Victims of Afghan data leak receive scam emails offering tens of thousands in compensation Sky News can reveal – Sky.com
Published on: 2025-07-31
Intelligence Report: Victims of Afghan data leak receive scam emails offering tens of thousands in compensation Sky News can reveal – Sky.com
1. BLUF (Bottom Line Up Front)
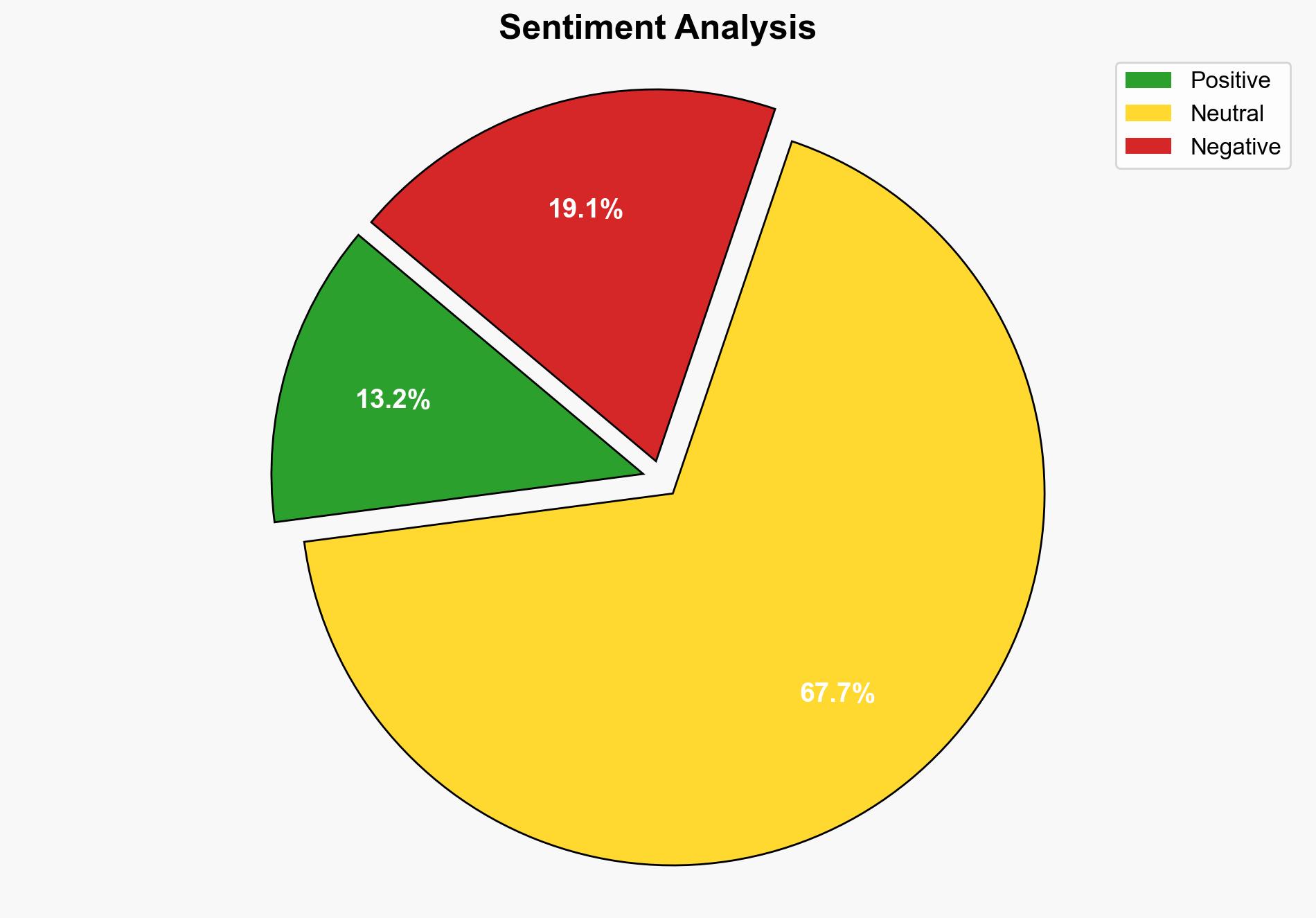
The most supported hypothesis is that the scam emails targeting Afghan data leak victims are orchestrated by opportunistic cybercriminals exploiting the data breach. Confidence level: Moderate. It is recommended to enhance cybersecurity measures and public awareness campaigns to prevent further exploitation.
2. Competing Hypotheses
1. **Opportunistic Cybercrime Hypothesis**: The scam emails are the work of independent cybercriminals who gained access to the leaked data and are exploiting it for financial gain.
2. **State-Sponsored Disinformation Hypothesis**: The scam emails are part of a broader state-sponsored disinformation campaign aimed at undermining trust in the UK Ministry of Defence and its operations.
Using the Analysis of Competing Hypotheses (ACH) technique, the first hypothesis is better supported by the evidence. The lack of sophisticated disinformation elements and the straightforward financial motive align more with typical cybercrime activities.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the data breach was not orchestrated by a state actor, and that the scam emails are not part of a coordinated disinformation campaign.
– **Red Flags**: The rapid emergence of scam emails following the data breach suggests potential insider involvement or advanced cyber capabilities to quickly exploit the leaked data.
– **Blind Spots**: The full extent of the data breach and the number of affected individuals remain unclear, which could obscure the scale of the threat.
4. Implications and Strategic Risks
The scam emails could lead to financial losses and further erode trust in governmental institutions, particularly if perceived as a failure to protect sensitive data. There is a risk of cascading threats if other actors exploit the breach for different purposes, such as identity theft or further phishing attacks. Geopolitically, if the breach is perceived as mishandled, it could strain UK-Afghan relations and impact ongoing relocation efforts.
5. Recommendations and Outlook
- Enhance cybersecurity protocols to prevent future breaches and monitor for signs of insider threats.
- Launch a public awareness campaign to educate potential victims about the scam and how to protect themselves.
- Conduct a thorough investigation to determine the breach’s origin and scope.
- Scenario Projections:
- Best Case: Quick containment of the scam, minimal financial impact, and restored public trust.
- Worst Case: Widespread exploitation of leaked data leading to significant financial and reputational damage.
- Most Likely: Continued attempts at phishing with moderate success, requiring ongoing vigilance and response.
6. Key Individuals and Entities
– Adnan Malik, head of data protection at Baring Law, involved in organizing group action against the Ministry of Defence.
– The Ministry of Defence, implicated in the data breach and subsequent handling of the situation.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus