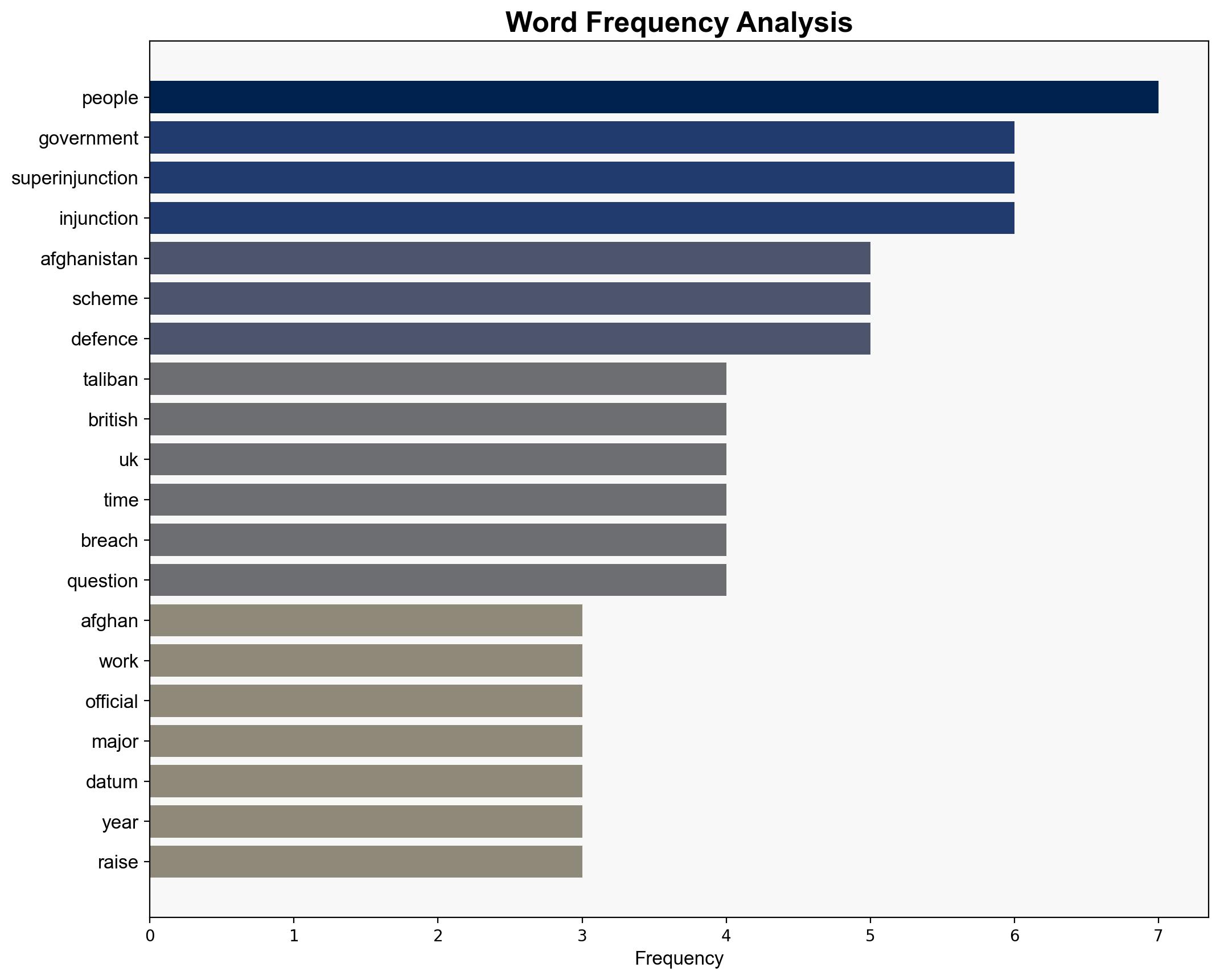
Afghan data breach Why UK sought to keep it a secret – RTE
Published on: 2025-07-19
Intelligence Report: Afghan Data Breach and UK Secrecy – RTE
1. BLUF (Bottom Line Up Front)
The Afghan data breach involving the ARAP scheme posed significant risks to individuals associated with international forces, leading the UK to seek a superinjunction to prevent public disclosure. The breach highlighted vulnerabilities in data handling and raised questions about government transparency and accountability. Recommendations include enhancing data security protocols and conducting a comprehensive review of information protection measures.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
ACH 2.0
Analyzed potential motivations behind the data breach and the UK’s decision to seek a superinjunction. The primary intention was to protect individuals at risk of retribution from the Taliban.
Indicators Development
Monitored online activities and communications that could indicate further breaches or exploitation of compromised data by hostile entities.
Narrative Pattern Analysis
Examined how the breach and subsequent secrecy were portrayed in media and political narratives, assessing impacts on public perception and policy debates.
3. Implications and Strategic Risks
The breach underscores systemic vulnerabilities in data management and the potential for exploitation by adversaries. It poses risks to individuals’ safety and could erode trust in government transparency. The incident may also influence future policy on data protection and international cooperation.
4. Recommendations and Outlook
- Enhance cybersecurity measures and data protection protocols to prevent future breaches.
- Conduct an independent review of the ARAP scheme and related data handling practices.
- Scenario Projections:
- Best Case: Improved data security and restored public trust through transparency and accountability measures.
- Worst Case: Continued data breaches leading to increased threats to individuals and diplomatic tensions.
- Most Likely: Incremental improvements in data security with ongoing scrutiny of government actions.
5. Key Individuals and Entities
Kemi Badenoch, Ed Davey, Keir Starmer, Ben Wallace, John Healey
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus