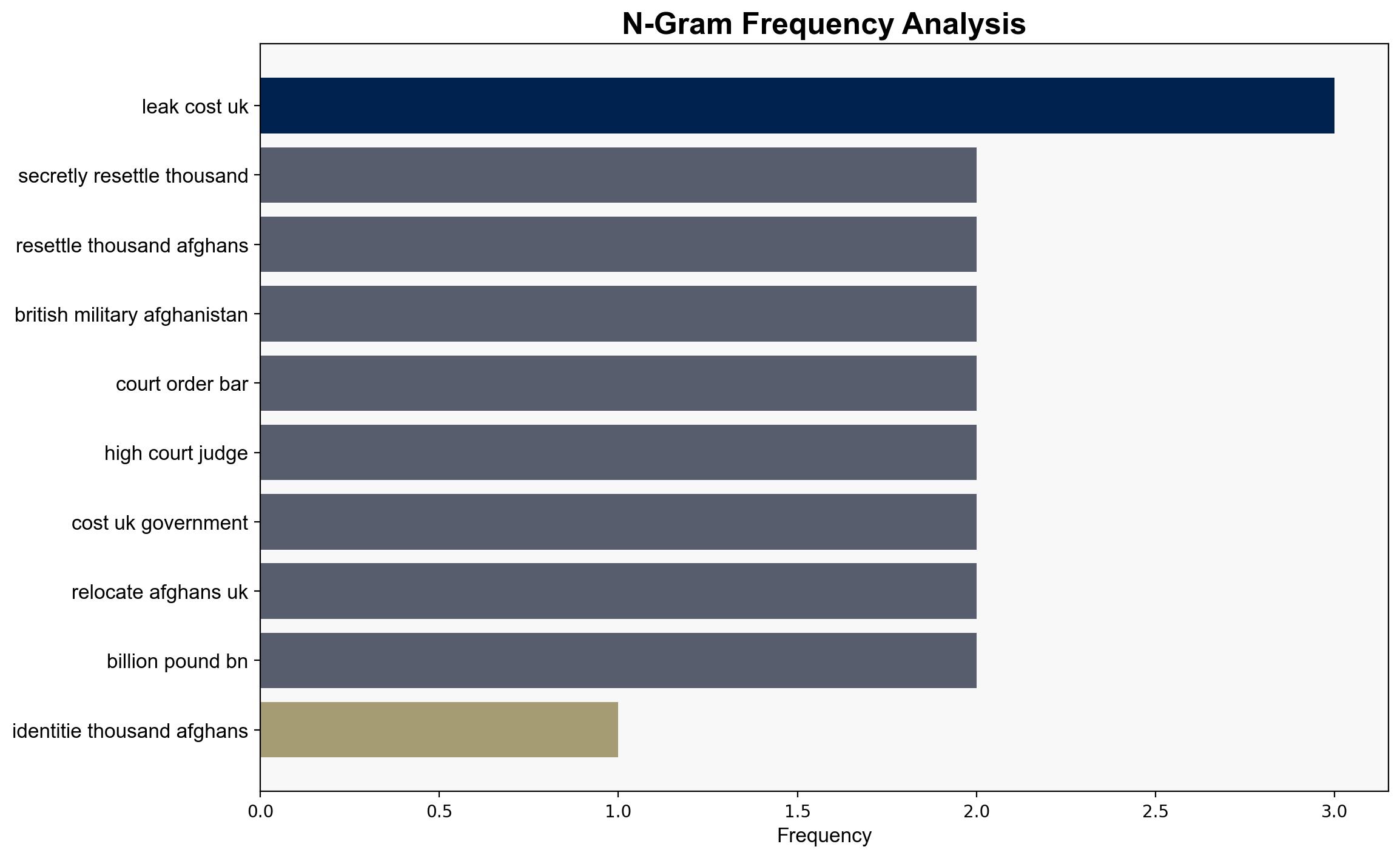
A significant data breach involving the identities of Afghan refugees occurred within the UK military, potentially exposing individuals to Taliban reprisals. The breach was initially kept secret under a superinjunction, which has now been lifted. This incident underscores vulnerabilities in data handling and the need for enhanced security measures to protect sensitive information.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
ACH 2.0
The breach appears to be accidental, resulting from a misunderstanding of the database content by military personnel. The intention was not malicious but highlights critical lapses in data management protocols.
Indicators Development
The leak could potentially be exploited by hostile actors to track and target Afghan refugees. Monitoring online platforms for any signs of radicalization or targeting efforts is crucial.
Narrative Pattern Analysis
The breach narrative may be used by adversaries to undermine trust in UK government operations and refugee protection efforts, potentially fueling propaganda efforts.
Network Influence Mapping
The incident has drawn attention from activists and media, influencing public perception and government accountability. Understanding these influence networks is key to managing the fallout.
3. Implications and Strategic Risks
The data breach poses significant risks, including potential targeting of Afghan refugees by the Taliban, reputational damage to the UK government, and increased scrutiny of military data handling practices. There is a risk of cascading effects, such as heightened tensions in refugee communities and increased pressure on government resources.
4. Recommendations and Outlook
- Enhance data protection protocols and conduct comprehensive audits of current systems to prevent future breaches.
- Develop contingency plans to ensure the safety of affected individuals, including expedited relocation and protection measures.
- Scenario Projections:
- Best Case: Rapid implementation of security measures prevents further exploitation of the breach.
- Worst Case: Exploitation of leaked data leads to targeted attacks on refugees, damaging UK international standing.
- Most Likely: Increased scrutiny and pressure lead to policy reforms and improved data management practices.
5. Key Individuals and Entities
John Healey, Sir Gwyn Jenkins
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus