Instrumenting Nextjs with runtime secret injection – Phase.dev
Published on: 2025-07-27
Intelligence Report: Instrumenting Nextjs with Runtime Secret Injection – Phase.dev
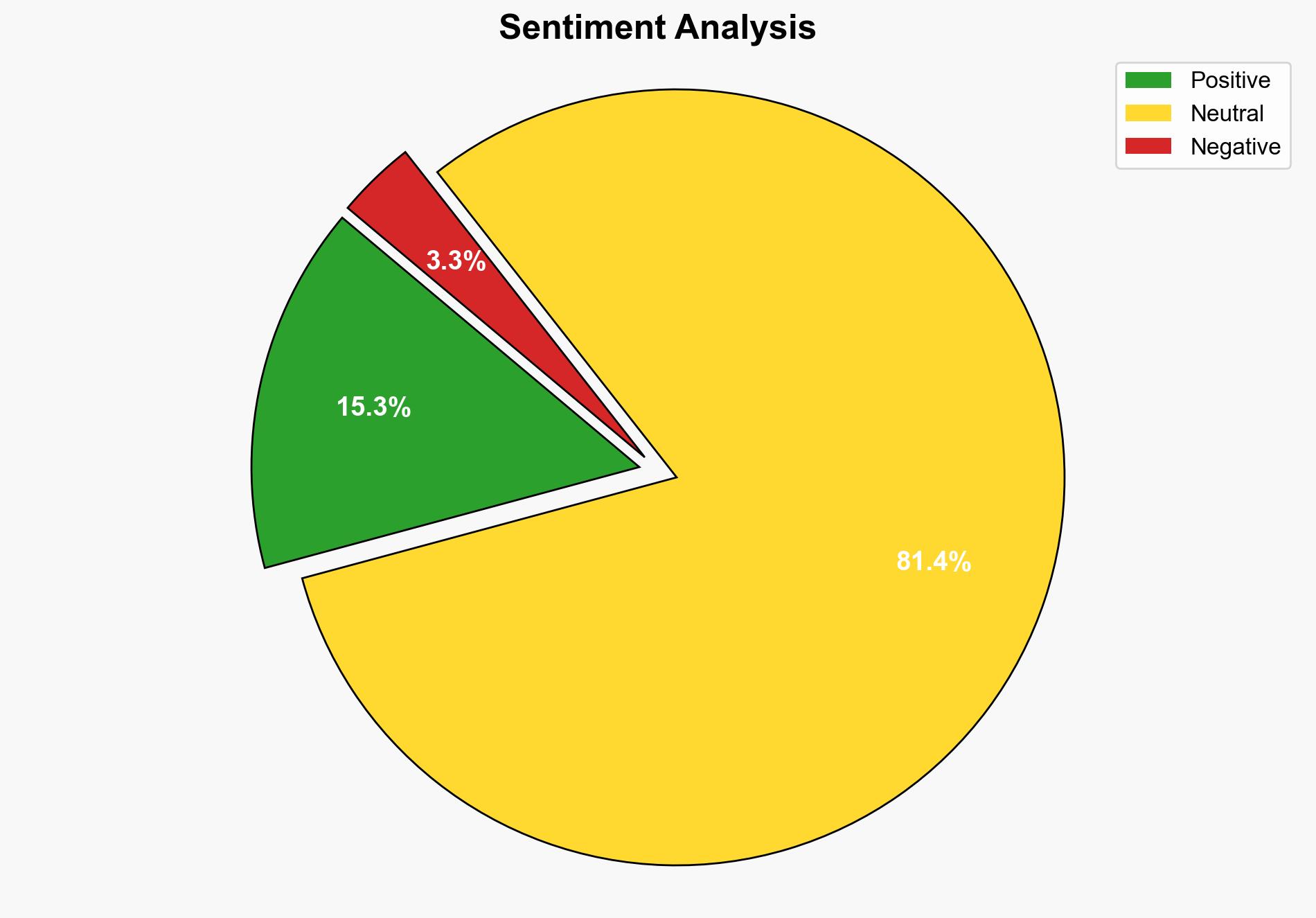
1. BLUF (Bottom Line Up Front)
The analysis suggests that the introduction of runtime secret injection in Next.js applications via instrumentation files is a strategic move to enhance security and scalability. The most supported hypothesis is that this method is primarily aimed at improving secret management in development environments, with a moderate confidence level. It is recommended to adopt this approach while ensuring comprehensive security audits and training for developers.
2. Competing Hypotheses
Hypothesis 1: The primary goal of runtime secret injection is to improve security by preventing secrets from being stored in code repositories or build artifacts, thus reducing the risk of exposure.
Hypothesis 2: The main objective is to enhance the portability and ease of distribution of applications by decoupling secret management from the application codebase, facilitating collaboration and deployment across teams.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis 1 is better supported due to the explicit mention of security concerns and the drawbacks of traditional secret management methods like environment files. The focus on security risks and the benefits of runtime injection align more closely with this hypothesis.
3. Key Assumptions and Red Flags
Assumptions:
– Runtime secret injection inherently provides better security than traditional methods.
– Developers will correctly implement and manage the new system without introducing new vulnerabilities.
Red Flags:
– Lack of detailed information on how the new system handles potential runtime vulnerabilities.
– Possible over-reliance on the assumption that runtime injection alone can mitigate all security risks.
4. Implications and Strategic Risks
The shift to runtime secret injection could significantly reduce the risk of secret leaks, but it also introduces new challenges in terms of runtime security and potential performance impacts. If not properly managed, this could lead to new vulnerabilities. The economic implications include potential cost savings from reduced security breaches and more efficient development processes. However, there is a risk of increased complexity in managing runtime environments.
5. Recommendations and Outlook
- Conduct thorough security audits to identify and mitigate any new vulnerabilities introduced by runtime secret injection.
- Provide training for developers to ensure proper implementation and management of the new system.
- Best Case: Improved security and collaboration lead to widespread adoption and reduced incidents of data breaches.
- Worst Case: Mismanagement of the new system results in new vulnerabilities and potential data leaks.
- Most Likely: Gradual adoption with initial challenges in implementation, leading to eventual improvements in security and efficiency.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. The focus is on the Next.js development community and organizations using this framework.
7. Thematic Tags
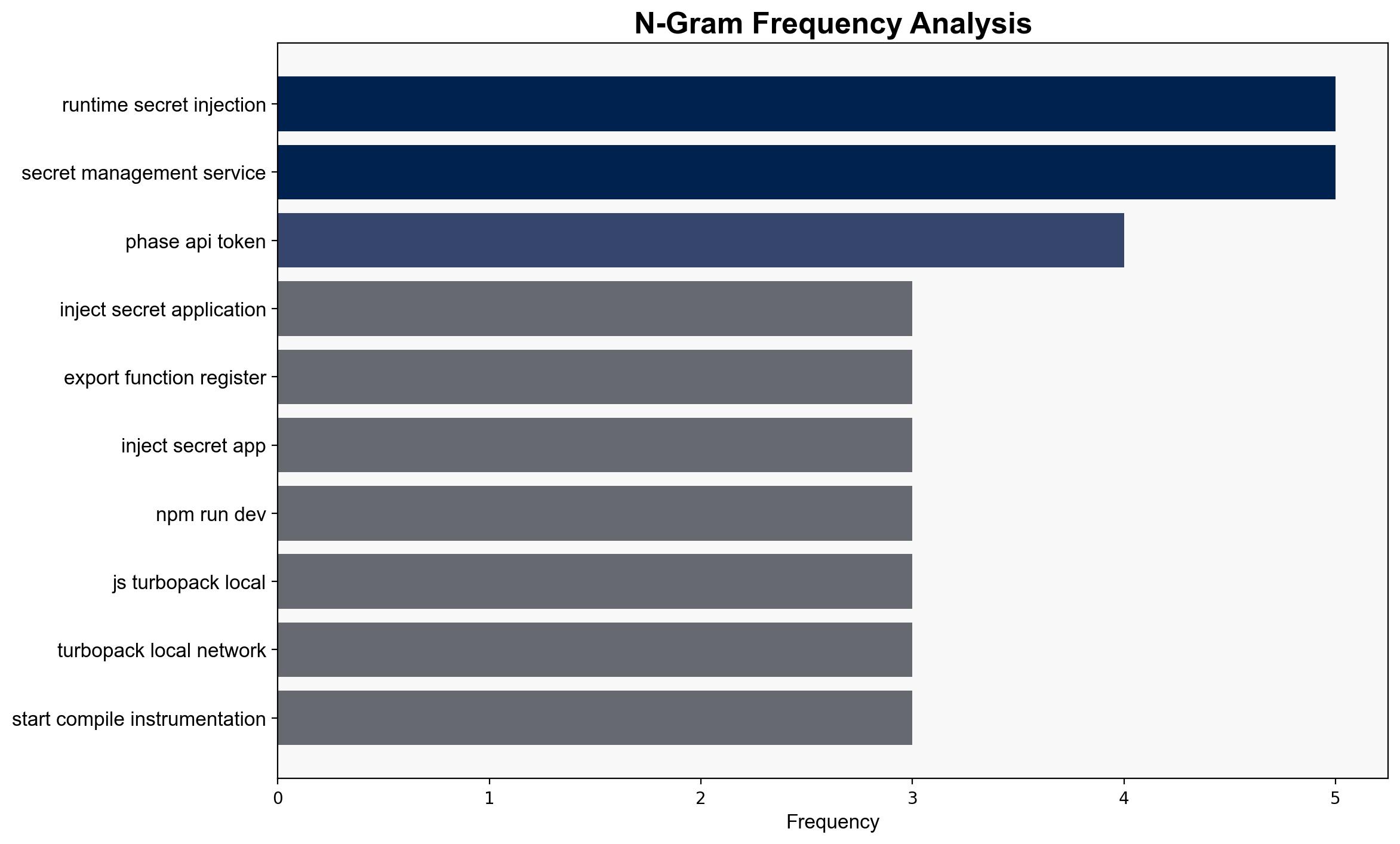
cybersecurity, software development, secret management, runtime security