Dimitri John Ledkov Achieving actually full disk encryption of UEFI ESP at rest with TCG OPAL FIPS LUKS – Surgut.co.uk
Published on: 2025-07-28
Intelligence Report: Dimitri John Ledkov Achieving actually full disk encryption of UEFI ESP at rest with TCG OPAL FIPS LUKS – Surgut.co.uk
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that the integration of TCG OPAL and FIPS LUKS for full disk encryption, including UEFI ESP, represents a significant advancement in cybersecurity standards for both physical and virtual environments. Confidence Level: High. Recommended action is to promote the adoption of these standards across industries to enhance data protection and compliance with security regulations.
2. Competing Hypotheses
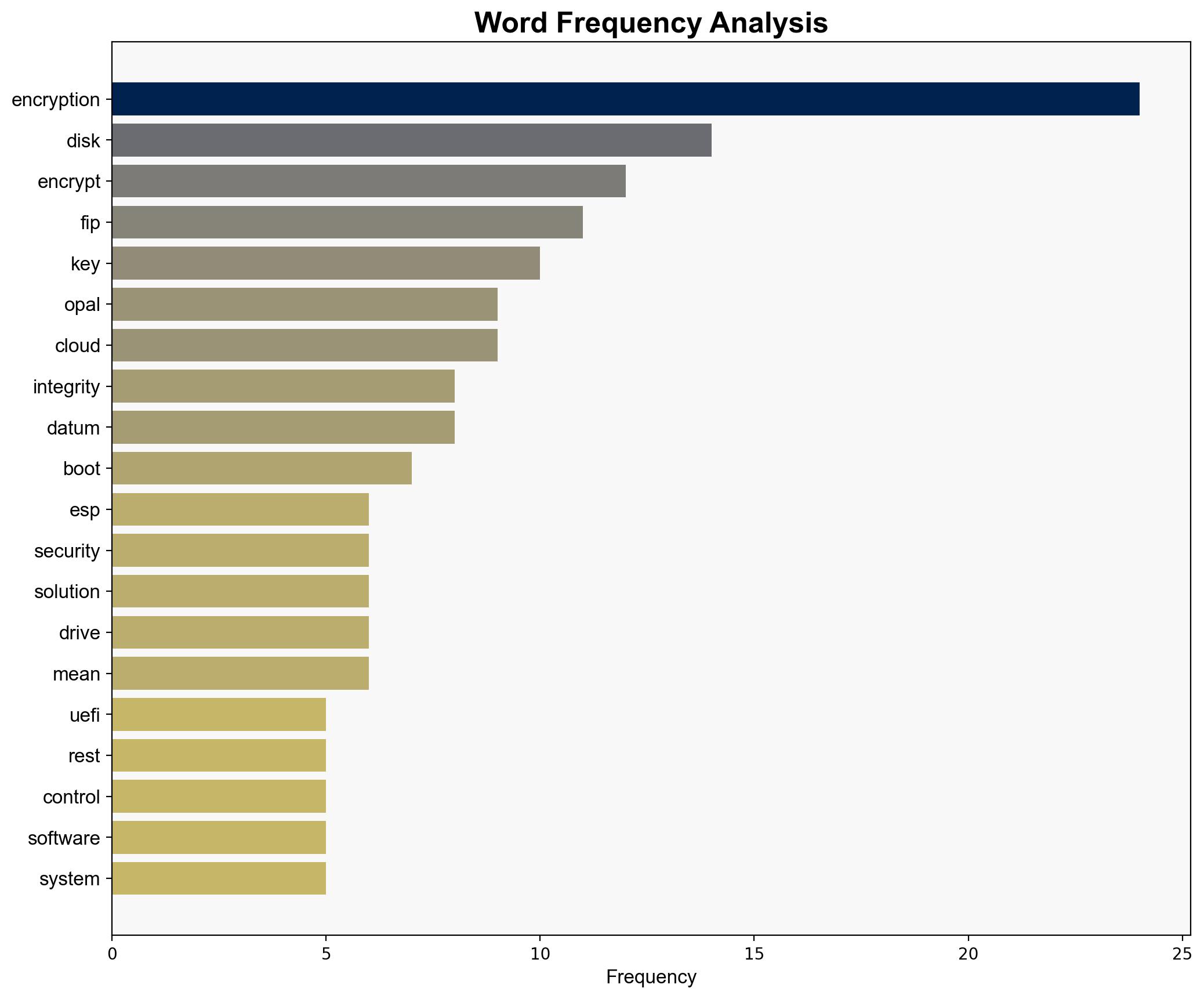
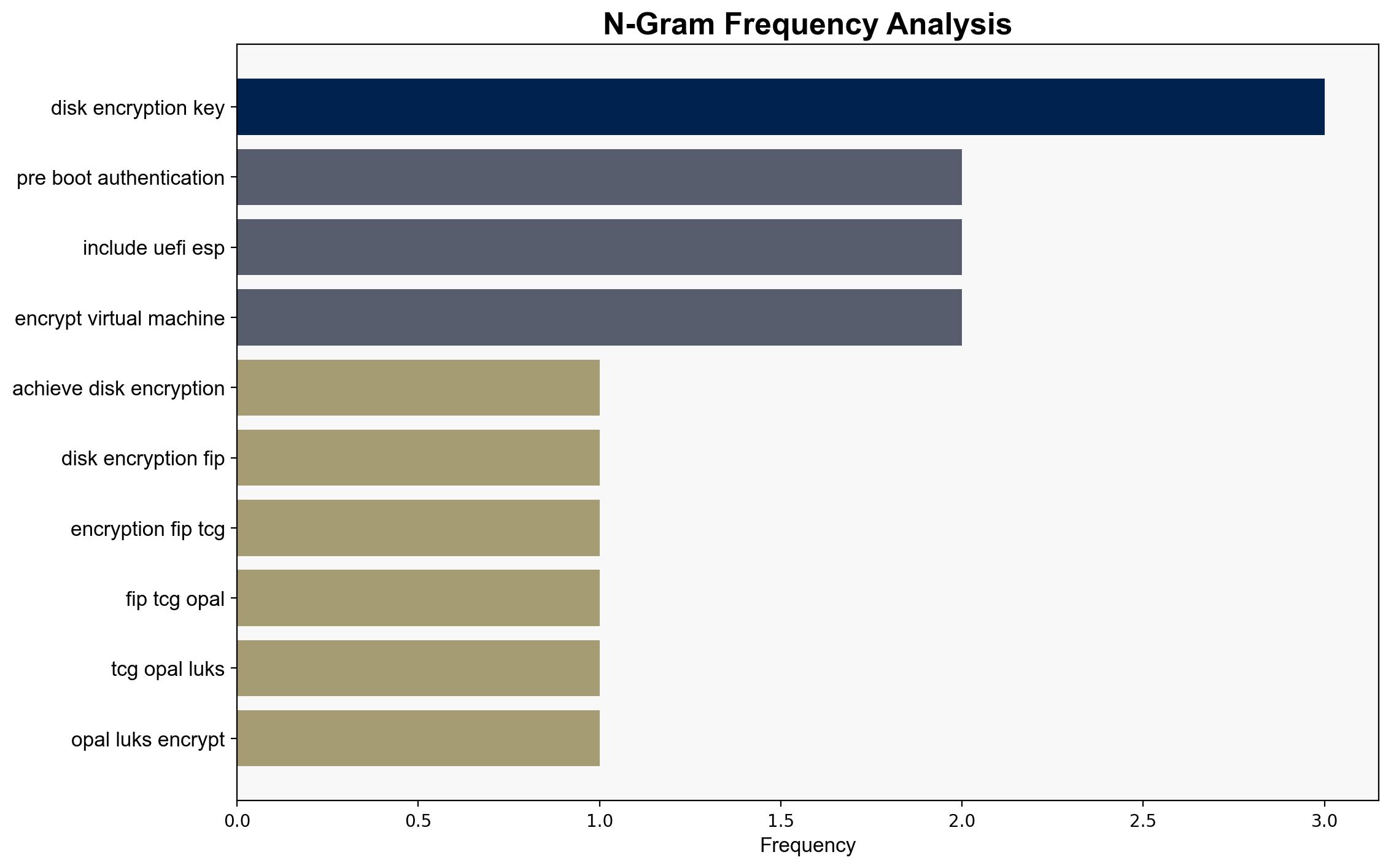
1. The integration of TCG OPAL and FIPS LUKS encryption methods provides a comprehensive solution for full disk encryption, enhancing security for both physical devices and virtual machines.
2. The implementation of these encryption standards may face significant challenges in adoption due to technical complexities and potential compatibility issues with existing systems.
3. Key Assumptions and Red Flags
– Assumptions: It is assumed that the encryption standards are universally applicable and that hardware manufacturers will continue to support these specifications.
– Red Flags: Potential over-reliance on hardware compatibility and the assumption that all cloud providers will offer FIPS-certified encryption solutions could be misleading.
– Missing Data: Specific data on the adoption rate of these standards across different sectors is not provided.
4. Implications and Strategic Risks
The adoption of these encryption standards could significantly reduce the risk of data breaches and enhance compliance with international security standards. However, failure to address compatibility issues could lead to fragmented security implementations, increasing the risk of vulnerabilities. Additionally, reliance on specific hardware vendors may pose supply chain risks.
5. Recommendations and Outlook
- Encourage cross-industry collaboration to address compatibility and implementation challenges.
- Develop training programs to ensure IT professionals are equipped to implement these standards effectively.
- Best Case Scenario: Widespread adoption leads to a significant reduction in data breaches and enhanced global cybersecurity posture.
- Worst Case Scenario: Technical and compatibility issues hinder adoption, leading to inconsistent security measures and increased vulnerability.
- Most Likely Scenario: Gradual adoption with ongoing adjustments to address emerging challenges and compatibility issues.
6. Key Individuals and Entities
Dimitri John Ledkov, Samsung, Western Digital, Seagate Technology, Dell, Google, Lenovo, IBM, Kioxia.
7. Thematic Tags
national security threats, cybersecurity, data protection, encryption standards