My focus was on saving lives after Afghan data breach Shapps says – BBC News
Published on: 2025-07-18
Intelligence Report: My focus was on saving lives after Afghan data breach Shapps says – BBC News
1. BLUF (Bottom Line Up Front)
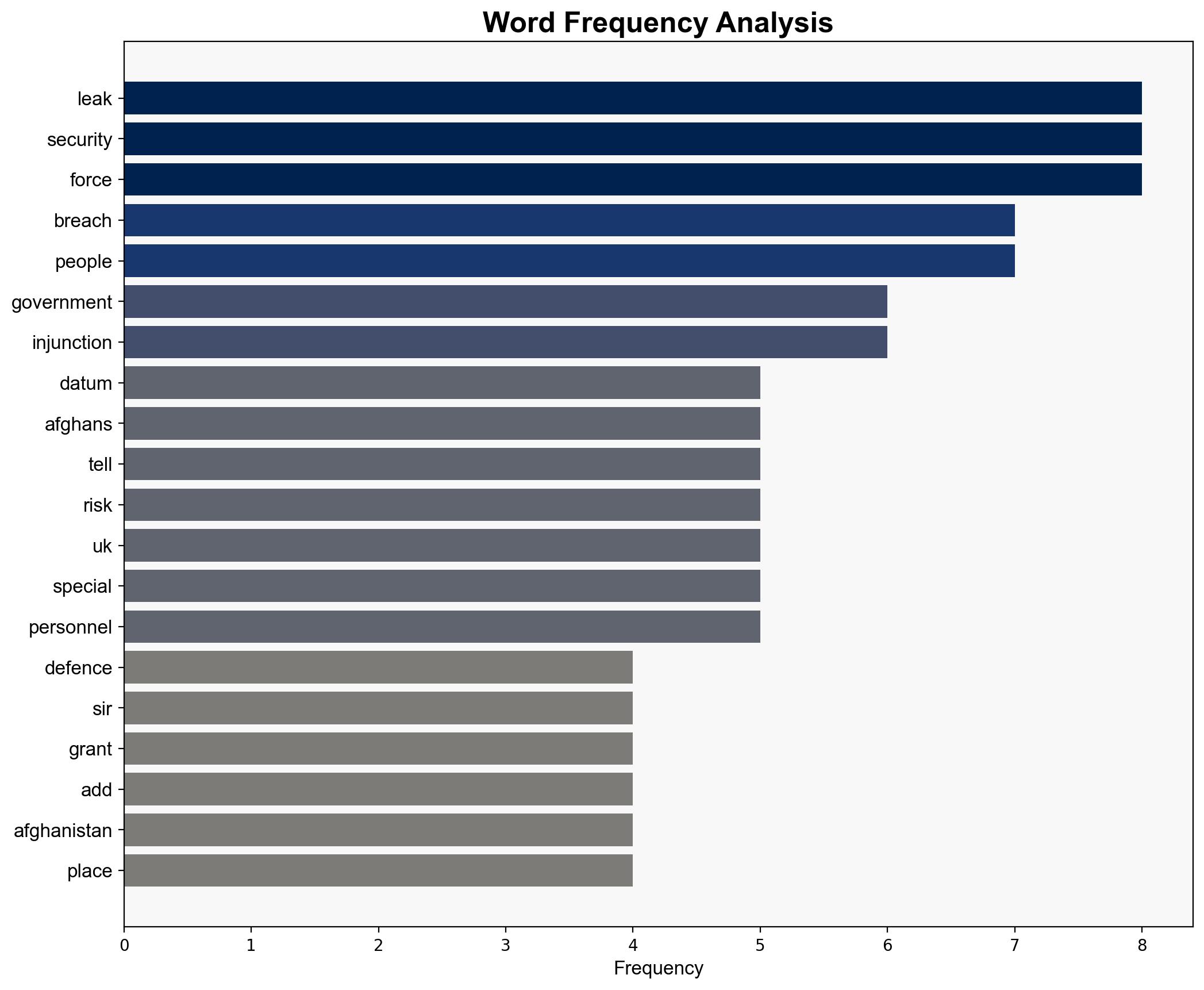
The recent Afghan data breach has posed significant risks to individuals associated with the British government, particularly those who worked with the UK during the Afghanistan conflict. The breach, involving sensitive personal data, has heightened the threat of retribution from the Taliban. Immediate actions were taken to mitigate potential harm, including legal measures to restrict information dissemination. The focus remains on safeguarding lives and managing the fallout effectively.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
ACH 2.0
Analyzed the intentions behind the data breach, concluding that the primary threat actors likely aimed to exploit the data for targeting individuals associated with Western forces.
Indicators Development
Monitored online activities and communications for signs of radicalization or operational planning, noting increased discussions related to the breach.
Narrative Pattern Analysis
Examined the dissemination of narratives around the breach, identifying potential recruitment and incitement efforts by hostile entities.
3. Implications and Strategic Risks
The breach exposes systemic vulnerabilities in data handling and protection, with potential cascading effects on international relations and security. The risk of targeted violence against individuals named in the breach is significant, necessitating heightened security measures. Additionally, the incident may embolden adversaries to exploit similar vulnerabilities in the future.
4. Recommendations and Outlook
- Enhance data protection protocols and conduct comprehensive security audits to prevent future breaches.
- Implement immediate protective measures for individuals identified in the breach, including relocation and increased security.
- Develop scenario-based plans to address potential escalations, with a focus on worst-case outcomes involving targeted attacks.
5. Key Individuals and Entities
Grant Shapps, John Healey
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus