Hackers are now hiding malware in DNS and using AI to reassemble it – TechSpot
Published on: 2025-07-17
Intelligence Report: Hackers are now hiding malware in DNS and using AI to reassemble it – TechSpot
1. BLUF (Bottom Line Up Front)
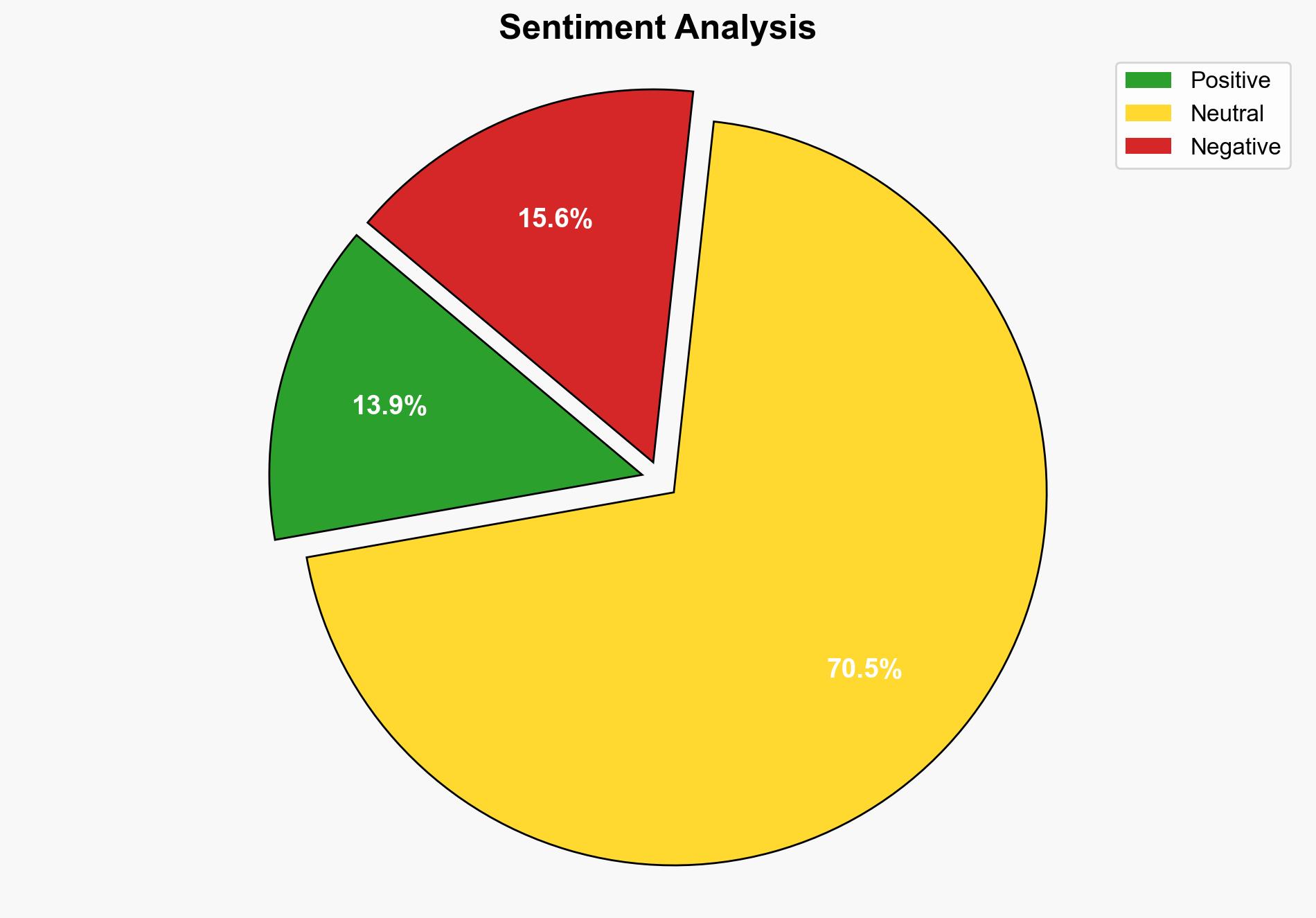
Cyber adversaries are exploiting the Domain Name System (DNS) to conceal malware, leveraging AI to reassemble it, thereby bypassing advanced security measures. This technique poses a significant threat to cybersecurity infrastructure, necessitating enhanced monitoring and defensive strategies. Immediate action is recommended to strengthen DNS security protocols and develop AI-based detection systems.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
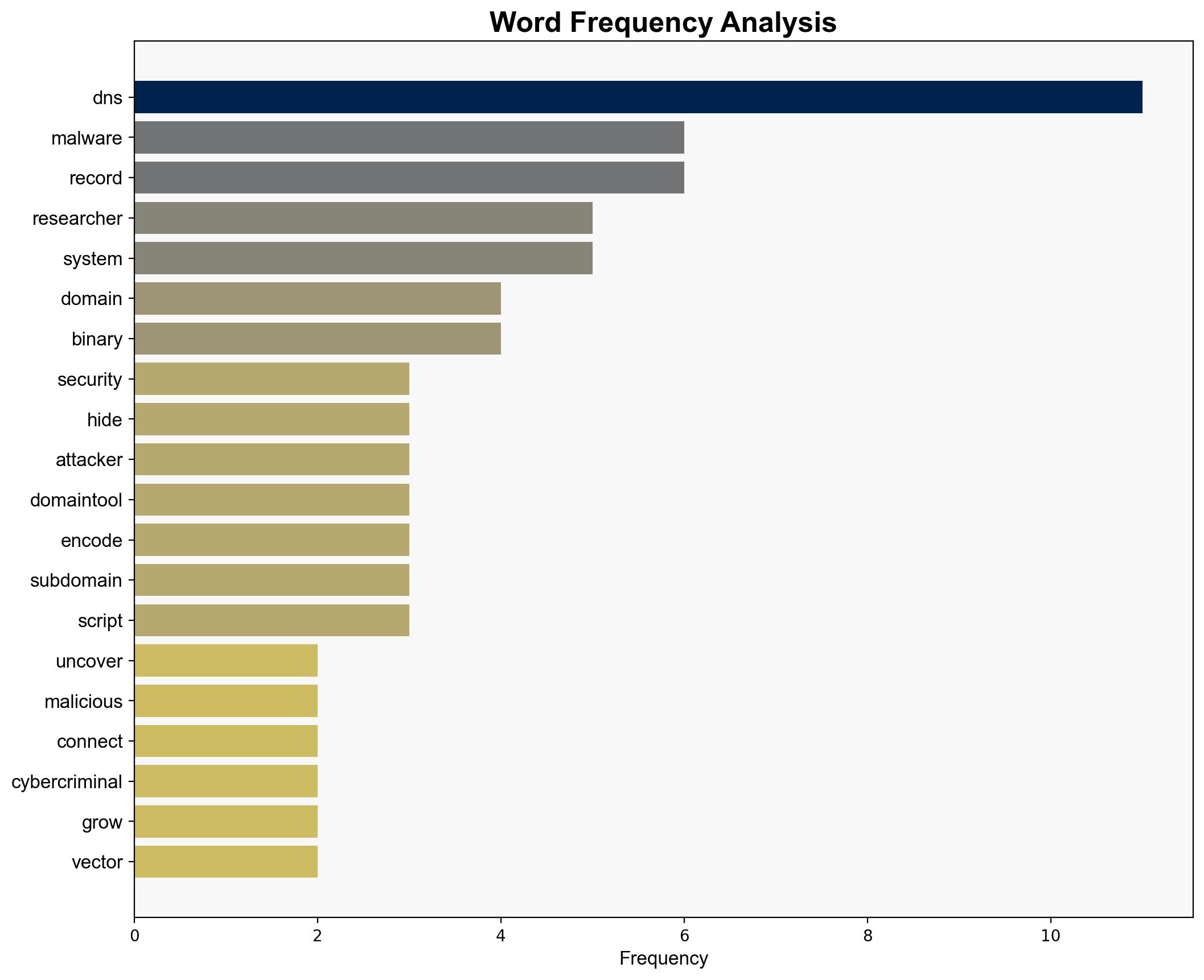
Simulations indicate that attackers can effectively embed malware within DNS records, evading detection by traditional security tools.
Indicators Development
Key indicators include anomalous DNS traffic patterns and the presence of non-standard data in DNS records.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of increased DNS-based attacks, with potential for rapid evolution in tactics.
Network Influence Mapping
Mapping reveals potential collaboration between state-sponsored actors and cybercriminals in exploiting DNS vulnerabilities.
3. Implications and Strategic Risks
The use of DNS as a malware distribution vector introduces systemic vulnerabilities that could impact critical infrastructure. The integration of AI in reassembling malware fragments increases the sophistication of attacks, potentially leading to widespread disruptions. This trend underscores the need for cross-domain collaboration to address emerging cybersecurity threats.
4. Recommendations and Outlook
- Enhance DNS security protocols by implementing advanced monitoring and anomaly detection systems.
- Invest in AI-driven cybersecurity tools to detect and counteract AI-based malware assembly.
- Develop international cooperation frameworks to share intelligence and best practices in combating DNS-based threats.
- Scenario-based projections:
- Best case: Rapid adaptation of security measures mitigates the threat.
- Worst case: Widespread exploitation leads to significant infrastructure disruptions.
- Most likely: Gradual increase in DNS-based attacks with moderate impact.
5. Key Individuals and Entities
Ian Campbell (Domaintool Engineer)
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus