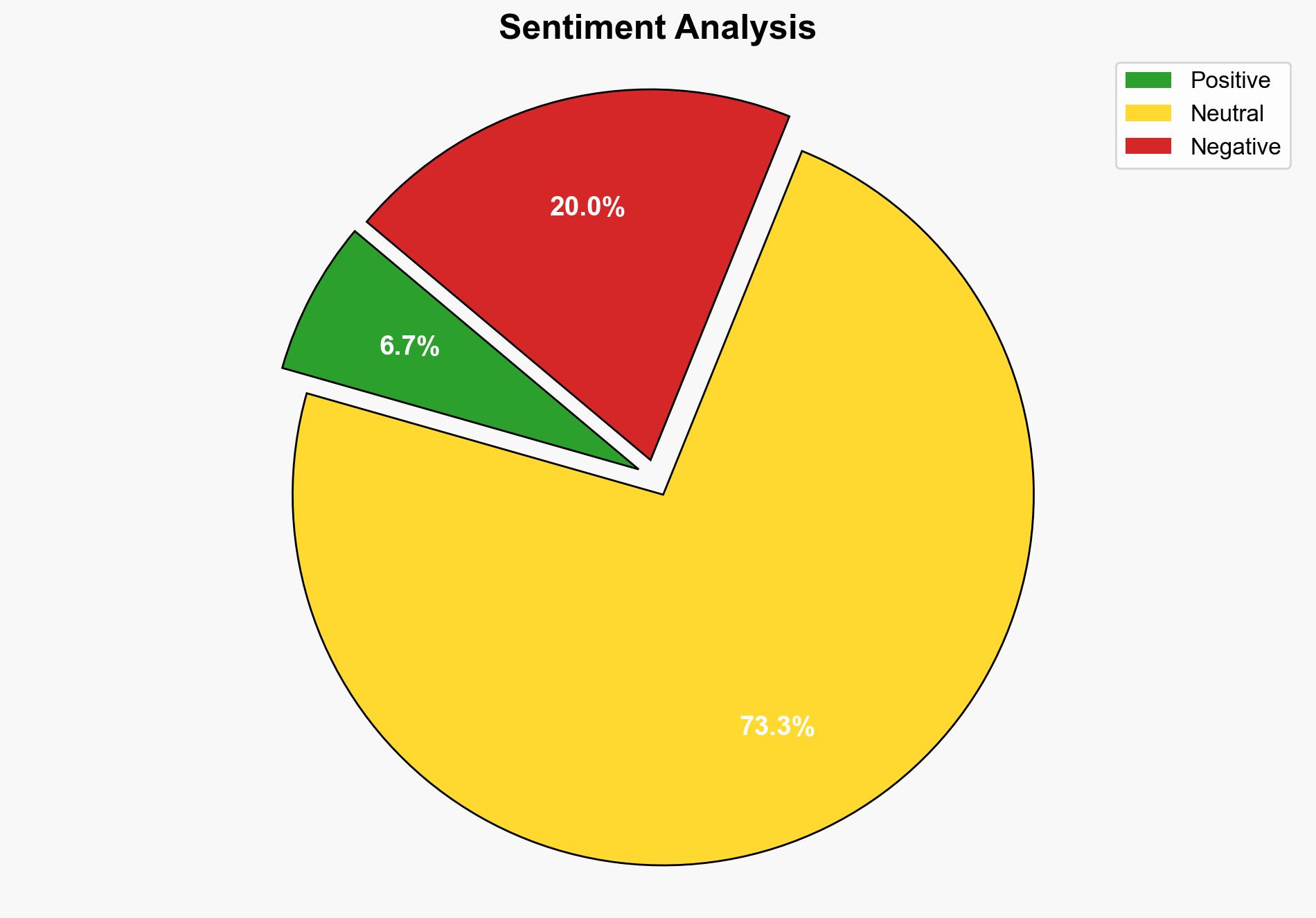
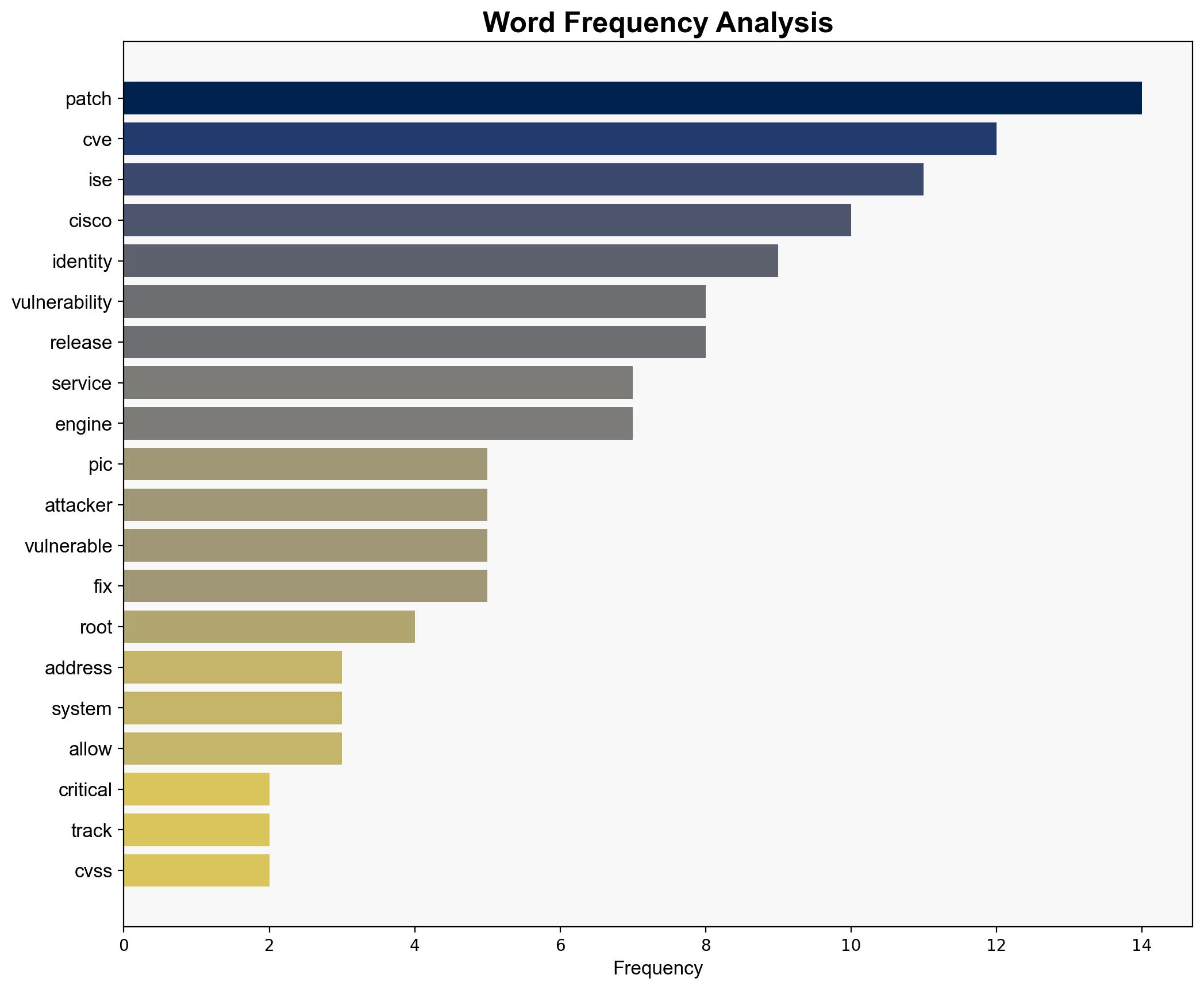
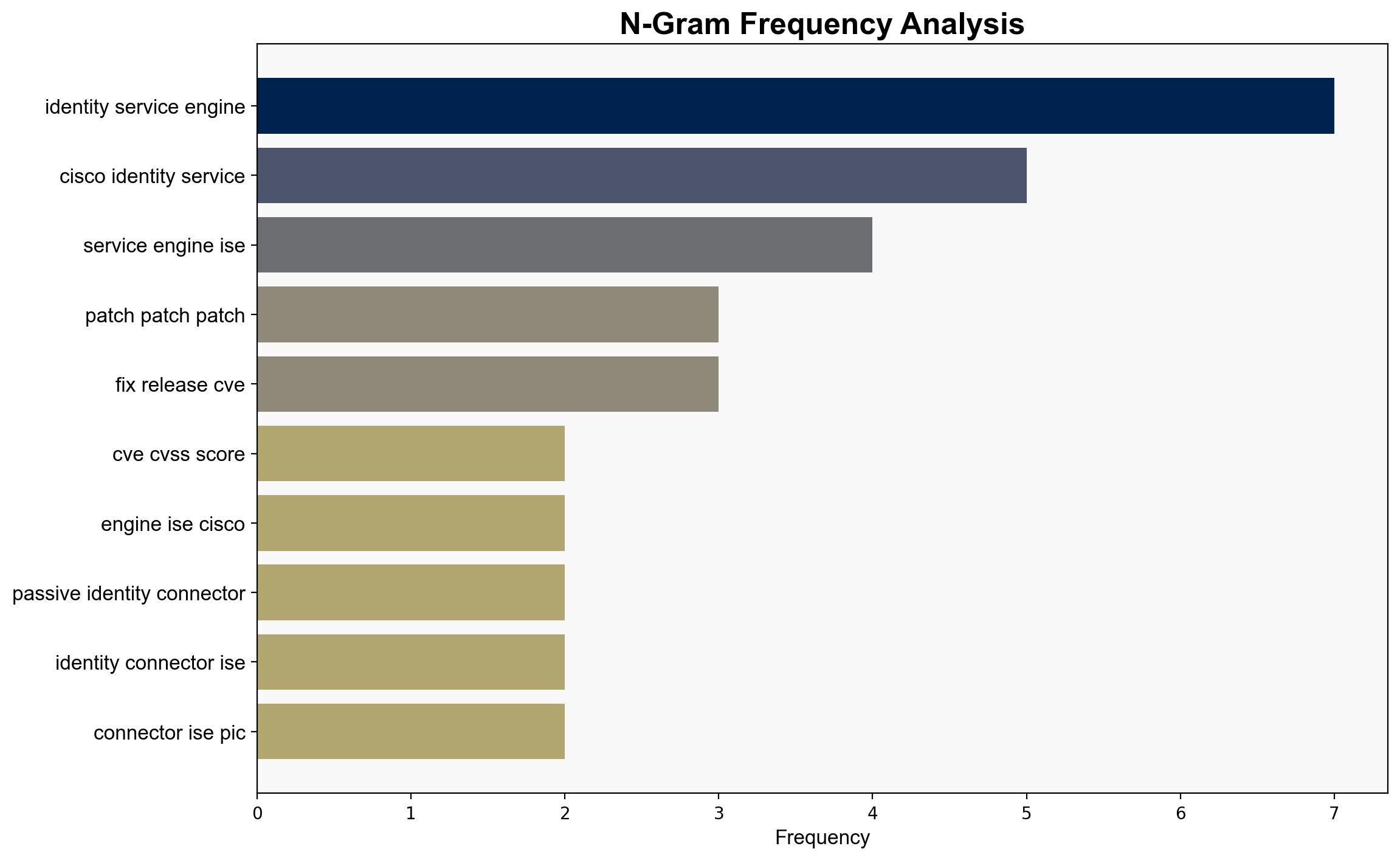
Cisco patches critical CVE-2025-20337 bug in Identity Services Engine with CVSS 10 Severity – Securityaffairs.com
Published on: 2025-07-17
Intelligence Report: Cisco Patches Critical CVE-2025-20337 Bug in Identity Services Engine with CVSS 10 Severity
1. BLUF (Bottom Line Up Front)
Cisco has addressed a critical vulnerability, CVE-2025-20337, in its Identity Services Engine (ISE), which had a CVSS score of 10, indicating the highest level of severity. The flaw allowed unauthenticated remote attackers to execute arbitrary code with root privileges. Immediate patching is recommended to mitigate potential exploitation risks.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations suggest that cyber adversaries could exploit this vulnerability to gain unauthorized access and control over affected systems, potentially leading to data breaches or system disruptions.
Indicators Development
Monitoring for unusual API requests and unauthorized system commands can help detect exploitation attempts early.
Bayesian Scenario Modeling
Probabilistic models indicate a high likelihood of exploitation attempts in the absence of timely patch application, with potential pathways leading to significant data compromise.
3. Implications and Strategic Risks
The vulnerability poses significant risks to organizations relying on Cisco ISE for network security. Exploitation could lead to unauthorized access, data theft, and operational disruptions. The widespread use of Cisco ISE amplifies the potential impact across multiple sectors, including critical infrastructure.
4. Recommendations and Outlook
- Immediately apply the available patches to all affected systems to prevent exploitation.
- Enhance monitoring of network traffic for signs of exploitation attempts.
- Scenario-based projections:
- Best Case: Rapid patch deployment mitigates risk with minimal disruption.
- Worst Case: Delayed patching leads to widespread exploitation and data breaches.
- Most Likely: Organizations that promptly patch will avoid significant impacts, while those delaying may face targeted attacks.
5. Key Individuals and Entities
Researcher: Kentaro Kawane
Organization: GMO Cybersecurity
Initiative: Trend Micro Zero Day Initiative
6. Thematic Tags
cybersecurity, vulnerability management, network security, critical infrastructure protection