Why CISOs should rethink identity risk through attack paths – Help Net Security
Published on: 2025-07-30
Intelligence Report: Why CISOs should rethink identity risk through attack paths – Help Net Security
1. BLUF (Bottom Line Up Front)
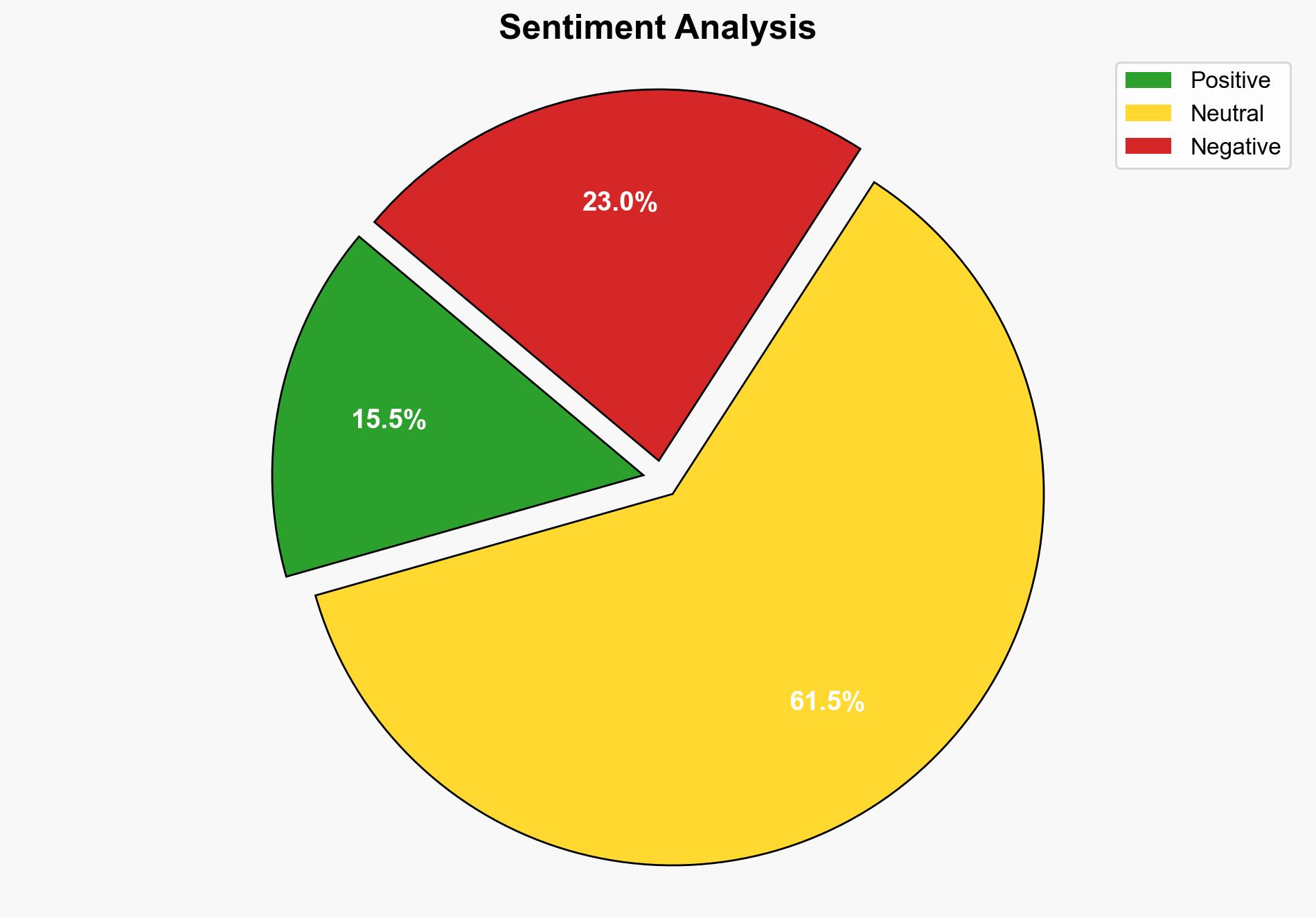
The analysis suggests a high confidence level in the hypothesis that traditional identity governance tools are insufficient to manage the evolving identity risk landscape, particularly due to the exponential growth of non-human identities and session-based attacks. The recommended action is to integrate attack path management (APM) strategies to enhance visibility and control over identity risks.
2. Competing Hypotheses
Hypothesis 1: Traditional identity governance tools like PAM and MFA are inadequate for managing modern identity risks, necessitating a shift towards attack path management strategies.
Hypothesis 2: The current identity governance tools, when properly configured and combined with enhanced monitoring, can still effectively manage identity risks without the need for new strategies.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis 1 is better supported. The evidence of increasing identity sprawl and the inadequacy of existing tools to address session-based threats aligns more closely with the need for APM strategies.
3. Key Assumptions and Red Flags
Assumptions:
– Identity risks are primarily driven by the growth of non-human identities and session-based threats.
– Attackers are increasingly exploiting session tokens and cookies, bypassing traditional authentication measures.
Red Flags:
– Lack of empirical data on the effectiveness of APM strategies compared to traditional tools.
– Potential bias towards promoting new security solutions without comprehensive evaluation.
4. Implications and Strategic Risks
The shift towards APM strategies implies a significant change in cybersecurity practices, potentially leading to increased costs and complexity. Failure to adapt could result in heightened vulnerability to identity-based attacks, impacting organizational security and operational continuity. The economic impact includes potential data breaches and associated costs, while geopolitical risks involve state-sponsored cyber activities exploiting identity vulnerabilities.
5. Recommendations and Outlook
- Integrate APM strategies with existing identity governance frameworks to enhance visibility and control over identity risks.
- Conduct regular audits and simulations to test the effectiveness of identity management strategies.
- Scenario Projections:
- Best Case: Successful integration of APM leads to reduced identity-based threats and improved security posture.
- Worst Case: Failure to adapt results in significant breaches and operational disruptions.
- Most Likely: Gradual improvement in identity risk management as organizations adopt APM strategies.
6. Key Individuals and Entities
The report does not mention specific individuals by name. Key entities include organizations deploying identity governance tools and those developing APM solutions.
7. Thematic Tags
national security threats, cybersecurity, identity management, attack path management, non-human identities