Amazon’s AI coding assistant exposed nearly 1 million users to potential system wipe – TechSpot
Published on: 2025-07-27
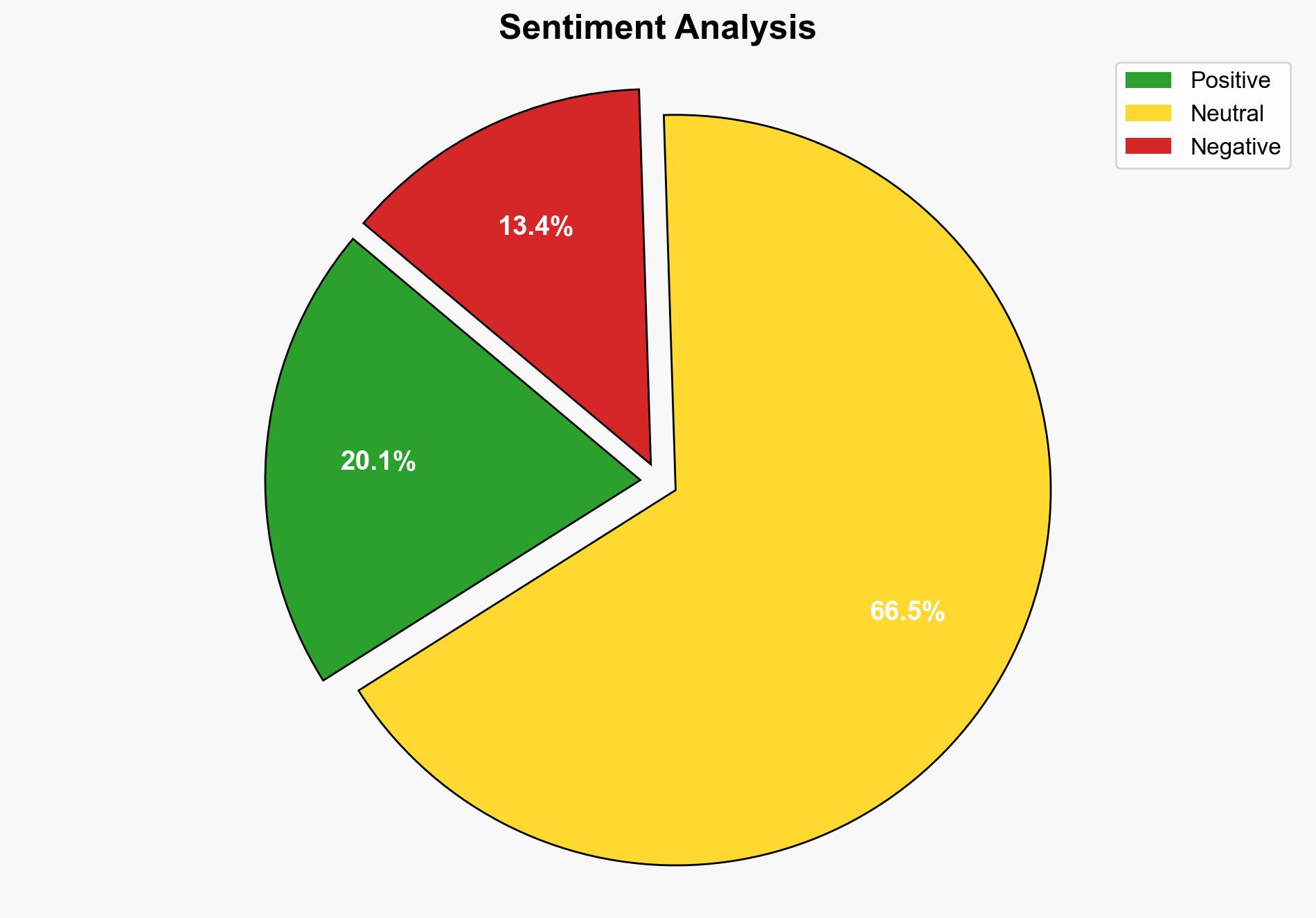
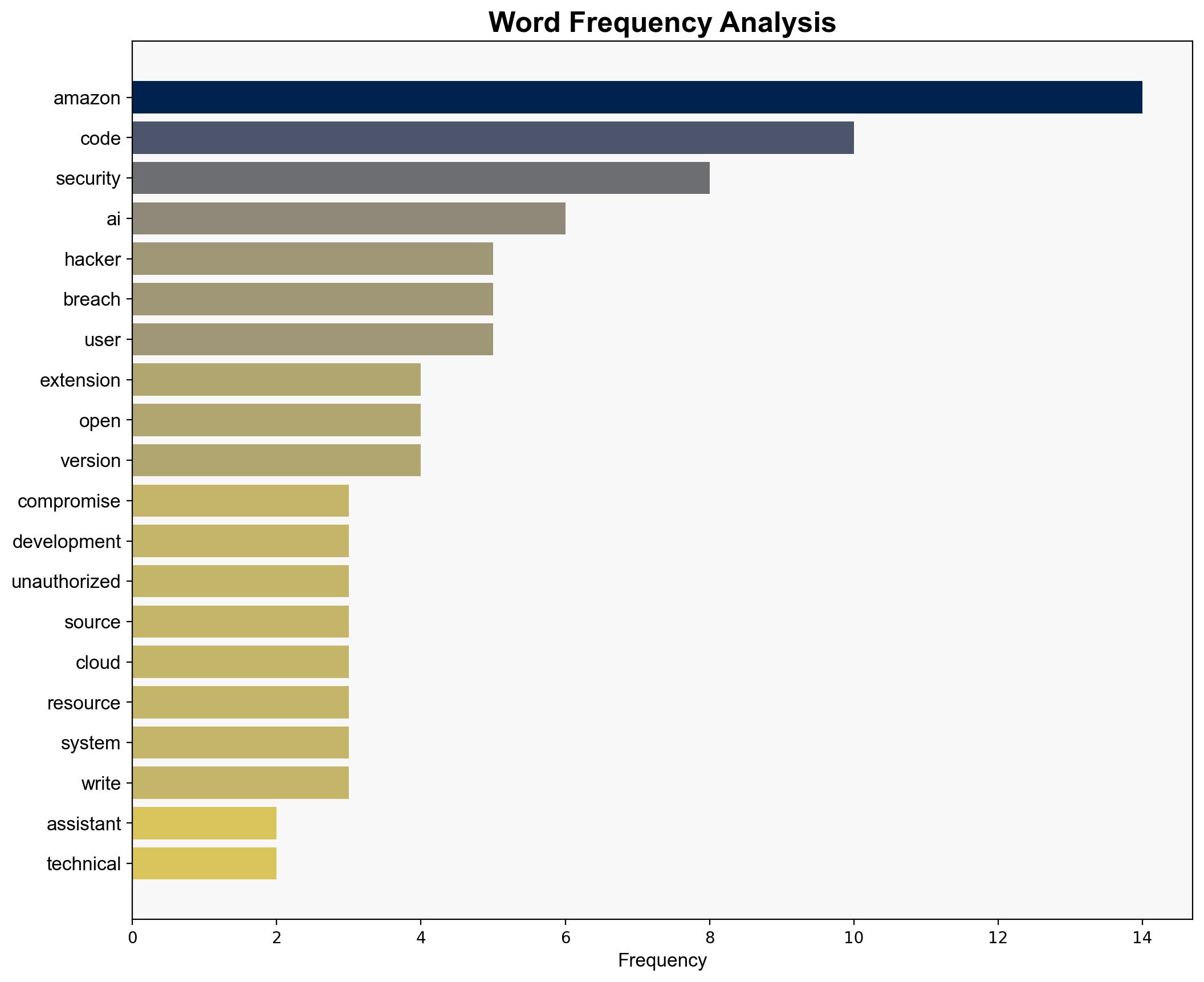
Intelligence Report: Amazon’s AI coding assistant exposed nearly 1 million users to potential system wipe – TechSpot
1. BLUF (Bottom Line Up Front)
The breach of Amazon’s AI coding assistant highlights significant vulnerabilities in integrating AI tools into software development pipelines. The most supported hypothesis suggests a deliberate demonstration of security weaknesses by the hackers. Confidence level: Moderate. Recommended action: Amazon should enhance its security protocols, particularly in code review and access control, to prevent future breaches.
2. Competing Hypotheses
1. **Deliberate Security Demonstration Hypothesis**: Hackers intentionally exposed the vulnerability to highlight Amazon’s inadequate security measures, as suggested by their public statements and the nature of the breach.
2. **Unintentional Oversight Hypothesis**: The breach resulted from a failure in Amazon’s security protocols and verification processes, allowing unauthorized code to be integrated without malicious intent from the hackers.
Using ACH 2.0, the deliberate demonstration hypothesis is better supported due to the hackers’ public mocking and characterization of Amazon’s security as “security theater,” implying intent to expose weaknesses rather than cause direct harm.
3. Key Assumptions and Red Flags
– **Assumptions**: The deliberate hypothesis assumes hackers had no intent to cause lasting damage, while the oversight hypothesis assumes Amazon’s security protocols are generally robust but failed in this instance.
– **Red Flags**: The initial failure to detect the breach and the delay in public acknowledgment suggest potential gaps in Amazon’s incident response and transparency practices.
– **Blind Spots**: Lack of detailed information on the hackers’ identities and motivations could skew analysis.
4. Implications and Strategic Risks
The breach underscores the risk of integrating AI tools without robust security measures, potentially leading to widespread system vulnerabilities. If not addressed, similar incidents could erode trust in AI-driven development tools and damage Amazon’s reputation. Economically, this could impact Amazon’s market position and customer base. Psychologically, it may increase developer skepticism towards AI integration.
5. Recommendations and Outlook
- **Immediate Action**: Strengthen code review processes and access controls to prevent unauthorized code integration.
- **Mid-term Strategy**: Conduct a comprehensive security audit of AI tools and workflows to identify and mitigate vulnerabilities.
- **Long-term Outlook**: Develop a robust incident response plan and improve transparency to maintain stakeholder trust.
- **Scenario Projections**:
– **Best Case**: Enhanced security measures prevent future breaches, restoring confidence in Amazon’s AI tools.
– **Worst Case**: Continued vulnerabilities lead to further breaches, causing significant reputational and financial damage.
– **Most Likely**: Incremental improvements in security reduce risk but do not eliminate it entirely.
6. Key Individuals and Entities
– Corey Quinn, who criticized Amazon’s response.
– The unnamed hacker(s) who exposed the vulnerability.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus