Akira Ransomware Hits SonicWall VPNs Deploys Drivers to Bypass Security – HackRead
Published on: 2025-08-06
Intelligence Report: Akira Ransomware Hits SonicWall VPNs Deploys Drivers to Bypass Security – HackRead
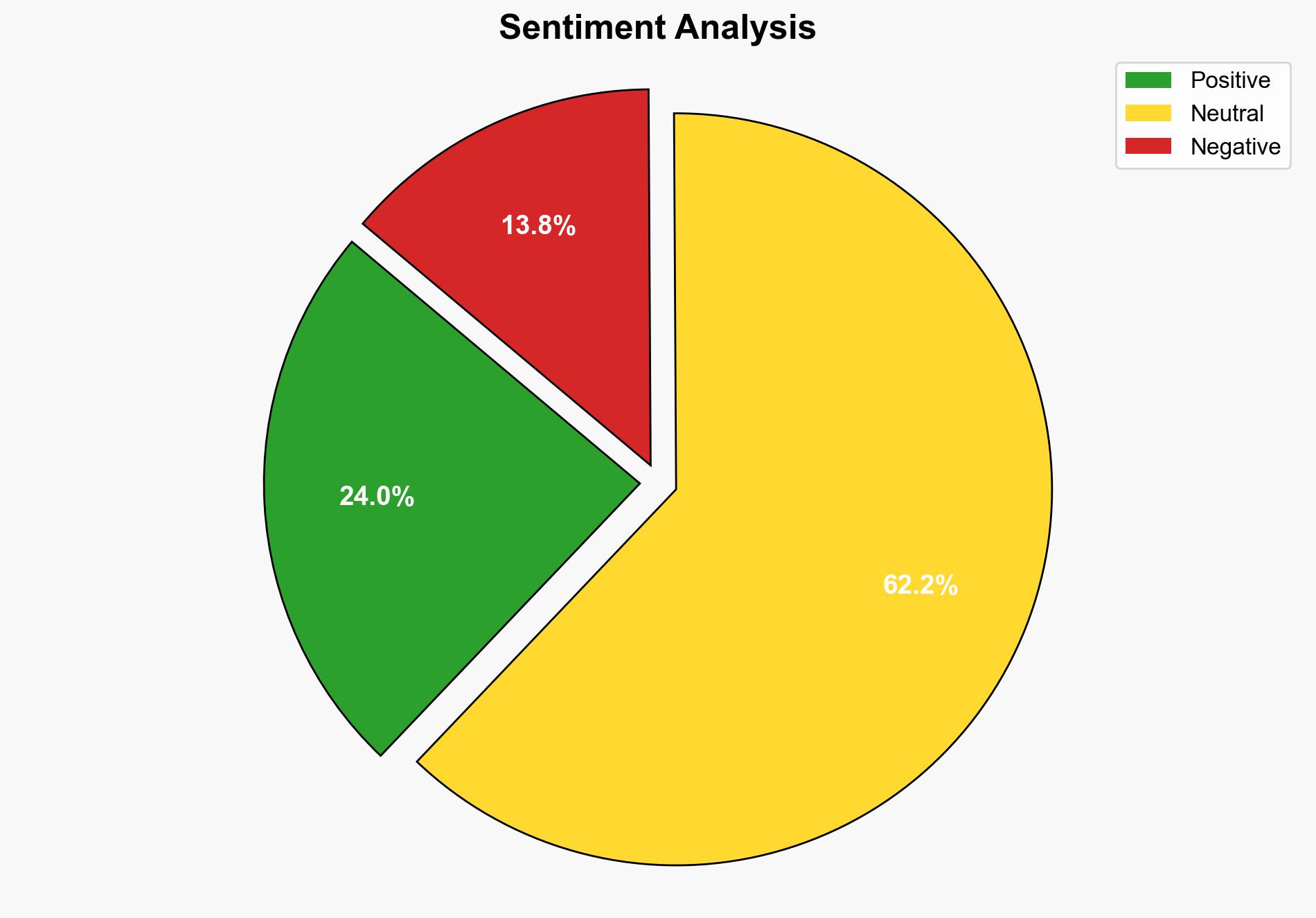
1. BLUF (Bottom Line Up Front)
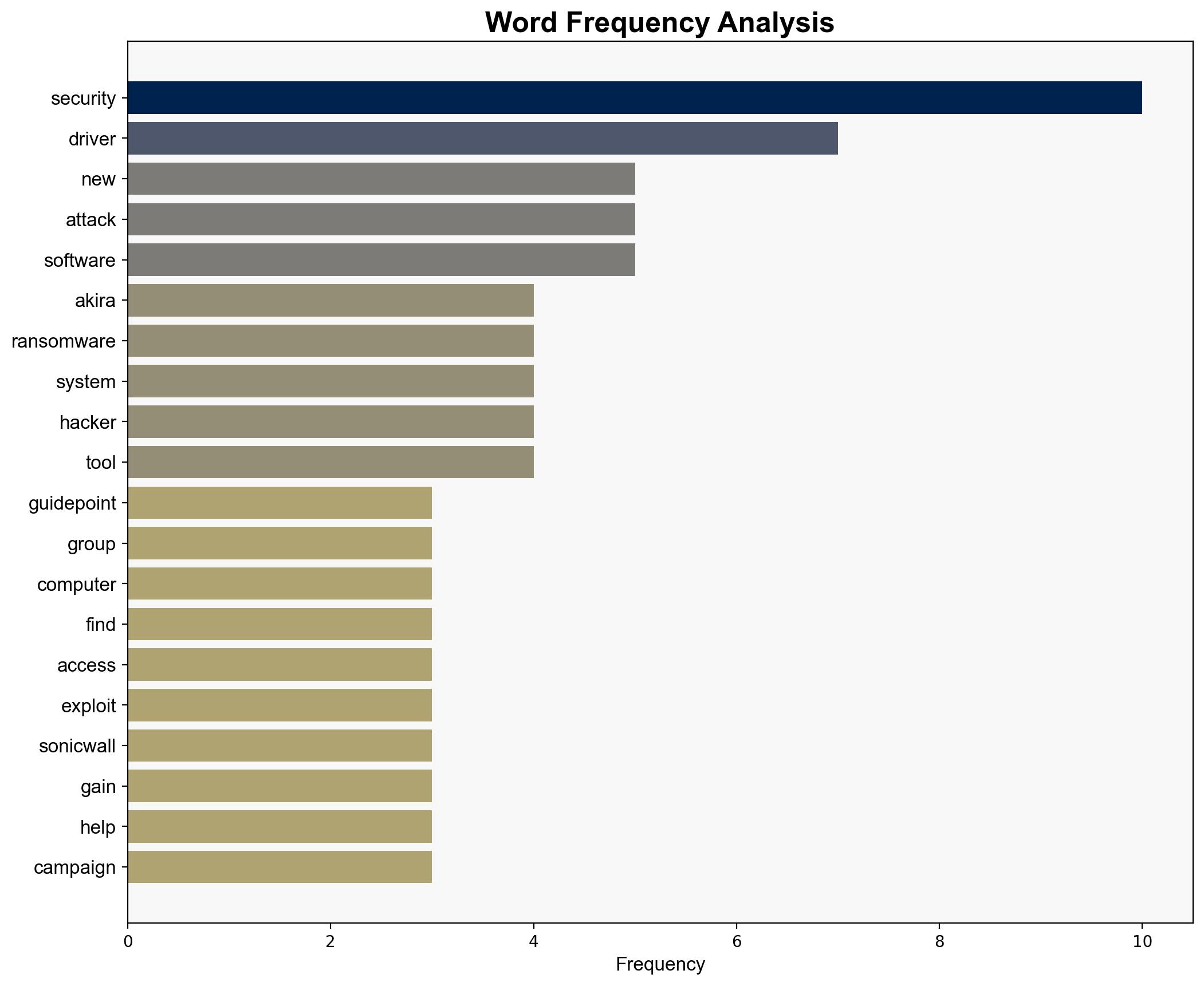
The Akira ransomware group has developed sophisticated methods to exploit vulnerabilities in SonicWall VPNs, using drivers to disable security tools and facilitate ransomware deployment. The most supported hypothesis is that Akira is leveraging these techniques to target corporate networks with insufficient security measures. Confidence Level: High. Recommended action includes immediate patching of known vulnerabilities and enhanced monitoring for unauthorized driver installations.
2. Competing Hypotheses
Hypothesis 1: Akira ransomware group is primarily targeting SonicWall VPNs due to a specific vulnerability that provides easy access and control over corporate networks. This hypothesis is supported by the repeated exploitation of SonicWall VPNs and the use of drivers to bypass security measures.
Hypothesis 2: Akira’s activities are part of a broader strategy targeting multiple VPN products, with SonicWall being one of several exploited due to its prevalence in corporate environments. This hypothesis considers the group’s past targeting of Cisco VPN products and suggests a pattern of exploiting widely used technologies.
Using ACH 2.0, Hypothesis 1 is better supported due to the specificity of the attacks on SonicWall VPNs and the detailed method of using drivers to disable security tools, indicating a focused campaign rather than a broad-based strategy.
3. Key Assumptions and Red Flags
Assumptions include the belief that SonicWall VPNs have a unique vulnerability that Akira can exploit more effectively than other products. A red flag is the lack of detailed information on how the vulnerability was initially discovered and whether similar vulnerabilities exist in other VPN products. The possibility of deception exists if Akira is using SonicWall as a decoy while targeting other systems.
4. Implications and Strategic Risks
The exploitation of SonicWall VPNs by Akira could lead to significant data breaches and operational disruptions in affected organizations, particularly in industries like education, healthcare, and manufacturing. There is a risk of cascading threats if other cybercriminal groups adopt similar techniques. Geopolitically, such attacks could strain relations between affected countries and those perceived to harbor cybercriminals.
5. Recommendations and Outlook
- Immediate patching of SonicWall VPN vulnerabilities and implementation of multi-factor authentication (MFA).
- Enhanced monitoring for unauthorized driver installations using YARA rules.
- Scenario-based projections:
- Best Case: Rapid patch deployment and increased vigilance prevent further breaches.
- Worst Case: Failure to address vulnerabilities leads to widespread ransomware attacks across multiple sectors.
- Most Likely: Continued targeting of SonicWall VPNs with sporadic success in breaching networks.
6. Key Individuals and Entities
No specific individuals are named in the report. The entities involved include the Akira ransomware group, SonicWall, and GuidePoint Security.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus