IR Trends Q2 2025 Phishing attacks persist as actors leverage compromised valid accounts to enhance legitimacy – Talosintelligence.com
Published on: 2025-07-31
Intelligence Report: IR Trends Q2 2025 Phishing Attacks Persist as Actors Leverage Compromised Valid Accounts to Enhance Legitimacy – Talosintelligence.com
1. BLUF (Bottom Line Up Front)
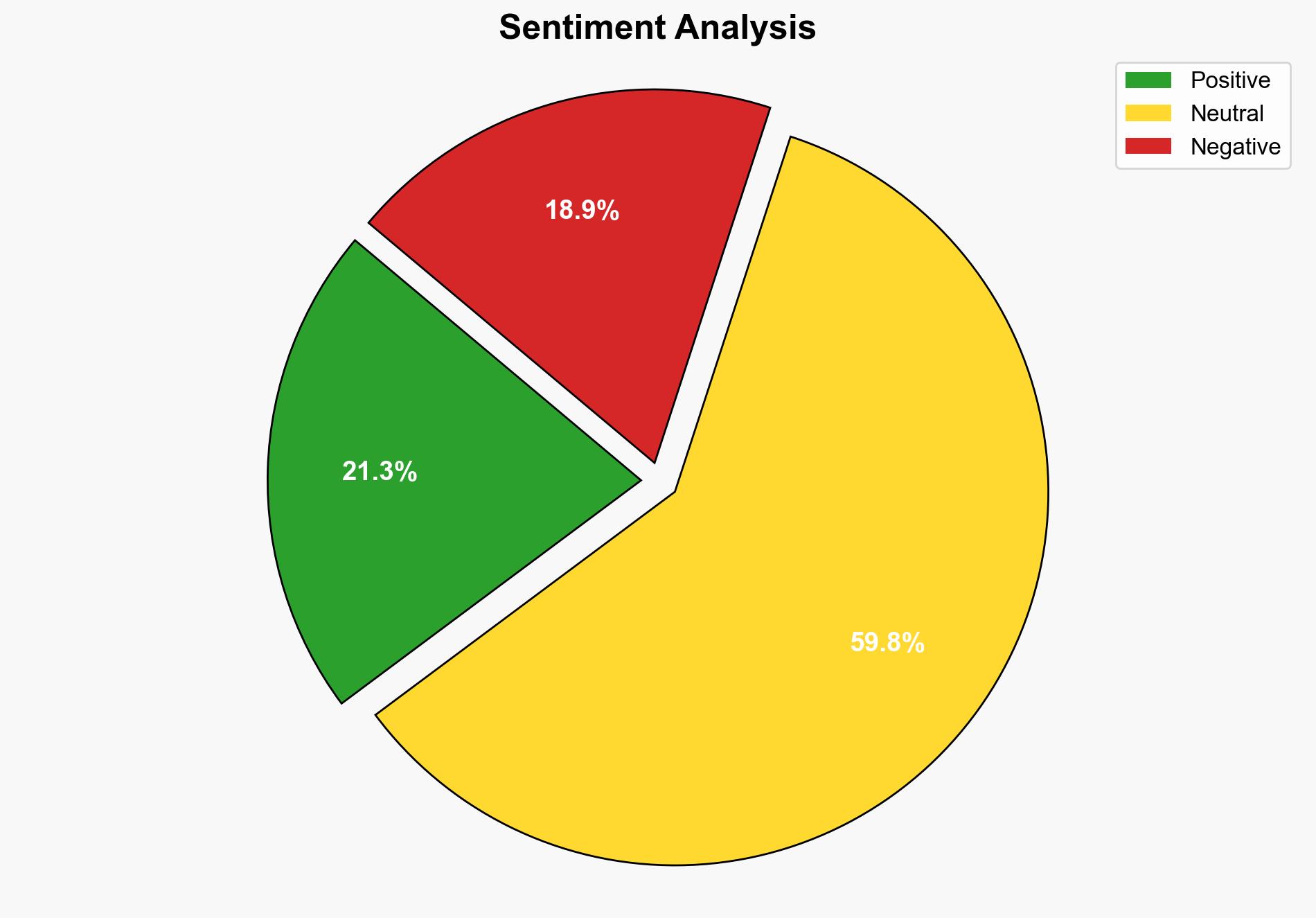
Phishing attacks continue to evolve, with actors increasingly using compromised valid accounts to enhance the legitimacy of their operations. The most supported hypothesis is that these actors are adapting to enhanced security measures by exploiting trusted accounts, increasing the difficulty of detection. Confidence level: Moderate. Recommended action: Strengthen multi-factor authentication and enhance monitoring of account activity to detect anomalies.
2. Competing Hypotheses
1. **Hypothesis A**: Cyber actors are leveraging compromised valid accounts primarily to bypass enhanced security measures and increase the success rate of phishing attacks.
2. **Hypothesis B**: The use of compromised valid accounts is a diversion tactic, aiming to distract cybersecurity efforts while preparing for larger-scale attacks.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the observed increase in phishing success rates and the sophistication of attacks using legitimate credentials. Hypothesis B lacks direct evidence and relies on speculative future intentions.
3. Key Assumptions and Red Flags
– **Assumptions**:
– Valid accounts are more trusted and less likely to trigger security alerts.
– Cyber actors have the capability to continuously compromise new accounts.
– **Red Flags**:
– Lack of specific data on the origin of compromised accounts.
– Potential cognitive bias towards overestimating the sophistication of attackers.
– Inconsistent reporting on the scale and impact of these attacks.
4. Implications and Strategic Risks
The persistence of phishing attacks using compromised accounts poses significant risks to organizational cybersecurity. This trend could lead to increased financial losses, reputational damage, and potential breaches of sensitive information. The economic impact may extend to increased costs for cybersecurity measures. Geopolitically, state-sponsored actors could exploit these tactics for espionage or disruption.
5. Recommendations and Outlook
- Enhance multi-factor authentication and implement behavioral analytics to detect anomalies in account usage.
- Conduct regular security training to increase awareness of phishing tactics among employees.
- Scenario-based projections:
- Best Case: Improved detection and response capabilities significantly reduce the success rate of phishing attacks.
- Worst Case: A major breach occurs, leading to widespread data compromise and financial losses.
- Most Likely: Continued adaptation by cyber actors, with incremental improvements in security measures.
6. Key Individuals and Entities
No specific individuals are mentioned in the source intelligence. Entities involved include cybersecurity firms and potentially affected organizations.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus